Malspam banks on Kaseya ransomware attack
The Malwarebytes Threat Intelligence Team recently found a malicious spam campaign making the rounds and banking on the ransomware attack that forced Kaseya to shut down its VSA service.
This is a classic example of an opportunistic attack conducted by (potentially) another threat actor/group off the back of another threat actor/group’s attack. With Kaseya being a big name in the MSP world and the company attempting to take their VSA SaaS platform off the ground, post-attack, it’s the perfect time and opportunity to also capitalize on organizations who are eagerly waiting for the hotfix that REvil exploited in the first place so they can get back to business as quickly as possible.
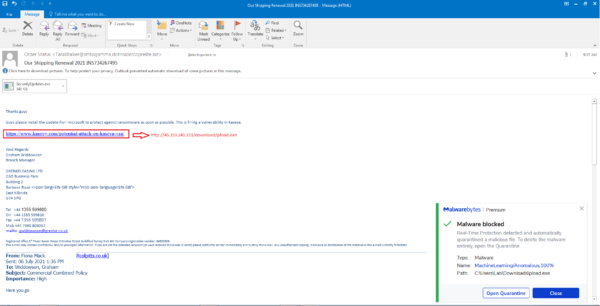

The email that Malwarebytes found contains both a malicious link and attachment purporting to have come from Microsoft. The link leads to the download of a file called ploader.exe while the attachment, named SecurityUpdate.exe. Both of these are Cobalt Strike payloads.
The email reads in part:
“Guys please install the update from microsoft to protect against ransomware as soon as possible. This is fixing a vulnerability in Kaseya.”
The Threat Intelligence Team at Malwarebytes also noted that the location where the payload is hosted is the same IP address used in another malspam campaign that was pushing Dridex, a known information stealer. In the past, threat actors behind Dridex campaigns were also observed using Cobalt Strike.
If you may recall, Cobalt Strike is a legitimate software that bills itself as an “adversary simulation software.” Ransomware actors, in particular, are known to abuse legitimate software and make it part of their overall malicious attack against target organizations during their big game hunting (BGH) campaigns.
If you’re a Kaseya client, you can get first-hand updates on the VSA incident here.
It goes without saying that any and all companies affected by the Kaseya ransomware attack should only get patches straight from their vendor. Links and/or attachments sent over your way, even from a trusted colleague, should be suspect until you have confirmed with your vendor of the availability of a patch and where or how to get it. Realize that this is not the first time that threat opportunists bank on attacks like what Kaseya experienced. Opportunists will show no mercy in targeting cyber attack victims multiple times as long as they get something out of it.
In this case, with the use of Cobalt Strike, these threat actors intend to also gain access to your already-compromised system possibly for further reconnaissance or to conduct a local, follow up attack.
Stay safe!
The post Malspam banks on Kaseya ransomware attack appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


