Dubious downloads: How to check if a website and its files are malicious
A significant amount of malware infections and potentially unwanted program (PUP) irritants are the result of downloads from unreliable sources. There are a multitude of websites that specialize in distributing malicious payloads by offering them up as something legitimate or by bundling the desired installer with additional programs.
In November 2019, we learned that Intel removed old drivers, BIOS updates, and other legacy software from their site. While this software relates to products released in the last century and early years of the 2000s, many users still rely on old Intel products and have been left scrambling for specific downloads.
Users that follow older links to certain drivers and updates will find this instead:

Following the links to search the site or the download center only leads users around in circles—those downloads are gone. While some might argue that it is Intel’s right to remove drivers and updates after a decade, others understand that whenever legacy software is abandoned, a security nightmare ensues.
When users can no longer download files from official sources, desperate people will roam the Internet for a place where they can find the file they need. And what they usually find instead are malicious websites and downloads.
Malvertising using popular downloads
Habitually, threat actors find out which search terms are gaining in popularity as users seek out terminated software downloads and try to lure searchers to their site. They will use SEO techniques to rank high in the search results or may even spend some dollars to show up in the sponsored results for certain keywords. They can hide their malware in malvertising in the form of downloads or even drive-by-downloads, in which users needn’t install a single file, only visit the site, to be infected.
After all, a victim that is desperately looking for a file he needs to get a system up and running again is really all a malware peddler could wish for. All they have to do is make the user of the site believe they have found the file they are looking for. Once they are convinced, they will download and install the alleged driver all by themselves.
All the threat actor has to do is upload the malware under some convincing filename and attract visitors to the site. This is basically the same modus operandi that you will find in use when people go looking for cracks and keygens.
So, what can users do to avoid falling victim to such a scam? A couple of things, as it happens. We will provide you with some checks you can do before you visit the download site. And there are some checks you can perform before you run the downloaded file, too.
Checks you can perform to assess the website
When you have found a site that offers a file for download, there are a few actions you can take to check whether the site is trustworthy. They are:
- Check for the green padlock
- Read third-party reviews of the website
- Use a trusted antivirus or browser extension, such as Browser Guard
Checking for the presence of the green padlock is a good start to ensure a site has purchased a security certificate, but it’s also not a guarantee that the website is safe. SSL certificates are cheap, and your neighborhood cybercriminal knows where to get them practically for free. If you click on the green padlock, you can find out who issued the certificate and for which site.
Recommended reading: Explained: security certificates
There are many websites that offer reviews of download sites and domains, and while many of these sites are reputable, they tend to fall a little bit behind in adding Internet newcomers. Our cybercriminal can afford to dump a domain like a hot potato once it has racked up too many bad reviews, then purchase a new site from which to run his scheme.
In short, you can trust reviews about sites that have been around for a while, but the lack of reviews for a site could mean they only started or they may be up to no good.
Some cybercriminals are brilliant programmers. Most are not. But all the successful ones have one skill in common: They are well-versed in tricking people. So, don’t accept a website as trustworthy just because it features logos of other trustworthy companies on its pages. Logo images are easily found in online searches, and they could be planted on the site for exactly that reason: to gain the visitors’ trust. Logos could also be stolen, unauthorized, or handed out for different reasons than you might expect.
Some browsers and some free applications warn you about shady sites—especially sites they know to be the home of malware and scammers. Malwarebytes Browser Guard, for example, can be installed on Chrome and Firefox, adding to the browsers’ own capabilities to recognize malicious domains and sites.
How do I filter possible malware from the downloaded files
There are some methods you can use to weed
out the bad boys in your download folder:
- Compare the checksum to the original file
- Look at the file’s digital signature
- Run a malware scan
A checksum is a sequence of numbers and
letters used to check data for errors. If you know the checksum of the original
file, you can compare it to the one you have downloaded. Windows,
macOS, and Linux have built-in options to calculate the checksum of a file.
The digital signature of a Windows
executable file (a file with an .exe extension) can be verified after the file
has been downloaded and saved. In your Downloads folder, right-click the
downloaded .exe file and click Properties. Here you can click on the Digital
Signatures tab to check whether the downloaded file is signed by the expected
party.
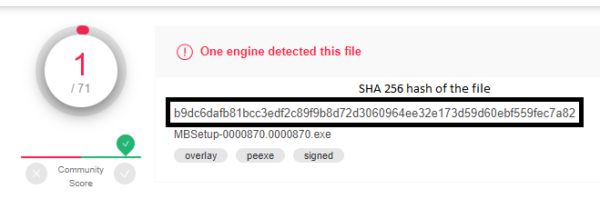
Finally, use your anti-malware scanner to double-check that you are not downloading an infected file. You can also use online scanners like VirusTotal, which will also provide you with a SHA-256 hash for the file and save you the trouble of calculating a checksum.

Much ado about what?
All this may seem like a lot of work to those who habitually download files without a worry in the world. However, even the most practiced downloader eventually has their moment of truth—when that downloaded file wrecks their computer or all those bundled applications are harder to remove than expected.
People who download all the time have better instincts about which sites to trust or not, but that doesn’t mean they can’t be fooled. From experience, they know the sites that offer malware under a different filename from the sites that offer clean files. But sometimes, we reach for the shiny golden delicious and, once we take a bite, discover it has a worm.
We don’t all have the stomach or the knowledge to clean an infected computer. And some systems are not ours to put at risk.
Even if you follow all these pointers to the letter, it is still riskier to download files from unknown sites than it is to download from the company that made them. So we would like to urge companies to keep their “old files” available on their own site, even if the number of downloads has dwindled.
Stay safe, everyone!
The post Dubious downloads: How to check if a website and its files are malicious appeared first on Malwarebytes Labs.

