Adult popunder campaign used in mainstream ad fraud scheme
Online advertising is a multi billion dollar industry with projected spending to reach over 600 billion U.S. dollars for 2022. It’s not surprising that criminals are trying their hardest to abuse this ecosystem in any way that they can.
One of the biggest threats and always top of mind for advertisers is bot traffic as it is the equivalent of throwing money down the drain with ads that will never be seen by real eye balls. However, ad fraud is more than bots and in fact, even when traffic is seemingly real, there can still be abuse.
Case in point, we came across a clever ad fraud scheme where a fraudster is running a cost-effective popunder campaign on high-traffic adult websites and then making money via Google Ads. What originally caught our attention was seeing a Google advert on what appeared to be an adult page, as it is strictly against the search giant’s acceptable content policy. It turned out to be a clever way to hide a bogus blog loaded with many more ads, most of them hidden behind a fullscreen pornographic iframe.
As unaware visitors trigger the popunder landing page and continue browsing in their other tab, the decoy website is constantly refreshing with new content and of course new ads, generating millions of ad impressions per month.
We reported this invalid traffic and would like to thank Google for quickly shutting down this ad campaign.
Popunder campaign on top adult sites
It is no secret that adult websites generate a lot of traffic. Did you know that 3 of the top 20’s most visited websites are from the adult industry, the more popular one getting an estimated 2.8 billion monthly visits?
A fraudster has set up an ad campaign with one of the major adult ad networks using an ad format known as a popunder, which is one of the most cost efficient. Depending on the visitor’s geolocation and other parameters, the CPM (cost per thousand impressions) can be as low as $0.05.
A popunder is like a ‘pop-up’ in that it is triggered when a user clicks anywhere on a web page, except that the resulting ad will appear behind the open window. It’s also not like a typical banner ad, it’s actually an entire page, often referred to as a landing page whose goal is to provide clear and interesting information in order to have a high conversion ratio. Examples of common popunders for the adult industry include online dating services, adult webcams, or simply an adult portal.
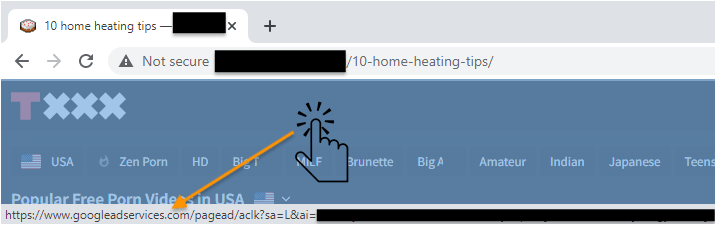
At first, it appears that this popunder is simply promoting another adult website called Txxx. But a couple of things don’t add up: the page’s title and address bar show something completely unrelated and we can see what appears to be a Google ad at the bottom of the page.
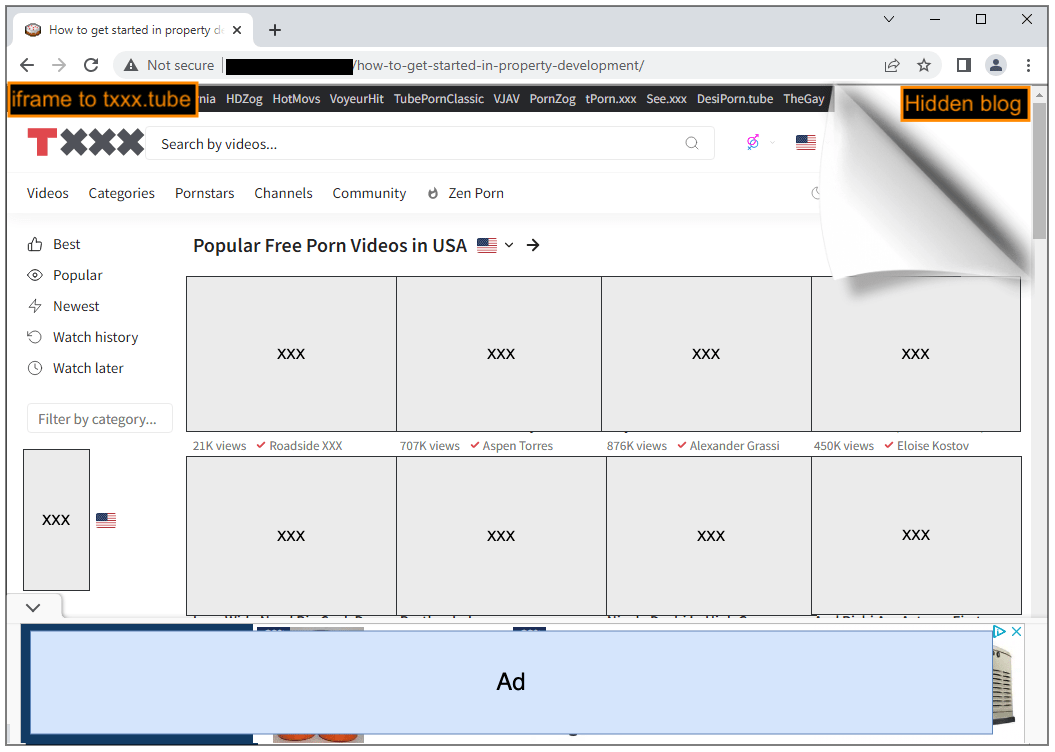
The problem is that Google’s advertising policies state that sexually explicit content such as text, image, audio, or video of graphic sexual acts intended to arouse is not allowed. Technically speaking, the adult content is merely an iframe placed on top of a WordPress blog and the ad at the bottom should really have been hidden in the background.
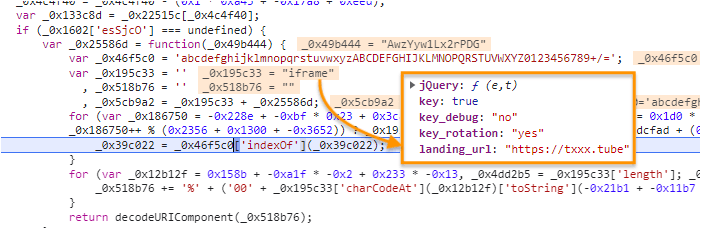
To avoid detection, the code is heavily obfuscated and the iframe is built dynamically:

SEO-friendly content to place ad banners
The fraudster is actually deceiving Google by loading legitimate content (i.e. how to fix your plumbing issues) under a fullscreen XXX iframe. Not only that, but the page also refreshes its content at regular intervals, to serve a new article, still hidden behind with the XXX overlay to further monetize on Google Ads. This happens without the user’s knowledge since the tab was launched as a popunder.
This is no ordinary landing page, it’s actually a full blog with dozens of articles that were stolen from other sites.
- 10-home-heating-tips
- 10-ways-to-style-your-kitchen-countertops-like-a-pro
- 4-main-benefits-of-installing-gutter-protection-systems
- 8-most-common-roof-leak-causes-in-california
- before-you-plan-to-build-your-own-house-work-out-your-budget
- build-your-own-home-in-3-days
- build-your-own-home-in-the-country
- does-your-home-in-california-need-roof-ventilation
- homeowner-s-guide-to-the-best-outdoor-lighting
- how-much-does-a-mortgage-to-build-your-own-house-cost
- how-much-does-it-cost-to-build-a-new-house-in-los-angeles-area
- how-snow-and-ice-impact-your-roof
- how-solar-panels-can-make-your-roof-last-longer
- how-to-adhere-drywall-to-a-concrete-block
- how-to-build-modern-dining-room-in-california
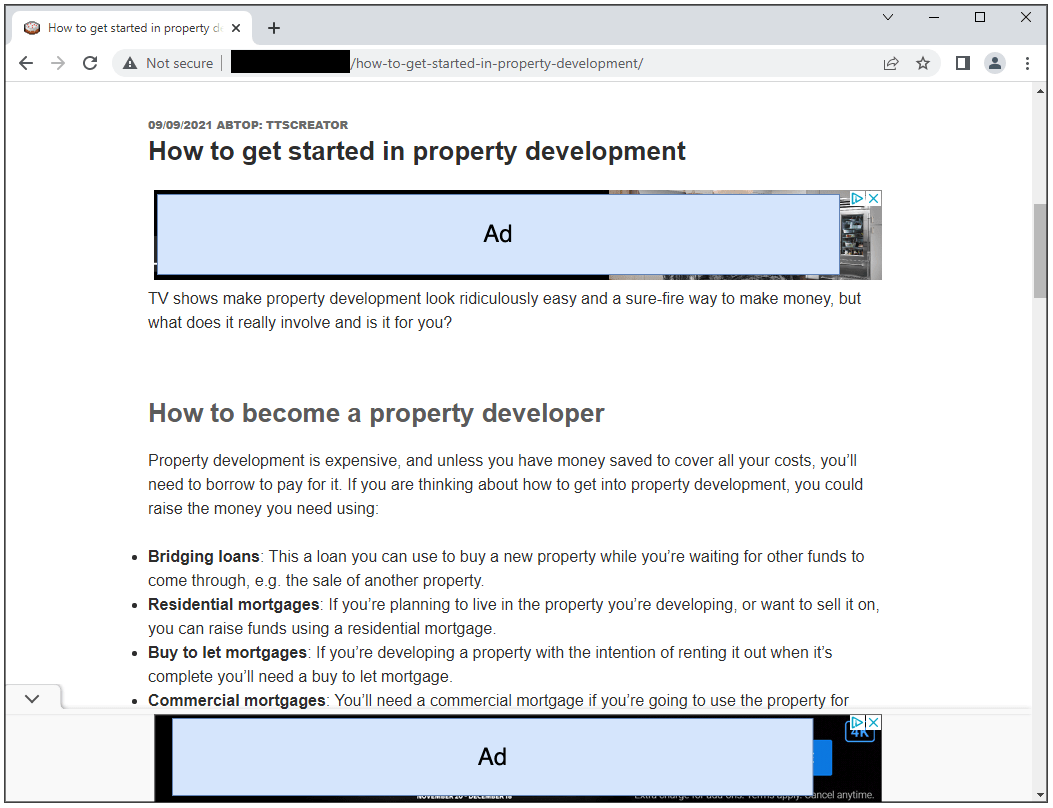

On average (when scrolling through the entire page), there are about 5 Google ads and sometimes even video ads which are more lucrative.
Millions of ad impressions
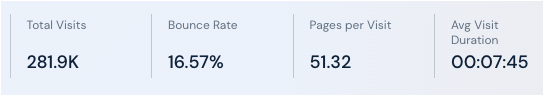
Looking at high level metrics (taken from Similarweb) for that one decoy website we see some interesting figures. The total number of visits per month is close to 300K (and doubling based on previous month data). But the more interesting metric is the number of pages viewed per visit, which is over 51.

How can a human actually browse and read 51 articles in an average of 7 minutes and 45 seconds? The answer is simple: they don’t. The user is most likely busy minding their own business on the other active tab while the popunder page constantly reloads new articles along with Google Ads. We ran a quick capture of what this looks like based on the ad requests made to Google’s servers:
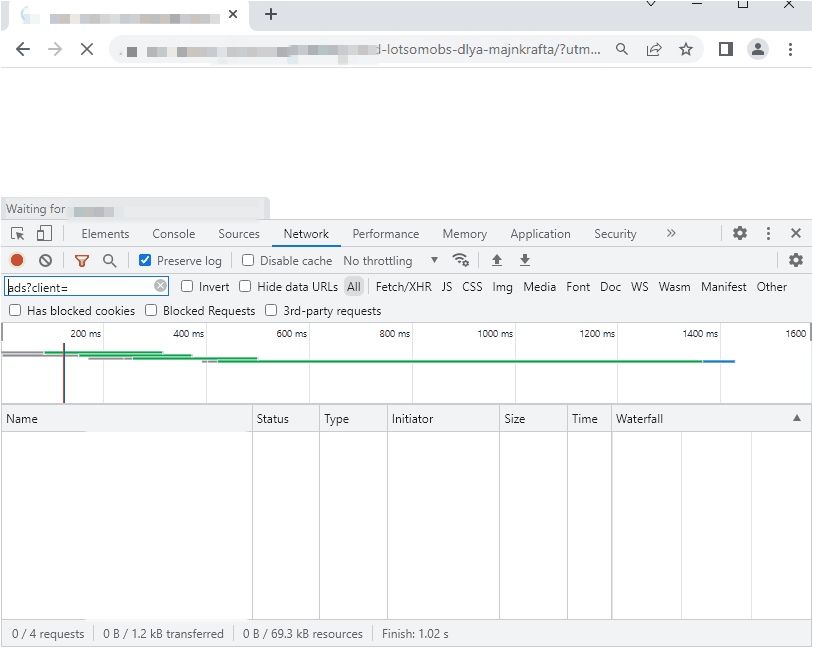

While numbers will vary based on demographics and other settings, we estimate that the page generates an average of 35 ad impressions every minute. If we do the math and multiply the total number of monthly visits (281.9K) and average duration (7:45 min or 465 seconds), we get a total ad impressions of 76,465,375 per month. Calculating the exact revenue made will depend on different factors but with a CPM of $3.50, this scheme could theoretically generate $276,629 a month.
Since these ads are not going to be seen by anyone, we could consider that all those impressions are purely driven by invalid traffic (IVT). This is not typical bot traffic though, because the unwilling participants are real users with genuine IP addresses, cookies and other browser settings. However, there are giveaways such as an unexpectedly high number of pages per visit. For comparison, the most popular adult site has an average of 9 pages and 9 minutes per visit.
There is one more twist to this ad fraud scheme that comes in the form of clickjacking. Once a user gets the tab into focus (it was a popunder), suddenly the page rotation stops and what the user sees is what looks like another adult website (the iframe). A click anywhere on the page (the user may want to select one of the thumbnails and watch a specific video) triggers a real click on a Google ad instead.

Based on the previous stats, the popunder quietly cycles through blogs and ads for an average of 7 minutes and 45 seconds before the user either closes that tab or clicks on the page which would increase the advertiser’s cost-per-click (CPC).
(Fake) real news sites
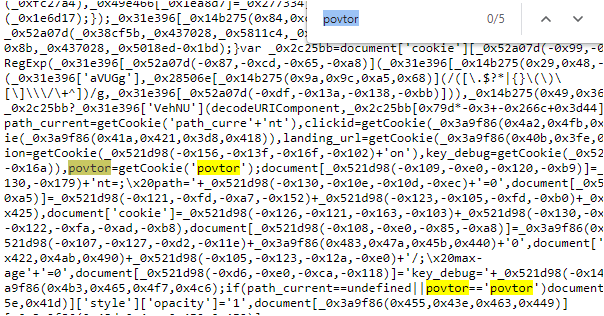
The decoy site used fairly complex and obfuscated code to defraud Google which likely was not developed for a one-off. We wrote a signature based on a string of text that stood out called ‘povtor’ and ran a retrohunt search on VirusTotal. Povtor is Russian for ‘repeat’ which aligns with our understanding of the threat actor likely being Russian.

The retrohunt search returned a number of hits for sites that had something in common: news portals registered on previously expired domains. While we have seen influence campaigns before, pushing only biased news stories for a certain political party, we don’t believe this is the case here. The news articles look balanced and real which would indicate another motive.
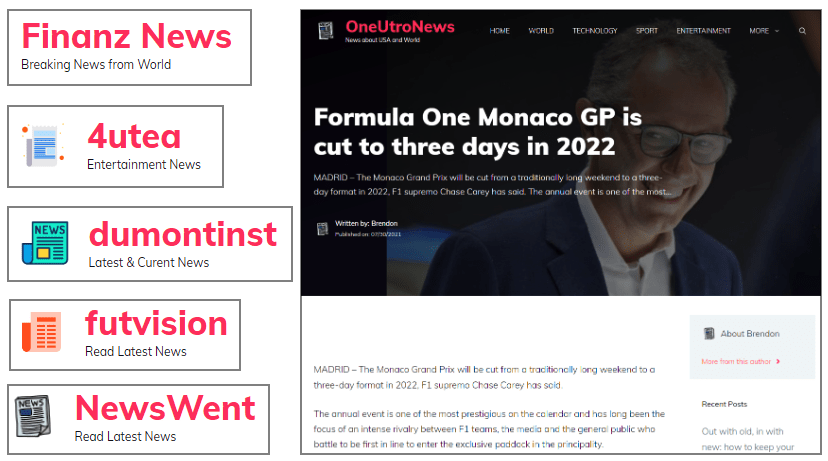

This is again the same modus operandi of grabbing content from various places and creating SEO-friendly sites for advertising purposes. It does not appear that this particular scheme with the news sites was extremely successful though.
Content may be king, except when stolen
Fraudsters will continuously look for ways to make money online, with minimal effort required. Leveraging adult traffic ensures large volume and cost-efficient campaigns thanks to the pop-under format which is perfectly suited for running a landing page that will stay open for several minutes until the user closes it.
Visitors are not genuinely going to the website and can’t even see ads that are masked by a full page iframe. However, those users are not bots and they have the correct browser settings and networking attributes, possibly making it harder to identify the invalid traffic.
Had it not been for a Google ad displayed at the bottom of the page (all other ads were hidden behind the XXX iframe), we likely would not have detected this fraudulent scheme. Even with web traffic analysis, the presence of an iframe does not clearly standout when all other content appears to be genuine.
Perhaps the content itself may be where security models will work best. It would be unlikely for a fraudster to write a hundred blog articles by themselves; it would make more sense at least to hire a third-party to produce that amount of content. This is why detecting duplicates and identifying copycat sites may yield good results from phishing pages to bogus blackhat SEO websites.
After our reporting to Google, we confirmed that the website was no longer loading ads, and instead showed blank iframes.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below
To keep up to date follow us on the below channels.







![Sliver C2 Detected - 89[.]23[.]117[.]246:31337 17 Sliver C2](https://www.redpacketsecurity.com/wp-content/uploads/2024/02/Sliver-C2-300x142.jpg)
