Windows MSHTML zero-day actively exploited, mitigations required
Several researchers have independently reported a 0-day remote code execution vulnerability in MSHTML to Microsoft. The reason it was reported by several researchers probably lies in the fact that a limited number of attacks using this vulnerability have been identified, as per Microsoft’s security update.
Microsoft is aware of targeted attacks that attempt to exploit this vulnerability by using specially-crafted Microsoft Office documents.
MSHTML is a software component used to render web pages on Windows. Although it’s most commonly associated with Internet Explorer, it is also used in other software including versions of Skype, Microsoft Outlook, Visual Studio, and others.
Malwarebytes, as shown lower in this article, blocks the related malicious powershell code execution.
CVE-2021-40444
Publicly disclosed computer security flaws are listed in the Common Vulnerabilities and Exposures (CVE) database. Its goal is to make it easier to share data across separate vulnerability capabilities (tools, databases, and services). This one has been assigned the designation CVE-2021-40444 and received a CVSS score of 8.8 out of 10. The CVSS standards are used to help security researchers, software users, and vulnerability tracking organizations measure and report on the severity of vulnerabilities. CVSS can also help security teams and developers prioritize threats and allocate resources effectively.
The Cybersecurity and Infrastructure Security Agency took to Twitter to encourage users and organizations to review Microsoft’s mitigations and workarounds to address CVE-2021-40444.
ActiveX
Because MSHTML is the beating heart of Internet Explorer, the vulnerability also exists in that browser. Although given its limited use, there is little risk of infection by that vector. Microsoft Office applications however, use the MSHTML component to display web content in Office documents.
The attack depends on MSHTML loading a specially crafted ActiveX control when the target opens a malicious Office document. The loaded ActiveX control can then run arbitrary code to infect the system with more malware.
So, the attacker will have to trick the user into opening a malicious document. But we all know how good some attackers are at this.
Mitigation
At the moment all supported Windows versions are vulnerable. Since there is no patch available yet, Microsoft proposes a few methods to block these attacks.
- Disable the installation of all ActiveX controls in Internet Explorer via the registry. Previously-installed ActiveX controls will still run, but no new ones will be added, including malicious ones.
- Open documents from the Internet in Protected View or Application Guard for Office, both of which prevent the current attack. This is a default setting but it may have been changed.
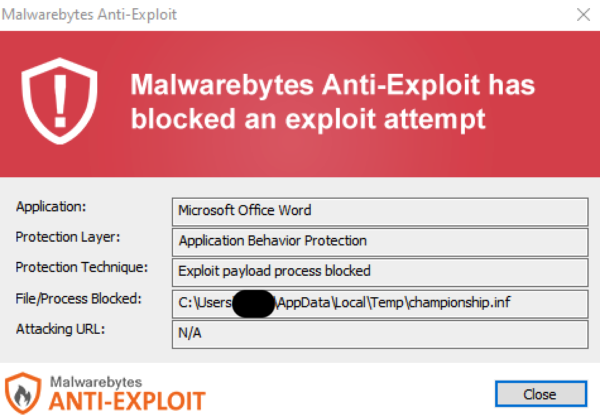
Despite the lack of a ready patch, all versions of Malwarebytes currently block this threat, as shown below. Malwarebytes also detects the eventual payload, Cobalt Strike, and has done so for years, meaning that even if a threat actor had disabled anti-exploit, then Cobalt Strike itself would still be detected.
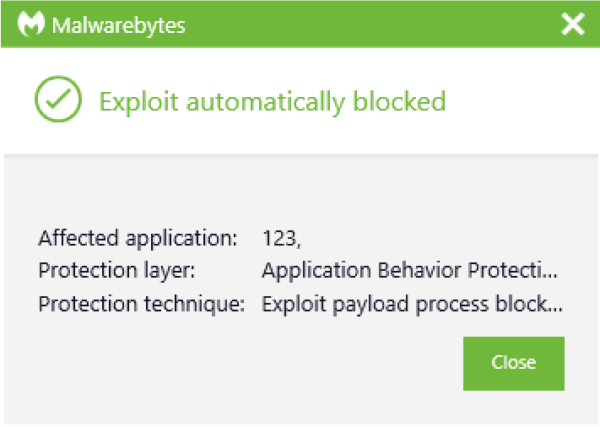

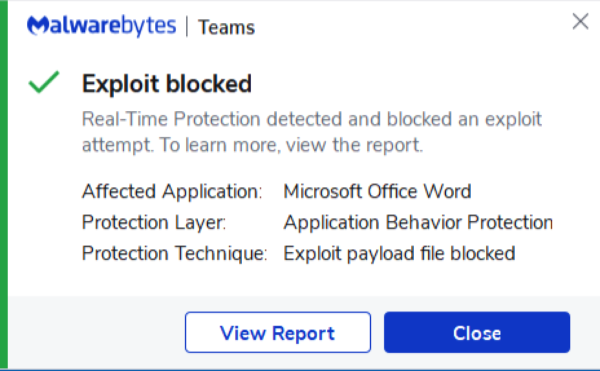

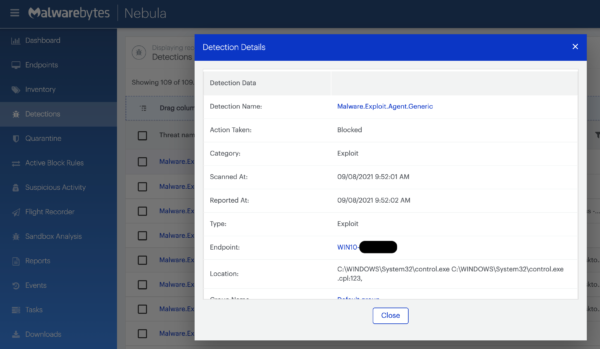

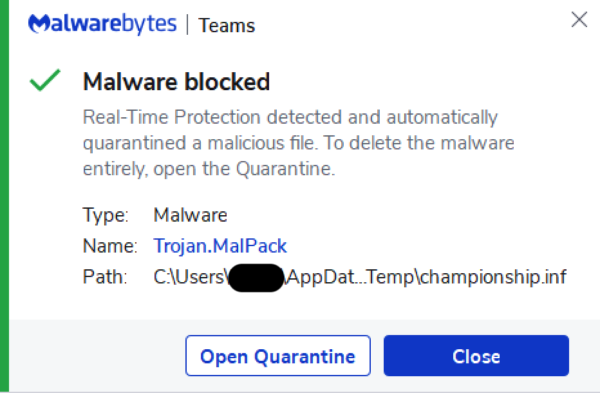


Registry changes
Modifying the registry may create unforeseen results, so create a backup before you change it! It may also come in handy when you want to undo the changes at a later point.
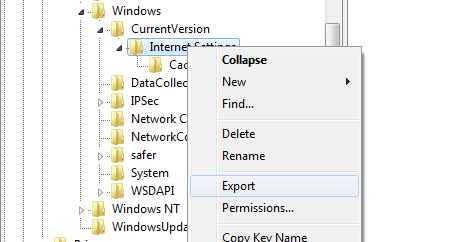
To create a backup, open Regedit and drill down to the key you want to back up (if it exists):
HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsCurrentVersionInternet SettingsZones
Right click the key in the left side of the registry pane and select “Export”. Follow the prompts and save the created reg file with a name and in a location where you can easily find it.

To make the recommended changes, open a text file and paste in the following script. Make sure that all of the code box content is pasted into the text file!
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsCurrentVersionInternet SettingsZones�]
"1001"=dword:00000003
"1004"=dword:00000003
[HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsCurrentVersionInternet SettingsZones1]
"1001"=dword:00000003
"1004"=dword:00000003
[HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsCurrentVersionInternet SettingsZones2]
"1001"=dword:00000003
"1004"=dword:00000003
[HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsCurrentVersionInternet SettingsZones3]
"1001"=dword:00000003
"1004"=dword:00000003
Save the file with a .reg file extension. Right-click the file and select Merge. You’ll be prompted about adding the information to the registry, agree, and then reboot your machine.
Stay safe,everyone!
The post Windows MSHTML zero-day actively exploited, mitigations required appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


