Android Malware Chameleon Disables Fingerprint Unlock To Steal Pins

The Chameleon Android banking trojan has re-emerged with a new version that uses a tricky technique to take over devices — disable fingerprint and face unlock to steal device PINs.
It does this by using an HTML page trick to acquire access to the Accessibility service and a method to disrupt biometric operations to steal PINs and unlock the device at will.
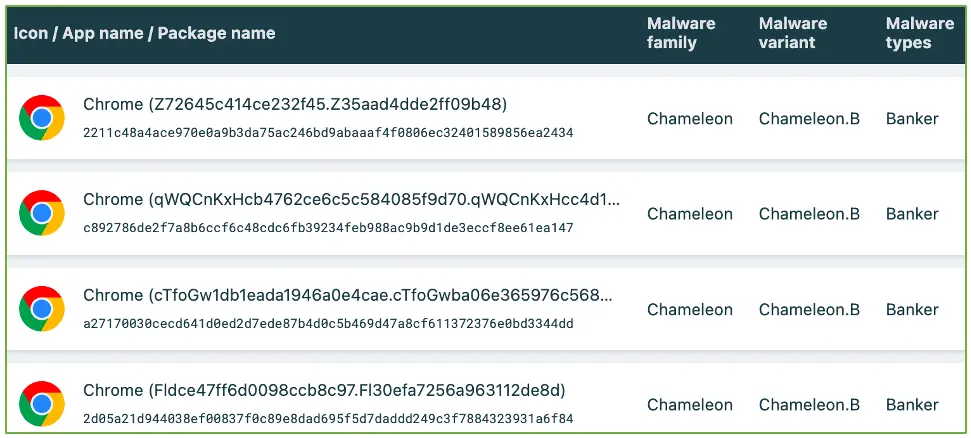
Earlier versions of Chameleon spotted in April this year impersonated Australian government agencies, banks, and the CoinSpot cryptocurrency exchange, performing keylogging, overlay injection, cookie theft, and SMS theft on compromised devices.
Researchers at ThreatFabric, who have been following the malware, report that it is currently distributed via the Zombinder service, posing as Google Chrome.
Zombinder “glues” malware to legitimate Android apps so that victims can enjoy the full functionality of the app they intended to install, making it less likely to suspect that dangerous code is running in the background.
The platform claims its malicious bundles are undetectable in runtime, bypassing Google Protect alerts and evading any anti-virus products running on the infected device.
New Chameleon features
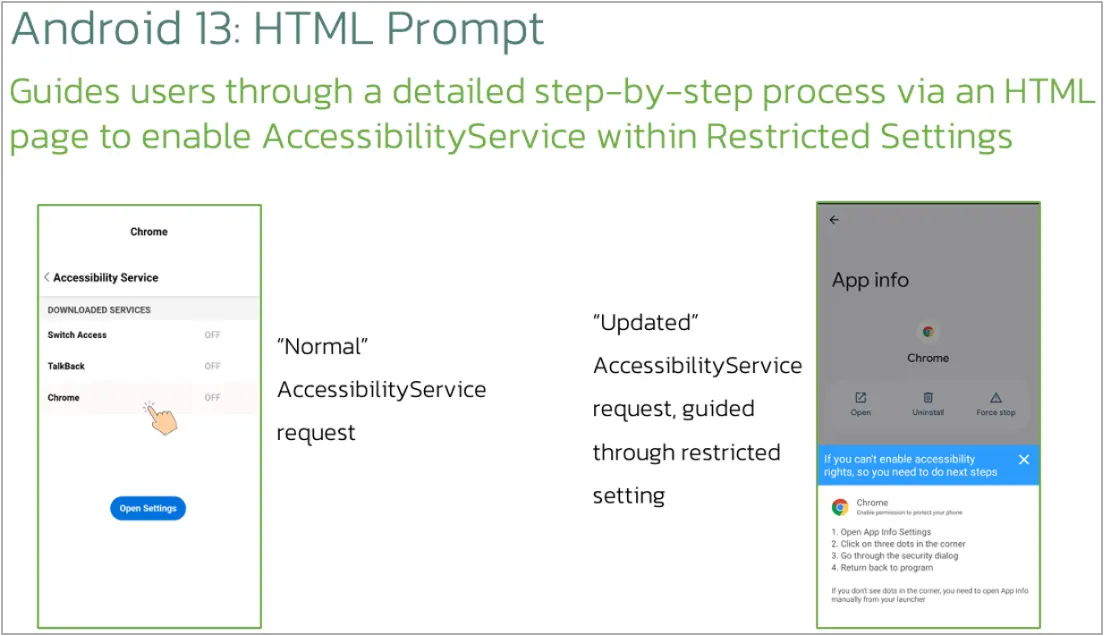
The first new feature seen in the latest Chameleon variant is the ability to display an HTML page on devices running Android 13 and later, prompting victims to give the app permission to use the Accessibility service.
Android 13 and later are protected by a security feature called “Restricted setting,” which blocks the approval of dangerous permissions like Accessibility, which malware can leverage to steal on-screen content, grant itself additional permissions, and perform navigation gestures.
When Chameleon detects Android 13 or 14 upon launch, it loads an HTML page that guides the user through a manual process to enable Accessibility for the app, bypassing the system’s protection.
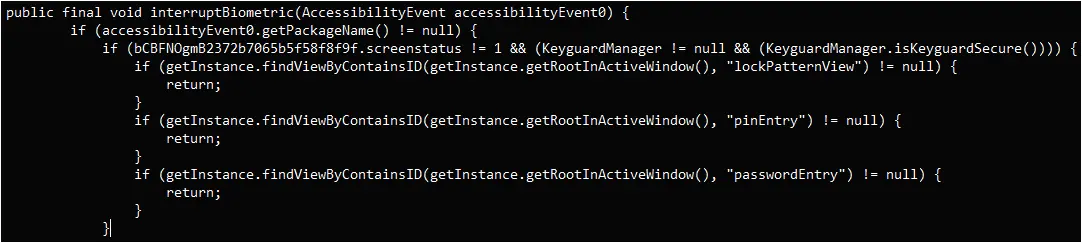
The second notable new feature is the ability to interrupt biometric operations on the device, like fingerprint and face unlock, by using the Accessibility service to force a fallback to PIN or password authentication.
The malware captures any PINs and passwords the victim enters to unlock their device and can later use them to unlock the device at will to perform malicious activities hidden from view.
Finally, ThreatFabric reports that Chameleon has added task scheduling through the AlarmManager API to manage the periods of activity and define the type of activity.
Depending on whether Accessibility is enabled or disabled, the malware adapts to launching overlay attacks or performing app usage data collection to decide on the best moment for injection.
“These enhancements elevate the sophistication and adaptability of the new Chameleon variant, making it a more potent threat in the ever-evolving landscape of mobile banking trojans,” warns ThreatFabric.
To keep the Chameleon threat at bay, avoid sourcing APKs (Android package files) from unofficial sources, as this is the primary distribution method for the Zombinder service.
Additionally, ensure that Play Protect is enabled at all times, and run regular scans to ensure your device is clean of malware and adware.
