All Dutch govt networks to use RPKI to prevent BGP hijacking

The Dutch government will upgrade the security of its internet routing by adopting before the end of 2024 the Resource Public Key Infrastructure (RPKI) standard.
RPKI, or Resource Certification protects against erroneous rerouting of internet traffic, maliciously or not, through cryptographic verification of the routes.
The standard uses digital certificates to secure the Border Gateway Protocol (BGP) used for exchanging routing information and ensure that the traffic comes through the legitimate network operator controlling the IP addresses on the destination path.
RPKI for all ICT systems
Standardization Forum in the Netherlands, a research and advising organization that serves the public sector on the use open standards, announced that all communication devices (ICT) managed by the Dutch government must use the RPKI standard by 2024.
The government supported the recommendation and in a decision last week it adopted the policy that refers to both newly added ICT equipment as well as the existing systems.
RPKI certificates are stored centrally and kept public, allowing network providers from anywhere in the world to validate internet traffic routes.
Networks that implement RPKI can be confident that internet traffic is routed only through authorized paths, thus eliminating the risks of man-in-the-middle or other data diversion and interception attacks.
Without RPKI, Internet routing depends on the trust of the network operators advertising the correct IP prefixes they manage. Under this model, though, if an operator falsely advertises that they handle a particular set of IP addresses, they would receive traffic that would otherwise take a different path.
Apart from the performance impact (e.g. network latency, disruption), this trust-based model opens the door to malicious BGP hijacking that allows traffic interception and monitoring, as well as spoofing legitimate IP addresses for spamming.
One example of BGP hijacking is from 2019, when network traffic from Dutch internet service provider KPN was diverted to China Telecom for over two hours.
Internet traffic rerouting can also happen by mistake when a a configuration error causes a network operator to announce the IP space of another party. In 2021, such an accident disrupted thousands of networks all over the world.
RPKI adoption
The adoption of RPKI is already high in the Netherlands, with 77.9% of government websites and 75.1% of email domains already supporting the standard.


However, global adoption of RPKI has moved slower than its developers and proponents hoped, with tier-two ISPs falling behind.
The National Institute of Standards and Technology (NIST) in the U.S. has a live RPKI monitor that provides real-time information about the RPKI ecosystem drawn from various data repositories, including BGP routing information.
According to NIST data from April 2023, about 41% of verifiable IPv4 prefix-origin pairs comply with RPKI, 58% are susceptible to routing incidents, and 1% have a mismatch in their route origin keys, so they’re are not valid.
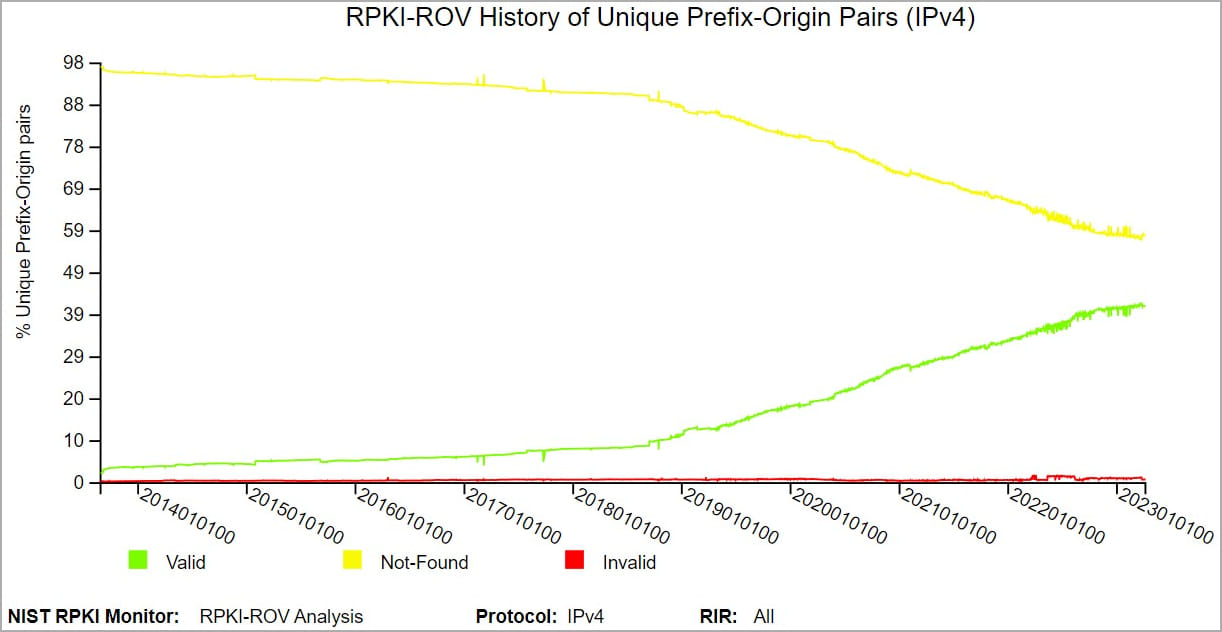

RPKI contributes to a safer and better internet, but a 41% adoption rate shows that there is still a long way to improving traffic security across the globe.
In early 2020, RPKI adoption rate was 18% and grew to 27% in January 2021, and 33.5% at the beginning of 2022.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.








