Avast releases free BianLian ransomware decryptor

Security software company Avast has released a free decryptor for the BianLian ransomware strain to help victims of the malware recover locked files without paying the hackers.
The availability of a decryptor comes only about half a year after increased activity from BianLian ransomware over the summer of 2022, when the threat group breached multiple high-profile organizations.
Avast’s decryption tool can only help victims attacked by a know variant of the BianLian ransomware.
If the hackers are using a new version of the malware that researchers have yet to catch, the tool is of no help at the moment.
However, Avast says the BianLian decryptor is a work in progress, and the ability to unlock more strains will be added shortly.
BianLian ransomware
BianLian (not to be confused with the same-name Android banking trojan) is a Go-based ransomware strain targeting Windows systems.
It uses the symmetric AES-256 algorithm with the CBC cipher mode to encrypt over 1013 file extensions on all accessible drives.
The malware performs intermittent encryption on the victim’s files, a tactic that helps speed up the attacks at the expense of data locking strength.
Encrypted files get the “.bianlian” extension, while the generated ransom note warns victims that they have ten days to meet the hacker’s demands or their private data will be published on the gang’s data leak site.
For more details on the operation of BianLian ransomware, check out this SecurityScoreCard report on the strain published in December 2022.
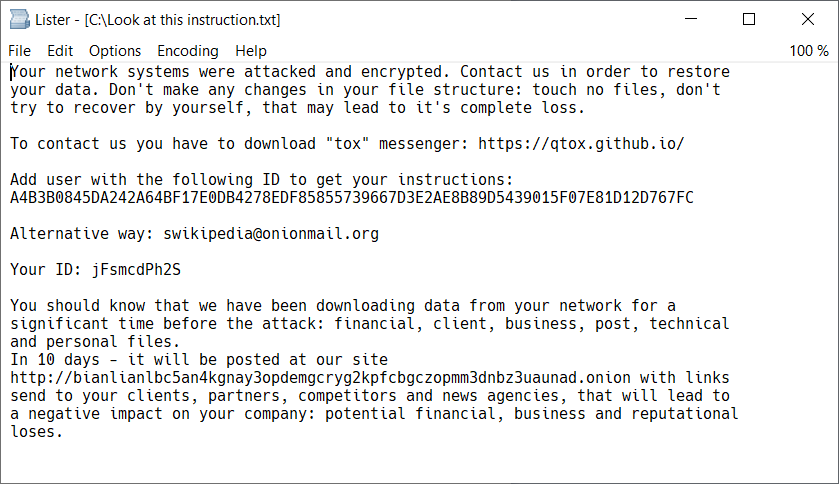

Avast’s decryptor
The BianLian ransomware decryptor is available for free and the program is a standalone executable that doesn’t require installation.
Users can select the location they wish to decrypt and provide the software with a pair of original/encrypted files.
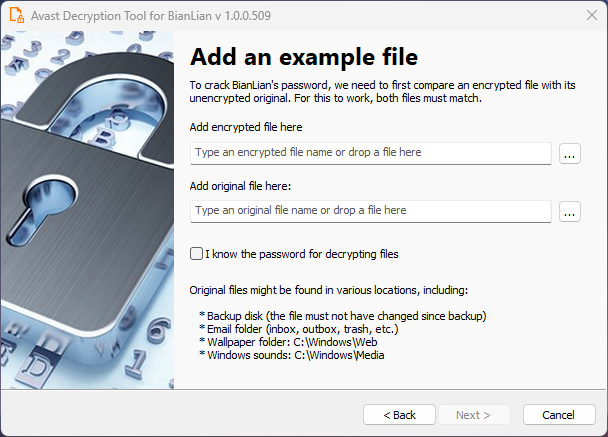

There’s also an option for users with a valid decryption password, but if the victim doesn’t have one, the software can still attempt to figure it out by iterating through all known BianLian passwords.
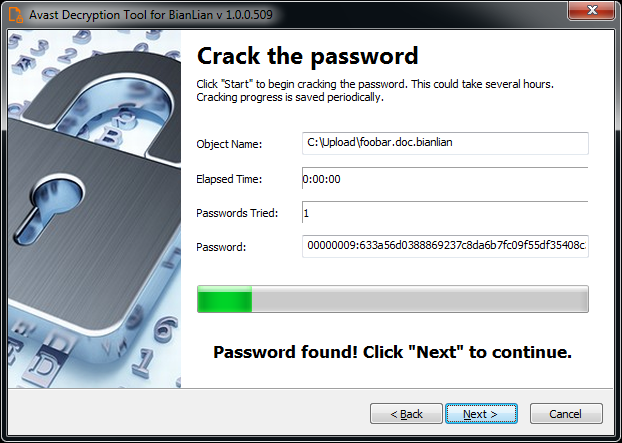
The decryptor also offers an option to backup encrypted files to prevent irreversible loss of data if something goes wrong during the process.
Those attacked by newer versions of the BianLian ransomware will have to locate the ransomware binary on the hard drive, which might contain data that can be used for deciphering the locked files.
Avast says some common filenames and locations for BianLian are:
- C:\Windows\TEMP\mativ.exe
- C:\Windows\Temp\Areg.exe
- C:\Users\%username%\Pictures\windows.exe
- anabolic.exe
However, because the malware deletes itself after the file encryption phase, it is unlikely that victims will find those binaries on their systems.
Those who manage to retrieve BinaLian binaries are requested to send them to “[email protected]” to help Avast improve its decrypter.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below
To keep up to date follow us on the below channels.






