Apache Ofbiz Rce Flaw Exploited To Find Vulnerable Confluence Servers

A critical Apache OFBiz pre-authentication remote code execution vulnerability is being actively exploited using public proof of concept (PoC) exploits.
Apache OFBiz (Open For Business) is an open-source enterprise resource planning system many businesses use for e-commerce inventory and order management, human resources operations, and accounting.
OFBiz is part of Atlassian JIRA, a commercial project management and issue-tracking software used by over 120,000 companies worldwide. Therefore, any flaws in the open-source project are inherited by Atlassian’s product.
This authentication bypass flaw is tracked as CVE-2023-49070 and was fixed in OFBiz version 18.12.10, released on December 5, 2023.
The issue potentially enabled attackers to elevate their privileges without authentication, perform arbitrary code execution, and access sensitive information.
While investigating Apache’s fix, which was to remove the XML-RPC code from OFBiz, SonicWall researchers discovered that the root cause for CVE-2023-49070 was still present.
This incomplete fix still allowed attackers to exploit the bug in a fully patched version of the software.
Actively exploited in attacks
In a write-up published yesterday, SonicWall researchers demonstrate it’s possible to bypass Apache’s fix for the CVE-2023-49070 vulnerability when using specific credential combinations.
“It was discovered while researching the root cause for the previously disclosed CVE-2023-49070,” explains SonicWall’s report.
“The security measures taken to patch CVE-2023-49070 left the root issue intact and therefore the authentication bypass was still present.”
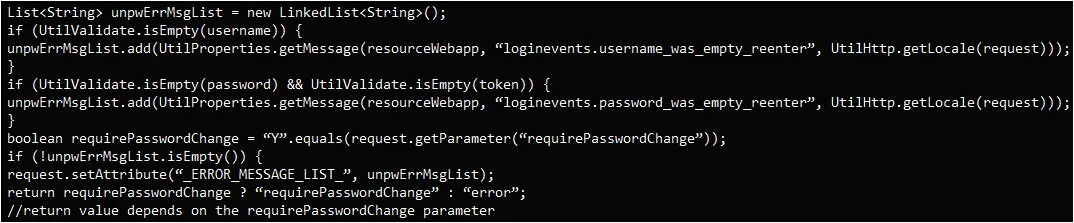
This patch bypass is caused by flawed logic in handling empty or special parameters like “requirePasswordChange=Y.”
SonicWall reported their findings to the Apache team, who quickly resolved the flaw, which they categorized as a server-side request forgery (SSRF) problem.
The new bypass issue was assigned CVE-2023-51467 and was addressed in OFBiz version 18.12.11, released on December 26, 2023.
However, not many have upgraded to this latest release yet, and the abundance of public PoCs exploits for the pre-auth RCE makes the flaw an easy target for hackers.
Threat monitoring service ‘Shadowserver’ reported today that it has detected quite a few scans that leverage public PoCs, attempting to exploit CVE-2023-49070.
“Throughout December we have observed scans using a PoC that has been published for CVE-2023-49070, so expect similar for CVE-2023-51467,” warned ShadowServer CEO Piotr Kijewski.
Kijewski told BleepingComputer that current exploitation attempts are being conducted to find vulnerable servers by forcing them to connect to an oast.online URL.
The researchers further said those scanning vulnerable servers are particularly interested in finding vulnerable Confluence servers.
Confluence servers are a popular target for threat actors as they commonly hold sensitive data that can be used to spread laterally on to further internal services or for extortion.
To minimize the risk, users of Apache OFBiz are recommended to upgrade to version 18.12.11 as soon as possible.