Purple Fox rootkit now bundled with Telegram installer
The Purple Fox rootkit is being spread as an installer for the popular Telegram instant messaging app for Windows, according to researchers.
It’s not clear how the installer in this case was distributed, although it seems like at least some were delivered via email. Common distribution methods for this type of installer are phishing campaigns, forum spam, YouTube posts and comments, as well as untrustworthy software download sites. We’ve also seen the same malicious downloader in a combination with a WhatsApp for Windows installer.
But what makes the newly found Telegram installer special is the fact that the malicious part of the install is done separately in several small files. This makes the malware harder to detect and makes it easier for the malware authors to replace parts that have a high detection rate.
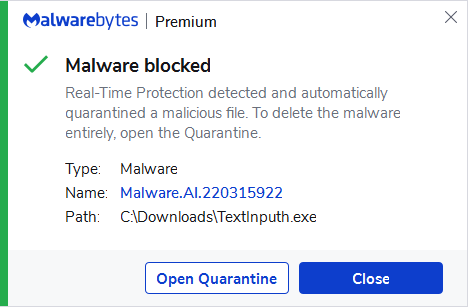
It starts with an installer called “Telegram Desktop.exe” which is an AutoIT script that drops a legitimate Telegram installer and a malicious downloader called “TextInputh.exe”. The legitimate Telegram installer is not executed, but the malicious downloader is immediately used as a downloader for the next stage of the attack.
It downloads and executes more files, which get deleted after they have done their work. Then User Account Control (UAC) is disabled, specific antivirus initiations are blocked, and information about security tools on the affected system are gathered and sent to a hardcoded command and control (C2) address.
The malware checks specifically for the presence of 360 AV software and will shut it down and block initiation.
The final stage of the infection requires a reboot for the new registry settings to take effect, including the disabled UAC. The disabled UAC setting allows the malware to download and deploy the Purple Fox rootkit.
Purple Fox background
Purple Fox is the name given to a malware family that has been in constant development ever since it was discovered in 2018. Back then it was a relatively simple Trojan that relied on exploit kits and phishing emails to spread. By the end of 2020, however, Purple Fox was using brute force attacks over Server Message Block (SMB), a network protocol that allows Windows computer to share files.
Then, in March 2021, researchers discovered that the Purple Fox malware included a rootkit and was wormable. A rootkit allows the attackers to hide the malware on a machine and make it difficult to detect and remove. Wormable malware is capable of spreading from one vulnerable computer to another automatically.
The Purple Fox infrastructure consists mostly of exploited servers that are used to host payloads, act as C2 servers, or serve as worm nodes. This makes it harder to track down the threat actors, but it also makes the infrastructure vulnerable if key servers get cleaned up by their rightful owners.
In September 2021, researchers found a new backdoor written in .NET which is believed to be associated with PurpleFox. This backdoor leverages WebSocket to communicate with its C2 servers, resulting in a more robust and secure means of communication. WebSocket is a communication protocol that allows streams of data to be exchanged between a client and server over a single TCP connection.
Mitigation
The most important advice to avoid this kind of infection is to download software only from trusted sources. Sometimes easier said than done, but trust me, it pays off.
Malwarebytes protects against and detects the malicious downloader by using the Artificial Intelligence module of its real-time protection.

IOCs
A full list of IOCs can be found on the Minerva blog, but we have listed the most important ones below:
Folders:
C:UsersPublicVideos1640618495
C:Users{username}AppDataLocalTempTextInputh
Files:
Telegram Desktop.exe
TextInputh.exe
1.rar
360.tct (which gets renamed to 360.dll)
rundll3222.exe
svchost.txt
Calldriver.exe
Driver.sys
bmd.txt
dll.dll
kill.bat
speedmem2.hg
Registry:
HKEY_LOCAL_MACHINESYSTEMSelectMarkTime
IPs:
144.48.243.79
193.164.223.77
Hashes:
41769d751fa735f253e96a02d0cccadfec8c7298666a4caa5c9f90aaa826ecd1
bae1270981c0a2d595677a7a1fefe8087b07ffea061571d97b5cd4c0e3edb6e0
Stay safe, everyone!
The post Purple Fox rootkit now bundled with Telegram installer appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


