Application Security Takes Center Stage in this Year’s Verizon Data Breach Investigations Report


The latest Verizon Data Breach Investigations Report (DBIR) was released in May, and we’re still unpacking all the golden nuggets inside! This annual report ranks the most common ways organizations get breached, leading to the disclosure of information. It also reports on the most common types of incidents, which are events that compromise the integrity of data for a company.
As we combed through this year’s report, a similar but mounting theme arose: web application security. Over the past few years, web applications have become the biggest target for attacks, as they’re an easy way for hackers to gain access to valuable information. This year, that theme only continued to resonate.
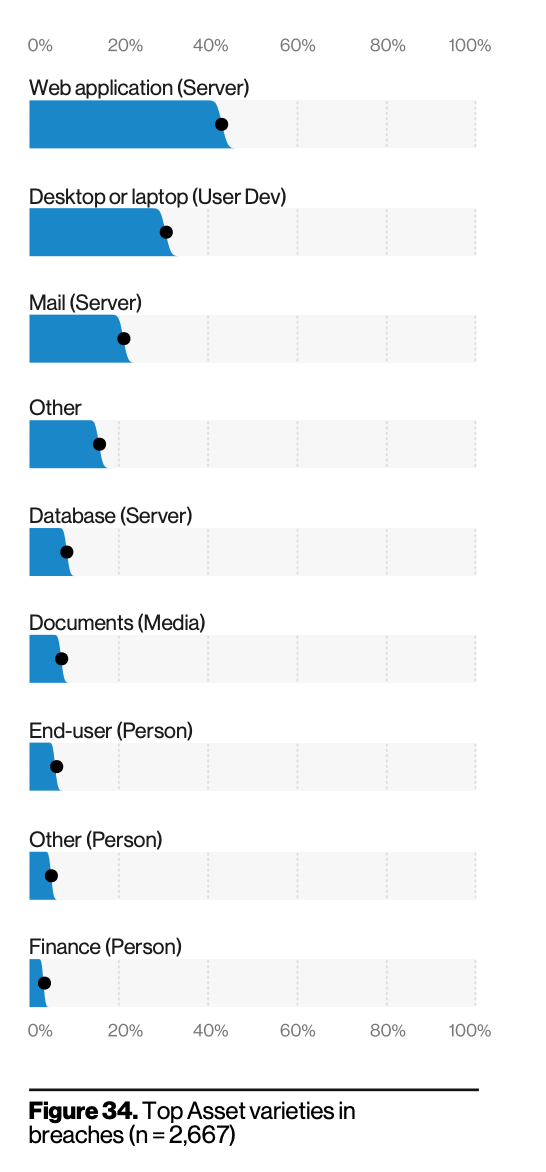

If you collect payments such as credit card data or deal with PHI data in the healthcare sector, web apps can be a gold mine for adversaries. So long as valuable data is held in the cloud, attackers will be at the ready, and this trend unfortunately isn’t going away anytime soon.
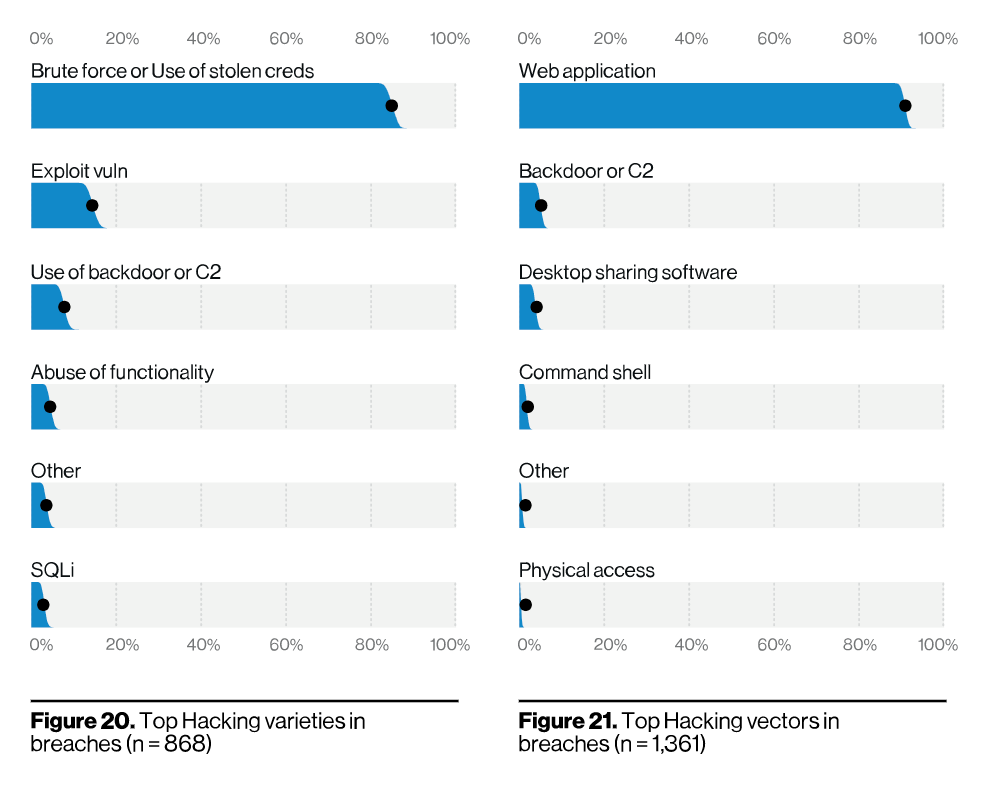

As the figures above show, these include attacks against exploiting code-based vulnerabilities as well as attacks against authentication, such as hacking and stolen credentials. The report also reported that SQL injections and PHP injections are the most commonly exploited vulnerabilities, which makes sense considering these attacks are quick and easy ways of extracting profit from an exposed system.
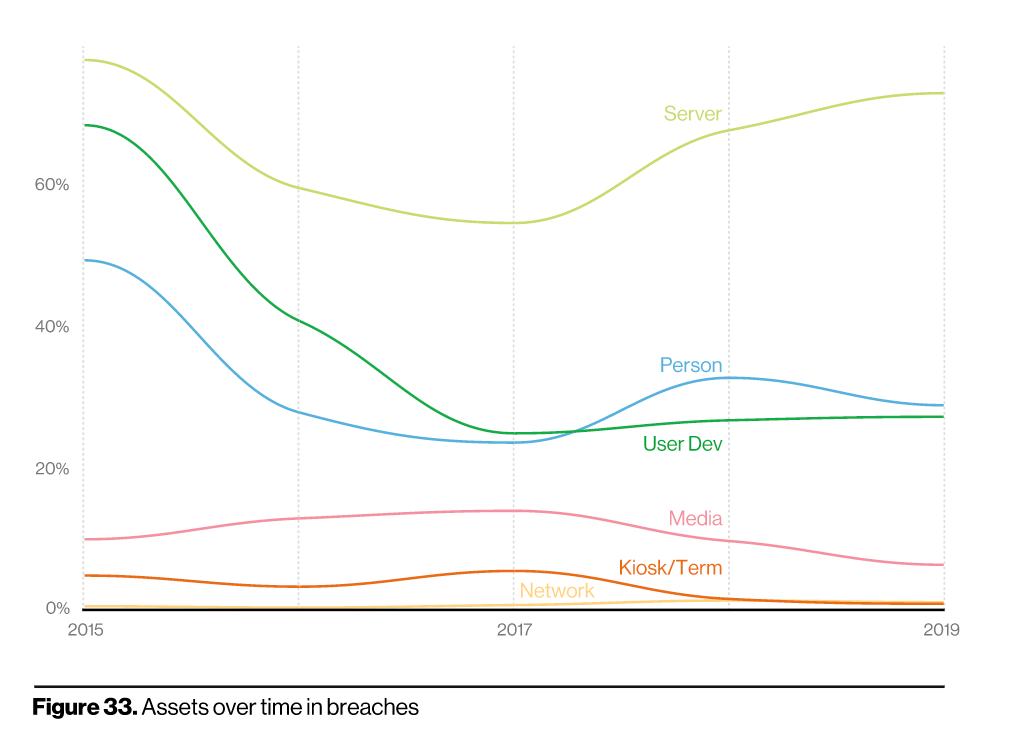

Additionally, the DBIR reported that web applications were the top attack patterns for small organizations in particular. However, regardless of your organization’s size, it’s important to invest in application security tools that can help protect you from the exploitable vulnerabilities mentioned above.
Lessons we can learn from the 2020 DBIR report
So, what can we learn from this, and how can companies do better this year? If it’s not already abundantly clear, we need to better secure web applications. As always, the DBIR recommends following the CIS controls, which are a prioritized set of cybersecurity guidelines. In this report, they placed continuous vulnerability management at the top of the list of things to implement to address this year’s findings. Continuous vulnerability risk management is a method for finding and remediating things like code-based vulnerabilities, such as the ones found in web applications, that are being exploited. It can also discover key misconfigurations that can leave you vulnerable.
There are three key elements of vulnerability risk management, specifically at the application layer:
- Testing. This helps to find flaws within your web apps. So long as apps are going to be attacked, you should simultaneously be testing them. This allows you to find vulnerabilities earlier and remediate them. Solutions like InsightAppSec are great for testing pre-production applications with its industry-leading DAST technology.
- Monitoring. While testing is important to finding and remediating vulnerabilities earlier in the SDLC, monitoring is the other half of the puzzle, as it enables you to actually see how apps are being attacked in real time. Solutions such as tCell, a next-gen WAF and RASP tool, are great for in-production monitoring and protection of applications.
- Prevention. The underlying goal of a testing and monitoring approach to application security is to ultimately reduce risk and prevent vulnerabilities from being exploited by either mitigating or remediating flaws.
Rapid7’s Insight Cloud offers all three of these capabilities, with robust application security solutions including InsightAppSec, tCell, and managed and professional services to assist customers with the ultimate goal of reducing risk.
You can learn more about InsightAppSec here and about tCell here, and can even request an on-demand demo, if you’re interested in seeing InsightAppSec in action.
Already an InsightAppSec customer? Share your experience with InsightAppSec with your security peers by submitting a Gartner Peer Insights review today.
Get Started
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


