It’s business as usual for REvil ransomware
After the FBS arrested 14 of its members in January, and a subsequent lull in action, the REvil ransomware gang appears to be back. We say “appears” because it’s still unclear whether the group’s operations have indeed restarted.
To the trained eye, REvil’s movements seem out of sorts. When REvil’s old Tor infrastructure came back to life in April, it was modified to redirect visitors to URLs owned by a new ransomware group. The sites the nodes point to looked nothing like REvil’s. And its data leak blog is prepopulated with new ransomware victims and old REvil victims.
“And they are recruiting,” added Malwarebytes Threat Intelligence Analyst Marcelo Rivero.
REvil ransomware: a brief look back
When the REvil ransomware gang began its operations in 2019, it started strong. REvil, also known as Sodinokibi or Sodin, was the new RaaS (ransomware as a service) of the criminal underground, filling the hole GandCrab left behind.
Like any “big-game hunting” operator, REvil only targets high-earning organizations. The logic behind this is that such targets are presumed to pay up, even a high ransom. They presumed correct.
2021 was the ransomware gang’s last year of activity. REvil attacked JBS, one of America’s largest meat and poultry processors, in June. JBS underwent recovery proceedings immediately after the attack, unlike other ransomware victims. It was revealed months after that the company paid REvil to the tune of $11M (£7.8M).
In July, REvil attacked Kaseya, the company behind Kaseya VSA, a popular remote monitoring and management software. The ransomware gang asked for a whopping $70M ransom, but the company didn’t pay. Instead, it used a decryption key “from a third party” to decrypt all its encrypted files.
Many suspected that something was up. Kaseya could not give any more details, as it was bound by an NDA (non-disclosure agreement), but the ransomware gang claimed that the decryptor was leaked by one of its operators.
Is REvil really back?
A ransomware sample is needed to dispel speculations on whether REvil has re-emerged or not. Sure enough, cybersecurity researcher Jakub Kroustek (@JakubKroustek) discovered one recently.
Multiple security researchers who looked into the sample said they noticed a few changes to the code based on old REvil ransomware code. The most notable changes in the encryptor are the version, the new accs configuration option, and the campaign and affiliate identifiers.
In an interview with BleepingComputer, Advanced Intel CEO Vitali Kremez said he believes this option “is used to prevent encryption on other devices that do not contain the specified accounts and Windows domains, allowing for highly targeted attacks.”
When asked about his thoughts, Rivero said, “I think this REvil sample is just a test file because it doesn’t encrypt.”
On top of this, the sample also adds a random extension name to affected files and creates a ransom note—both as text and HTML files—identical to old REvil’s. The web version of the ransom note links users back to new paid Tor sites and the new data leak blog.
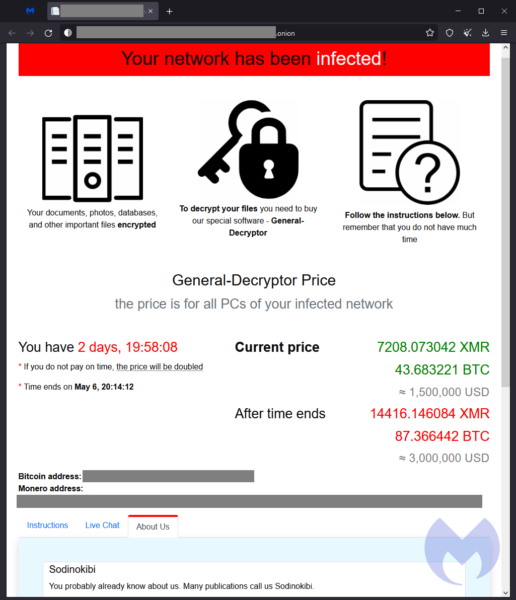
Malwarebytes detects this new REvil sample as Sodinokibi.Ransom.Encrypt.DDS.
What should previous victims do now?
When REvil’s servers disappeared on an early Tuesday morning in July 2021, current victims of the ransomware gang were left stumped, not knowing what to do next. They were stuck in mid-negotiations, fearing they might never hear from the gang again, leaving their essential files encrypted forever.
With REvil back and the new operators apparently inheriting former victims of the old ransomware gang, what does this mean for victims?
It’s almost a year since REvil’s infrastructure went dark, and victim companies may have already moved on or sought help from law enforcement. Either way, REvil might one day come knocking at their digital doors to pick up where it left off.
The post It’s business as usual for REvil ransomware appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.





