Coordinated Twitter attack rakes in 100 grand
“I’m feeling generous because of Covid-19. I’ll double any BTC payment sent to my BTC address for the next hour. Good luck, and stay safe out there!”
This and similar Tweets asking readers to send US$1,000 to a Bitcoin address with the promise of a double return payment went out yesterday.
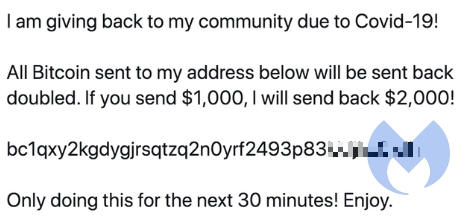

Too good to be true?
Once again, social engineering has been demonstrated to be a powerful attack vector. Who would fall for such a ruse, you may ask? Looking at the traffic on said Bitcoin address, more than 100 people were duped.
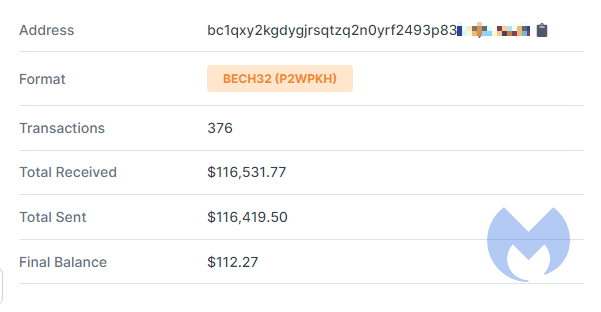

The victims that sent Bitcoin to this address probably do not feel so good about themselves right now. But in their defense, some of the accounts that were Tweeting out these messages were trusted figures with verified Twitter accounts. To name a few: Elon Musk, Bill Gates, Barack Obama, Kanye West, Warren Buffet, Jeff Bezos, Joe Biden, and many other high-profile accounts were taken over.
What happened?
The official Twitter Support account states that their investigation is still ongoing, but it has revealed that threat actors gained unauthorized access and used it to take control of many highly-visible (including verified) accounts and Tweet on their behalf.
From other sources we learned that the threat actors managed to use social engineering on a Twitter employee to gain access to their control panel. Through the employee panel, they were able to change associated email addresses for many accounts to addresses under their control. They then used that as a means to reset the password for the account and disable 2FA.
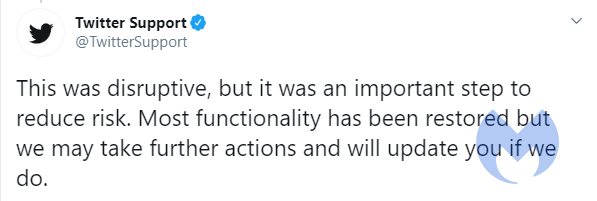
During the ongoing Twitter storm of misleading Tweets, Twitter Support locked down the affected accounts and removed Tweets posted by the attackers as fast as they could find them. They also limited functionality for a much larger group of accounts, like all verified accounts (even those with no evidence of being compromised) during the investigation.

What should I do?
If you think you might be the owner of an affected account, you should:
- Not feel bad because this one was not on you
- Check if the address listed under email is yours
- Reset and change your password
- Enable 2FA
All these settings can be found when you are logged in on Twitter under More > Settings and privacy. Another setting that is worth considering is the Password reset protect which can be found under Additional password protection. Even though it probably would not have helped against this attack, it might help if you get a test or email when someone requests a password reset on your account. In this case, I’m pretty sure the employee panel would have allowed the attackers to disable that option as well.
Can victims retrieve Bitcoin?
Unfortunately, it is virtually impossible to get back stolen Bitcoin from the attackers. They are probably laundering the money right now. They will use Bitcoin mixing services to hide where the Bitcoin came from and Bitcoin exchange services to anonymously convert Bitcoin into spendable money.
The best move now is to scrutinize each and every request for donations, payments, or services—whether you know the person or not. Social engineering is a trick as old as time, and the reason it’s still so popular is that it still works.
Stay vigilant and stay safe, everyone!
The post Coordinated Twitter attack rakes in 100 grand appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



![CACTUS Ransomware Victim: https://www[.]ghimli[.]com / 8 image](https://www.redpacketsecurity.com/wp-content/uploads/2023/09/image-300x291.png)


