ApkLeaks – Scanning APK File For URIs, Endpoints And Secrets
Scanning APK file for URIs, endpoints & secrets.
Installation
To install apkLeaks, simply:
$ git clone https://github.com/dwisiswant0/apkleaks
$ cd apkleaks/
$ pip install -r requirements.txt
Or download at release tab.
Dependencies
Install global packages:
Linux
$ sudo apt-get install libssl-dev swig -yOSX
$ brew install openssl swig
Windows
You need to install:
- OpenSSL, and
- swig-win.
Usage
Basically,
$ python apkleaks.py -f ~/path/to/file.apk
Options
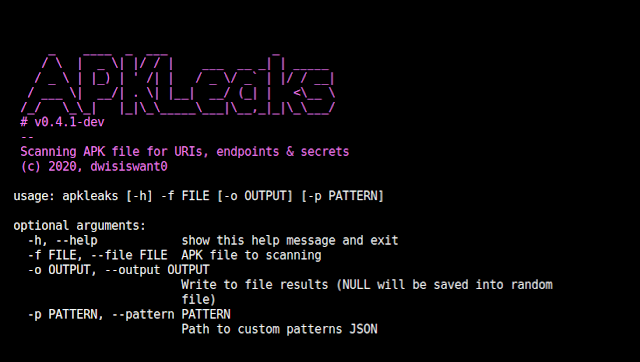
usage: apkleaks [-h] -f FILE [-o OUTPUT] [-p PATTERN]
optional arguments:
-h, --help show this help message and exit
-f FILE, --file FILE APK file to scanning
-o OUTPUT, --output OUTPUT
Write to file results (NULL will be saved into random
file)
-p PATTERN, --pattern PATTERN
Path to custom patterns JSON
In general, if you don’t provide -o argument, then it will generate results file automatically.
Custom patterns can be added with the following flag --pattern /path/to/rules.json to provide sensitive search rules in the JSON file format. For example,
// rules.json
{
"Amazon AWS Access Key ID": "AKIA[0-9A-Z]{16}",
...
}$ python apkleaks.py -f /path/to/file.apk -c rules.json -o ~/Documents/apkleaks-resuts.txt
Version
Current version is v1.0.2, and still development.
Credits and Thanks
Since this tool includes some contributions, and I’m not an asshole, I’ll publically thank the following users for their help and resource:
- @ndelphit – for his inspiring
apkurlgrep, that’s why this tool was made. - @dxa4481 and y’all who contribute to
truffleHogRegexes. - @GerbenJavado & @Bankde – for awesome pattern to discover URLs, endpoints & their parameters from
LinkFinder. - @tomnomnom – a
gfpatterns. - @pxb1988 – for awesome APK dissambler
dex2jar. - @ph4r05 for standalone APK parser.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[QILIN] - Ransomware Victim: Magna Hospitality Group 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

