Active Exploitation of Citrix NetScaler (CVE-2019-19781): What You Need to Know

On Dec. 17, 2019, a directory traversal vulnerability was announced in the Citrix Application Discovery Controller and Citrix Gateway, which would allow a remote, unauthenticated user to write a file to a location on disk. Affected products include:
- Citrix ADC and Citrix Gateway version 13.0 all supported builds
- Citrix ADC and NetScaler Gateway version 12.1 all supported builds
- Citrix ADC and NetScaler Gateway version 12.0 all supported builds
- Citrix ADC and NetScaler Gateway version 11.1 all supported builds
- Citrix NetScaler ADC and NetScaler Gateway version 10.5 all supported builds
According to security researchers who have done in-depth analysis of the vulnerability, it initially appeared that the impact of this vuln was limited due to the specific file extension (.xml) that could be written to disk. However, upon digging deeper, researchers found that, when combined with the Perl Templating Toolkit, this vulnerability would allow for remote code execution on the host. The Perl Templating Toolkit is a template subsystem for perl, similar to other templating libraries in other languages, that allows for inline code to be embedded in documents to make runtime-generated content easier to manage. For additional technical details, see in-depth analyses here and here.
Rapid7 has deployed several items to help detect the presence of this issue in your environment:
- A remote check for InsightVM customers.
- An update to our Threat Intel Dashboard in InsightVM to enable customers to quickly identify which assets in their environment are affected, along with the relevant contextual information on exploitability, which we outline in more depth below.
- An exploit and scanner for Metasploit customers and Framework users.
Mitigation
Customers and community members are strongly urged to apply the mitigation in Citrix’s knowledge base article until they are able to patch.
Patches will be released starting Jan. 20, 2020. You can see the list of affected products and the expected patch released dates here.
NOTE: As of Jan. 16, security researchers have reported that even if the mitigation is applied as Citrix advises, some firmware versions contain a bug that renders it ineffective. The firmware bug affects Citrix ADC Release 12.1 builds before 51.16/51.19 and 50.31. Citrix advises customers to update to an unaffected build and then ensure the mitigation is applied.
There was a sufficient window in which vulnerable targets were available to attackers that exploitation was possible and is probable, even when targets had mitigations applied. Rapid7 customers who use Citrix ADC in their environment should audit them for signs of exploitation, or consult the Rapid7 Managed Services team for advice, even if they have been patched or have applied the mitigation.
Rapid7 InsightVM customers can still use the check released on Jan. 13 to assess their exposure to this vulnerability. We will continue to update content checks as new information about the vulnerability surfaces.
Exploitation in the wild
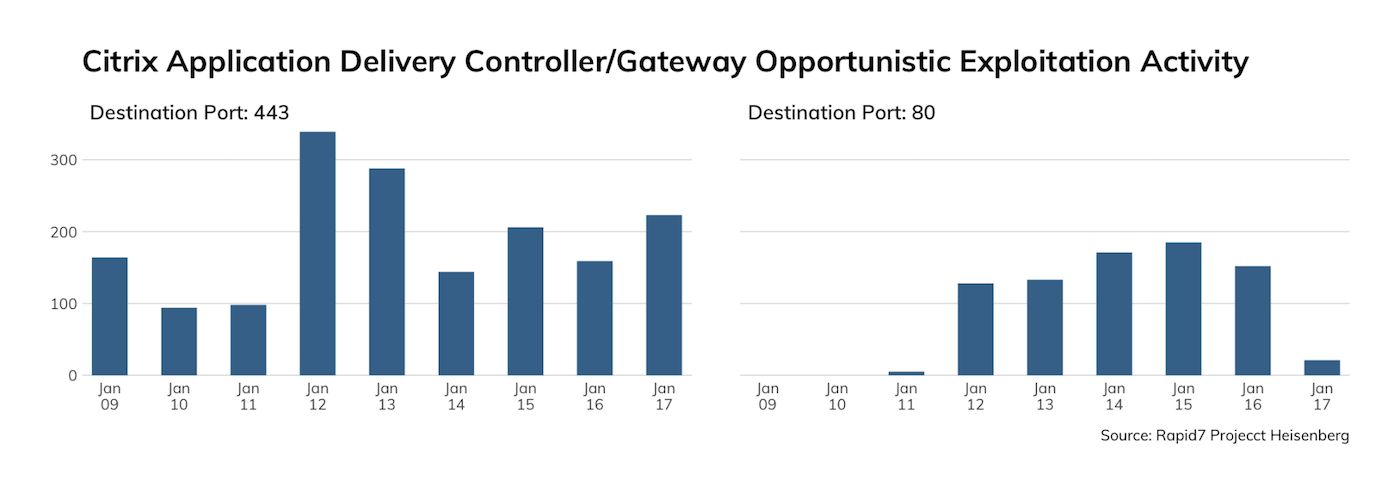
Rapid7 runs Project Heisenberg, which is a honeynet consisting of over 240 nodes in six continents. Heisenberg provides Rapid7 researchers with near-real-time information of exploitation of vulnerabilities for various protocols.
Rapid7 researchers rate this vulnerability as being high-value for attackers. It is trivial to exploit and known to be actively exploited in the wild. Security community researchers have previously noted opportunistic scanning and exploitation; Rapid7 researchers and external researchers have also noted that Citrix NetScaler AMIs on AWS Cloud are vulnerable by default out of the box (as of Jan. 12).
Rapid7 researchers first discovered exploitation of CVE-2019-19781 on Jan. 9, 2020, from several sources. Most of the traffic resembles scanning activity, but due to limitations of the Heisenberg honeynet (specifically, advertising a vulnerable response), these requests may simply be grooming packets attempting to identify targets before sending secondary exploitation payloads.

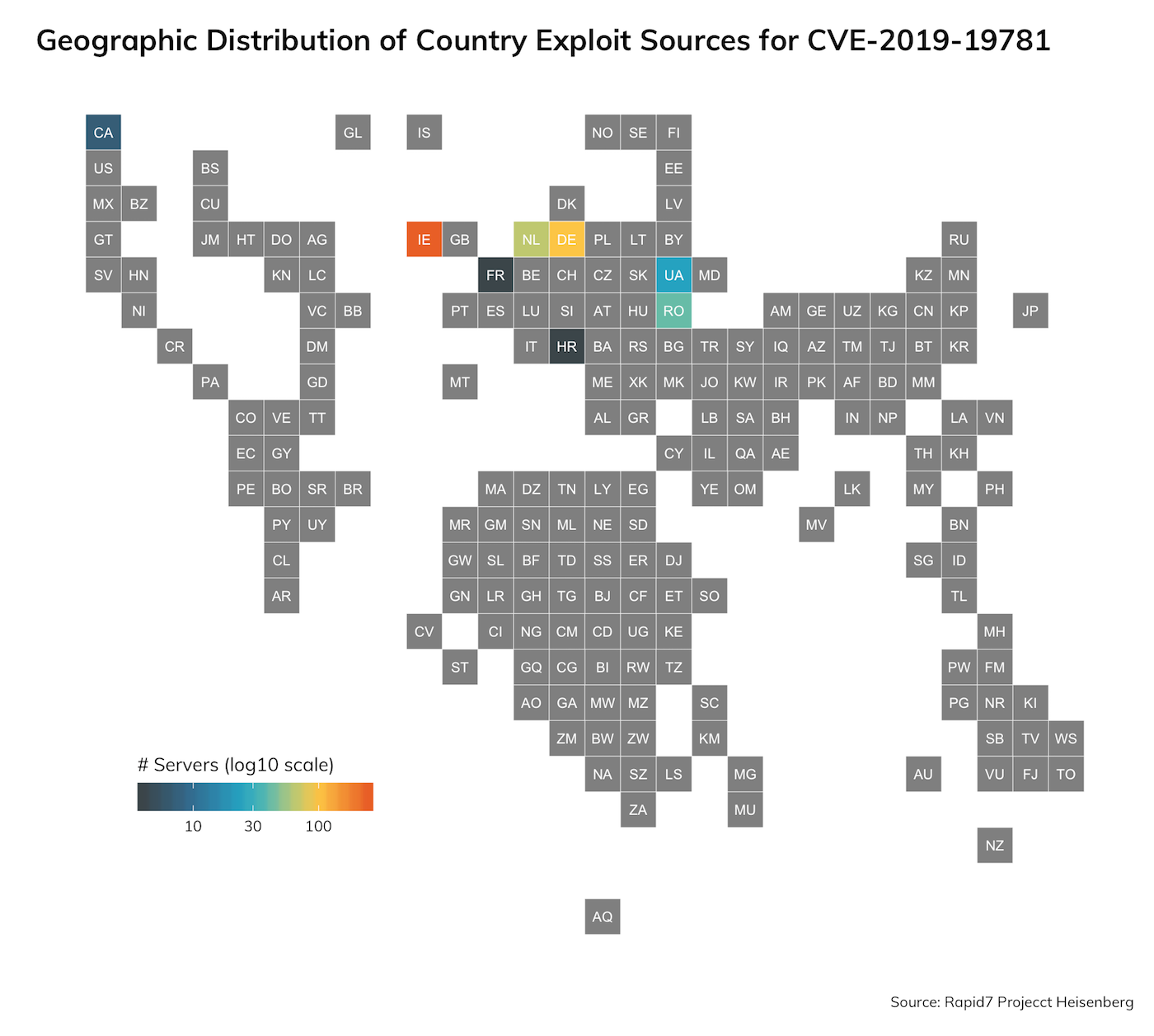

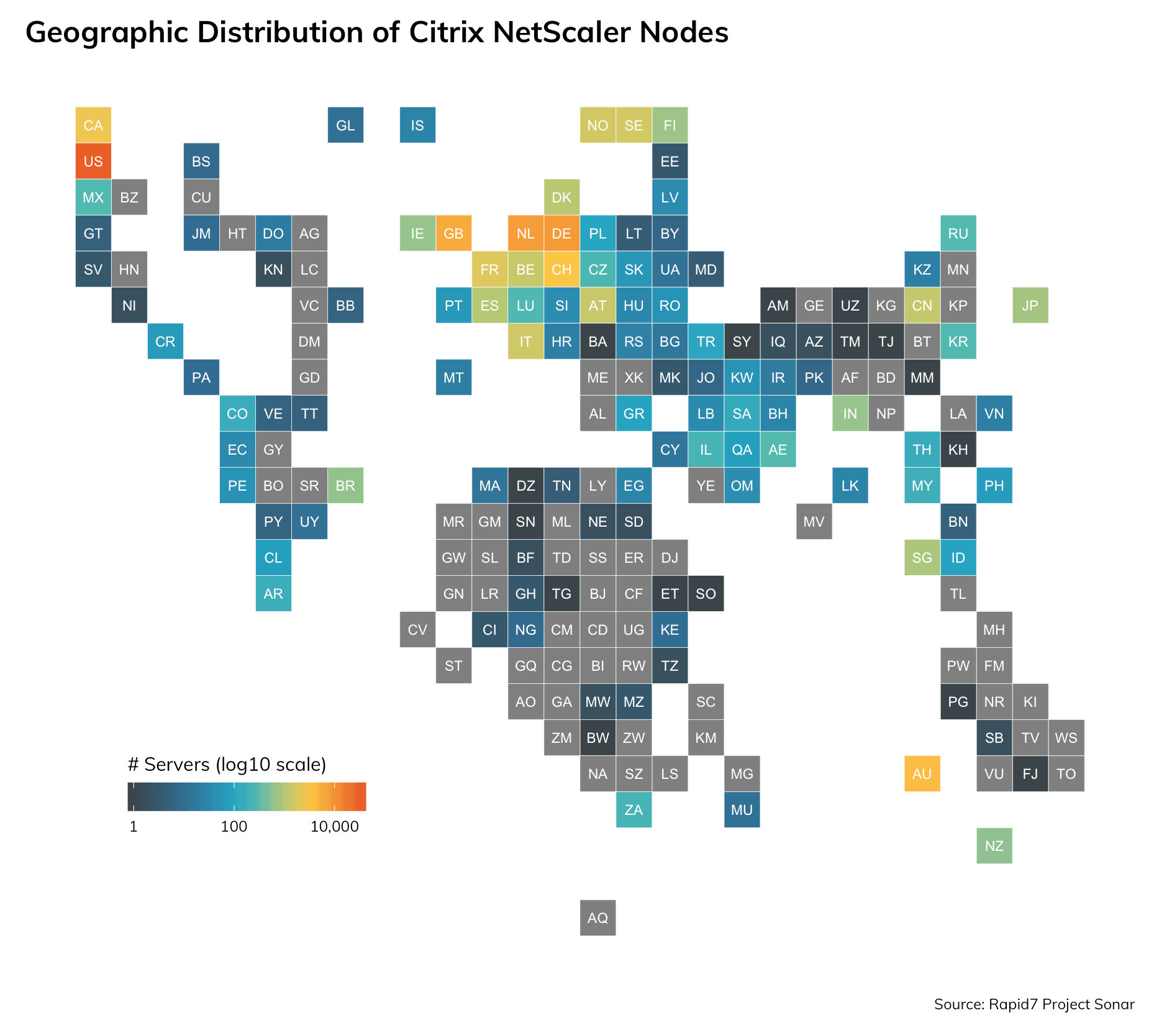
Rapid7 researchers also routinely monitor exposure across the global public internet through Project Sonar. We’ve found over 1 million Citrix ADC nodes on the public internet, depicted on the graph below:

Additional information
Rapid7 Heisenberg information is private due to the sensitive nature of the honeynet we have deployed. However, Rapid7 regularly releases scans of the entire internet, including popular HTTP and HTTPS ports, which would host Citrix ADC/Gateway deployments. You can visit https://opendata.rapid7.com, download HTTP/HTTPS datasets, and use https://github.com/rapid7/dap to filter those datasets for your organization, and learn more about what is exposed on the internet.



