OMIGOD vulnerabilities expose thousands of Azure users to hack
OMIGOD – Microsoft addressed four vulnerabilities in the Open Management Infrastructure (OMI) software agent that could expose Azure users to attacks.
Recently released September 2021 Patch Tuesday security updates have addressed four severe vulnerabilities, collectively tracked as OMIGOD, in the Open Management Infrastructure (OMI) software agent that exposes Azure users to attack. Below is the list of the OMIGOD flaws:
- CVE-2021-38647 – Unauthenticated RCE as root (Severity: 9.8)
- CVE-2021-38648 – Privilege Escalation vulnerability (Severity: 7.8)
- CVE-2021-38645 – Privilege Escalation vulnerability (Severity: 7.8)
- CVE-2021-38649 – Privilege Escalation vulnerability (Severity: 7.0)
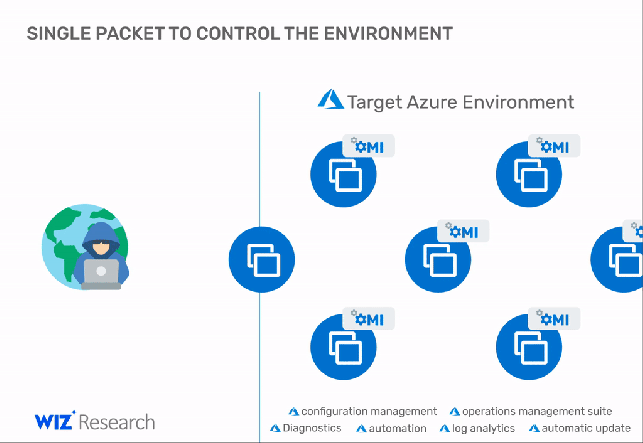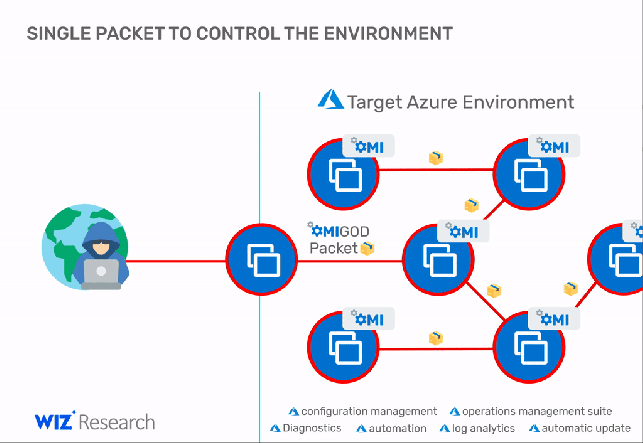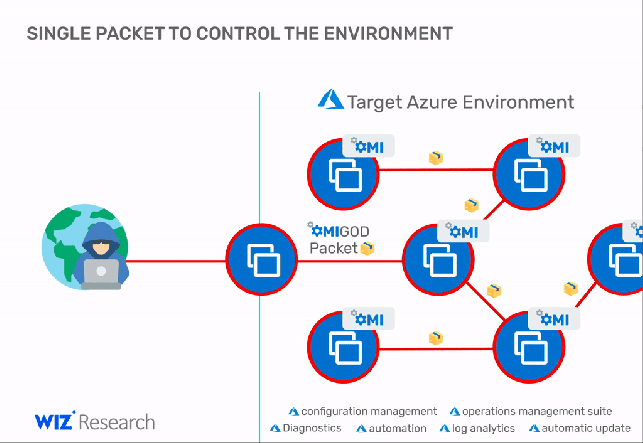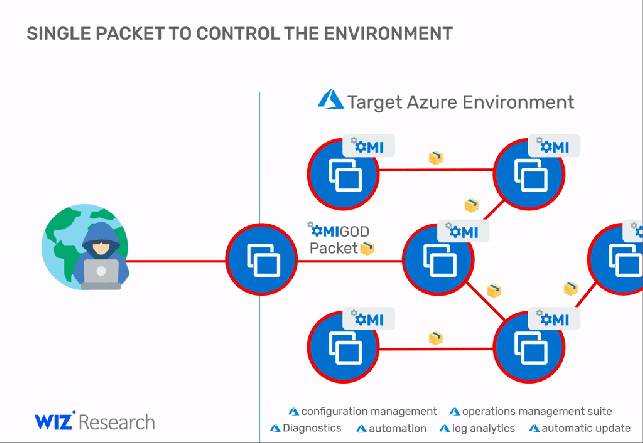
The vulnerabilities were reported by Wiz’s research team, an attacker could exploit OMIGOD vulnerabilities to execute code remotely or elevate privileges on vulnerable Linux virtual machines running on Azure.
Researchers estimate that thousands of Azure customers and millions of endpoints are potentially at risk of attack.
“When customers set up a Linux virtual machine in their cloud, the OMI agent is automatically deployed without their knowledge when they enable certain Azure services. Unless a patch is applied, attackers can easily exploit these four vulnerabilities to escalate to root privileges and remotely execute malicious code (for instance, encrypting files for ransom).” reads the analysis published by the experts. “We named this quartet of zero-days “OMIGOD” because that was our reaction when we discovered them. We conservatively estimate that thousands of Azure customers and millions of endpoints are affected. In a small sample of Azure tenants we analyzed, over 65% were unknowingly at risk.”
OMI is an open-source project written in C that allows users to manage configurations across environments, it is used in various Azure services, including Azure Automation, Azure Insights.
The most severe flaw is a remote code execution flaw tracked as CVE-2021-38647, it received a CVSS score of 9.8.
A remote, unauthenticated attacker could exploit the vulnerability by sending a specially crafted message via HTTPS to port listening to OMI on a vulnerable system.
“With a single packet, an attacker can become root on a remote machine by simply removing the authentication header. It’s that simple.” continues the analysis. “Thanks to the combination of a simple conditional statement coding mistake and an uninitialized auth struct, any request without an Authorization header has its privileges default to uid=0, gid=0, which is root. This vulnerability allows for remote takeover when OMI exposes the HTTPS management port externally (5986/5985/1270).”
Microsoft released a patched OMI version (1.6.8.1) and in order to mitigate the risk of attacks exploiting the CVE-2021-38647 RCE the IT giant recommends limiting network access to OMI listening on ports 5985, 5986, 1270.
Follow me on Twitter: @securityaffairs and Facebook
|
|
Pierluigi Paganini
(SecurityAffairs – hacking, OMIGOD)
The post OMIGOD vulnerabilities expose thousands of Azure users to hack appeared first on Security Affairs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![Mythic C2 Detected - 188[.]124[.]51[.]141:7443 3 mythic](https://www.redpacketsecurity.com/wp-content/uploads/2025/10/mythic.png)
![[NOVA] - Ransomware Victim: Regency Specialist Hospital 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

