CorsMe – Cross Origin Resource Sharing MisConfiguration Scanner

A Misconfiguration Scanner cors misconfiguration scanner tool based on golang with speed and precision in mind !
Misconfiguration type this scanner can check for
- Reflect Origin checks
- Prefix Match
- Suffix Match
- Not Esacped Dots
- Null
- ThirdParties (Like => github.io, repl.it etc.)
- Taken from Chenjj’s github repo
- SpecialChars (Like => “}”,”(“, etc.)
- See more in Advanced CORS Exploitation Techniques
How to Install
$ go get -u github.com/shivangx01b/CorsMeUsage
Single Url
echo "https://example.com" | ./Corsme Multiple Url
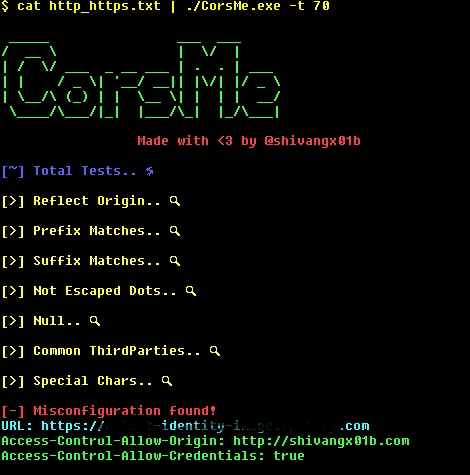
cat http_https.txt | ./CorsMe -t 70 Allow wildcard .. Now if Access-Control-Allow-Origin is * it will be printed
cat http_https.txt | ./CorsMe -t 70 --wildcard Add header if required
cat http_https.txt | ./CorsMe -t 70 -wildcard -header "Cookie: Session=12cbcx...." Tip
cat subdomains.txt | ./httprobe -c 70 -p 80,443,8080,8081,8089 | tee http_https.txt cat http_https.txt | ./CorsMe -t 70 Screenshot

Note:
- Scanner stores the error results as “error_requests.txt”… which contains hosts which cannot be requested
Idea for making this tools are taken from :
CORScanner
Corsy
cors-blimey
Download CorsMe
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![CACTUS Ransomware Victim: https://www[.]xdconnects[.]com/ 5 image](https://www.redpacketsecurity.com/wp-content/uploads/2023/09/image-300x291.png)



