Answers to Three FAQs About the New-and-Improved Cloud Configuration Assessment Remediation Content in InsightVM


Organizations operating in a cloud environment like Amazon Web Services (AWS) face additional security risk challenges that they need to manage. Cloud environments introduce new risks in the form of misconfigured assets, which could be anything from a publicly accessible cloud storage bucket to a virtual machine that doesn’t have logging enabled.
To help you detect misconfigurations, InsightVM, Rapid7’s vulnerability management tool, includes Cloud Configuration Assessment. It lets you monitor all your AWS accounts and ensure that the assets in those accounts are configured to follow industry standards like the CIS AWS Foundations Benchmark. With Cloud Configuration Assessment, you can easily see what misconfigurations exist and share that information with the teams in charge of your cloud environment to ensure the issues are quickly addressed.
In an ever-evolving cloud environment, having access to readily available remediation actions is critical to keeping your cloud infrastructure secure. Rapid7 recently released new-and-improved remediation content for a full library of rule checks that we use to assess your AWS environment. For each rule assessment, we now provide Python scripts that can be used to remediate noncompliant resources in a timely manner.
Let’s get to know this new feature a little better by answering some frequently asked questions.
Remediating cloud misconfigurations with InsightVM?
Remediation content provides fixes needed for any cloud resource that is misconfigured or in violation of a rule. Rapid7 InsightVM provides several remediation options for you to choose from—any of these options will remediate the noncompliant resource for the specific rule. Each remediation option is a script using Boto3, Amazon Web Services (AWS) Software Development Kit (SDK) for Python. The scripts are out-of-the-box remediations for vulnerabilities or misconfigurations in your AWS environment.
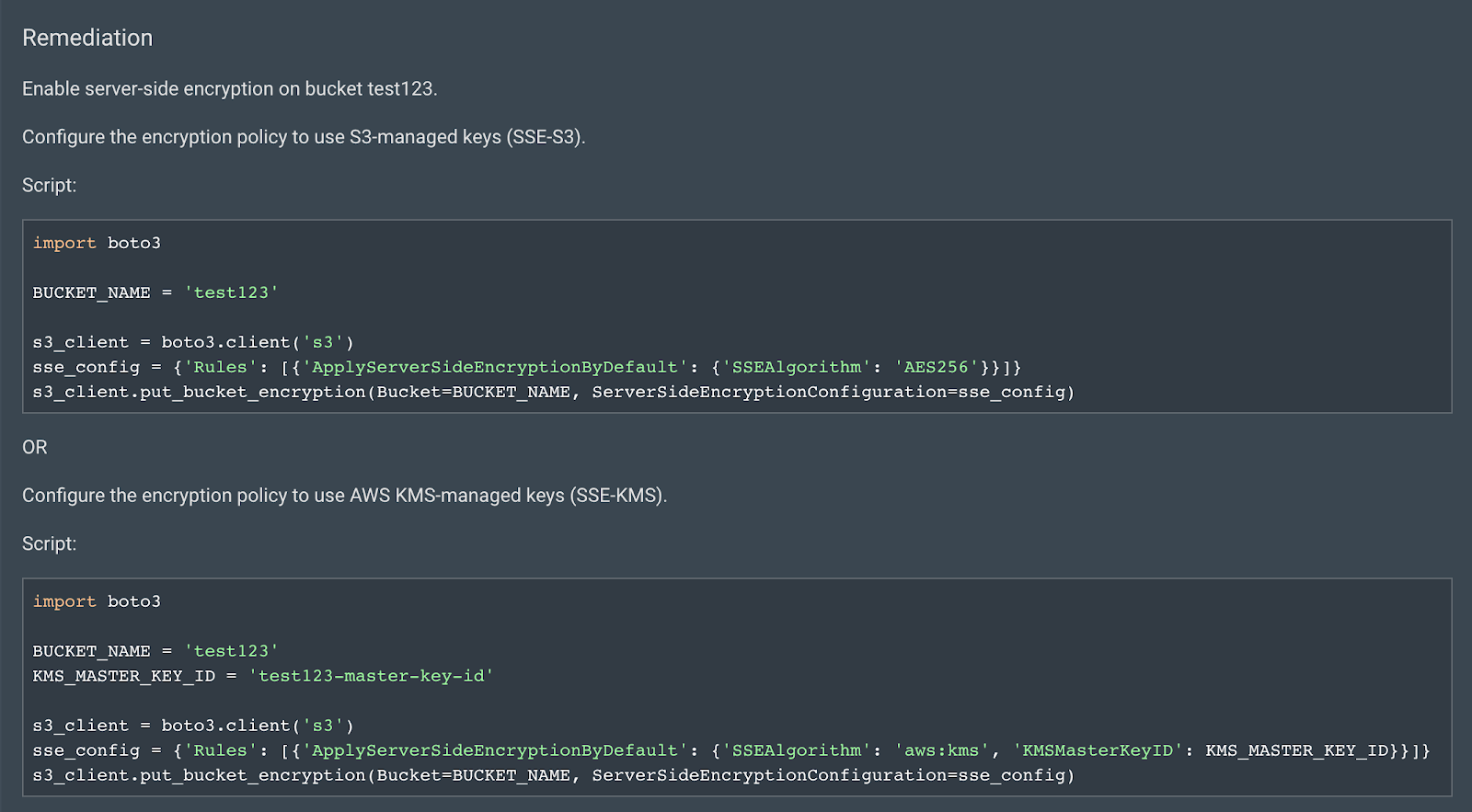
For example, one of the rules we check against AWS S3 buckets is whether server-side encryption (SSE) is disabled. Server-side encryption (SSE) of S3 buckets encrypts and protects data at rest. Best security practices recommend ensuring the storage of potentially sensitive data is encrypted at rest. An S3 bucket not in compliance with this rule would have two remediation options:
- Configure the encryption policy to use S3-managed keys (SSE-S3)
- Configure the encryption policy to use AWS KMS-managed keys (SSE-KMS)
Both options remediate the noncompliant S3 bucket for the specific rule, as shown in the screenshot below:

Why did Rapid7 release this new remediation content?
As we continue to improve the Cloud Configuration Assessment feature in InsightVM, we want to create a more comprehensive experience in terms of possible courses of remediation action once misconfigurations are discovered. Now with hundreds of our remediation scripts, we can help secure your cloud infrastructure through the entire vulnerability lifecycle.
How do I assess and remediate cloud misconfigurations with InsightVM?
In order to use this feature in InsightVM, you need Python 3.x. installed and AWS credentials configured in your local environment (with the AWS CLI configured, this is already taken care of). Remediating vulnerabilities in your cloud infrastructure is as easy as copying the remediation script of your choice, pasting it into your favorite text editor, and executing it.
Head over to Rapid7 InsightVM’s help documentation for information on getting started with Cloud Configuration Assessment.


![RansomHouse Ransomware Victim: STERCH - INTERNATIONAL s[.]r[.]o[.] 12 ransomhouse 1](https://www.redpacketsecurity.com/wp-content/uploads/2023/03/ransomhouse-1-300x153.png)