The Glupteba botnet is back researchers reported a surge in infection worldwide after Google disrupted its operation in
The Glupteba botnet is back, researchers reported a surge in infection worldwide after Google disrupted its operation in 2021.
In December 2021, Google announced it has taken down the infrastructure operated by the Glupteba botnet, it also sued Russian nationals Dmitry Starovikov and Alexander Filippov for creating and operating the botnet.
The blockchain-enabled botnet has been active since at least 2011, researchers estimated that the Glupteba botnet was composed of more than 1 million Windows PCs around the world as of December 2021.
The botnet was involved in stealing users’ credentials and data, mining cryptocurrencies abusing victims’ resources, and setting up proxies to funnel other people’s internet traffic through infected machines and routers.
Botnet operators use to spread the malware via cracked or pirated software and pay-per-install (PPI) schemes.
Now researchers from Nozomi Networks reported that the Glupteba botnet is back, and researchers reported a surge in the number of infections worldwide. Experts noticed a significant increase of malicious bitcoin addresses along with the increase in TOR hidden service being used as C2 servers.
The researchers observed a new campaign that started in June 2022 after the Google lawsuit and is still ongoing.
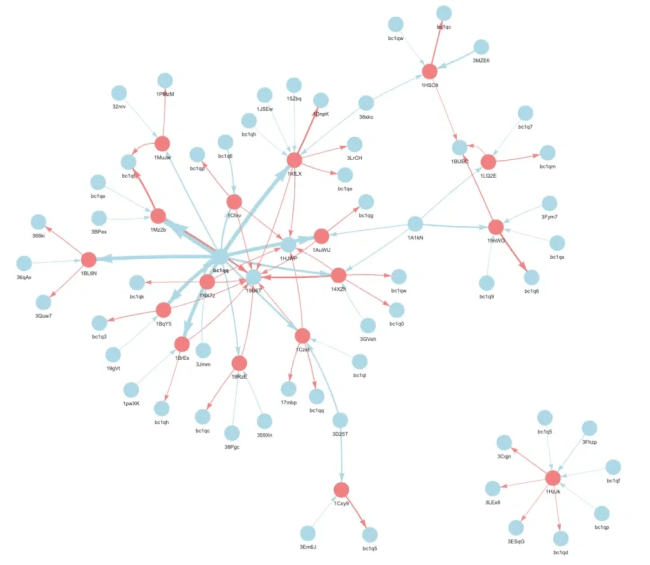
Nozomi analyzed the entire blockchain to discover the C2 domains used by the botnet, the researchers also downloaded over 1500 Glupteba samples from VirusTotal to track the wallet addresses used by the operators.
Researchers believe that at least five different merchants and exchanges were used to fund the Glupteba addresses since 2019. The experts identified 15 Glupteba bitcoin addresses over 4 years, likely involved in four different campaigns
“For this campaign we were not able to find any samples for 3 of the addresses we gathered. We believe these addresses are not made for testing as they distribute some domains found in other Bitcoin addresses for which we found samples.” reads the post published by Nozomi. “In addition, there was a tenfold increase in TOR hidden service being used as C2 servers since the 2021 campaign.”
The experts used passive DNS records to uncover Glupteba domains and hosts and analyzed the latest set of TLS certificates used by the bot to figure out the infrastructure used by the attackers.
One of the addresses had 11 transactions and was used by 1,197 samples, with the last seen activity reported on November 8, 2022.
“Even with Google winning a favorable ruling recently, we hoped it would have inflicted a severe blow to Glupteba operations, but almost a year later we can say it most likely did not. Indeed, it took Glupteba about six months to build a new campaign from scratch and distribute it in the wild, and this time on a much larger scale.” concludes the report. “For defenders and responders, we strongly suggest blocking blockchain-related domains like blockchain.info but also Glupteba known C2 domains in your environment. We also recommend monitoring DNS logs and keeping the antivirus software up to date to help prevent a potential Glupteba infection.”
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below
To keep up to date follow us on the below channels.