AvosLocker ransomware uses Microsoft Exchange Server vulnerabilities, says FBI
The FBI has issued an advisory about the AvosLocker ransomware. Notably the FBI has noticed that several victims have reported Microsoft Exchange Server vulnerabilities as the intrusion vector.
AvosLocker is a Ransomware as a Service (RaaS) affiliate-based group that has targeted victims across multiple critical infrastructure sectors in the United States including financial services, critical manufacturing, and government facilities.
Threat profile
AvosLocker ransomware is a multi-threaded Windows executable written in C++ that runs as a console application and shows a log of actions performed on victim systems. AvosLocker ransomware encrypts files on a victim’s server and renames them with the “.avos” extension.
The AvosLocker executable leaves a ransom note called GET_YOUR_FILES_BACK.txt in all directories where encryption occurs. The ransom note includes a .onion site that contains instructions for paying the ransom and receiving a decryption key.
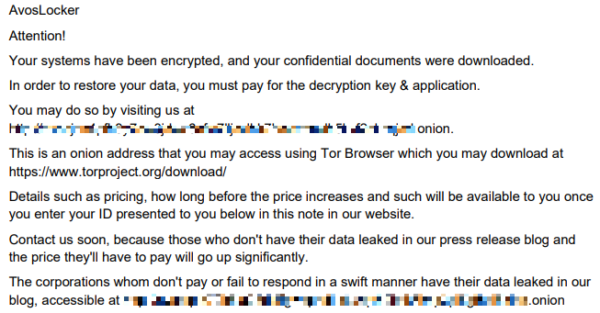

Attention!
Your systems have been encrypted, and your confidential documents were downloaded.
In order to restore your data, you must pay for the decryption key & application.
You may do so by visiting us at <onion address>.
This is an onion address that you may access using Tor Browser which you may download at https://www.torproject.org/download/
Details such as pricing, how long before the price increases and such will be available to you once you enter your ID presented to you below in this note in our website.
Contact us soon, because those who don’t have their data leaked in our press release blog and the price they’ll have to pay will go up significantly.
The corporations whom don’t pay or fail to respond in a swift manner have their data leaked in our blog, accessible at <onion address>
So, besides encrypting your files, AvosLocker also exfiltrates data and threatens to publish the stolen data to its leaks site. The public leak site not only lists victims of AvosLocker, along with a sample of data allegedly stolen from the victim’s network, but also gives visitors an opportunity to view a sample of victim data and to purchase that data.
The FBI also notes that in some cases, AvosLocker victims receive phone calls from an AvosLocker representative. The caller encourages the victim to go to the .onion site to negotiate, and threatens to post stolen data online. In some cases, AvosLocker actors will threaten and execute distributed denial-of-service (DDoS) attacks during negotiations.
Exchange vulnerabilities
Since AvosLocker is a Ransomware-as-a-Service it may depend on the affiliate which of the vulnerabilities gets used.
The Exchange Server vulnerabilities are named as: CVE-2021-31207, CVE-2021-34523, and CVE-2021-34473, and CVE-2021-26855.
CVE-2021-31207: a Microsoft Exchange Server security feature bypass vulnerability. The vulnerability allows a remote user to bypass the authentication process. This is the way in.
CVE-2021-34523: a Microsoft Exchange Server elevation of privilege (EoP) vulnerability. The vulnerability allows a user to raise their permissions. This is how they take control.
CVE-2021-34473: a Microsoft Exchange Server remote code execution (RCE) vulnerability. The vulnerability allows an authenticated user to execute arbitrary code in the context of SYSTEM and write arbitrary files. This allows the attacker to drop malware on the server and run it.
This is exactly the same attack chain we described in August 2021. This chain of attack was generally referred to as ProxyShell.
Another RCE vulnerability in Exchange Server has been seen as well:
CVE-2021-26855: the ProxyLogon vulnerability which we discussed in detail in our article on Microsoft Exchange attacks causing panic as criminals go shell collecting. The vulnerability allows an attacker to drop a webshell on a vulnerable Exchange Server. A web shell is a script used by an attacker that allows them to escalate and maintain persistent access on an already compromised web application. (Obviously, not every web shell is malicious, but the non-malicious ones are not interesting to us in this context.)
Mitigation
As we stated earlier, all these vulnerabilities have been patched. So, if you are wondering which updates to install next and you are running one or more Microsoft Exchange Server instances, starting there might be a good idea.
Microsoft’s team has published a script on GitHub that can check the status of protection against ProxyLogon vulnerabilities of Exchange servers.
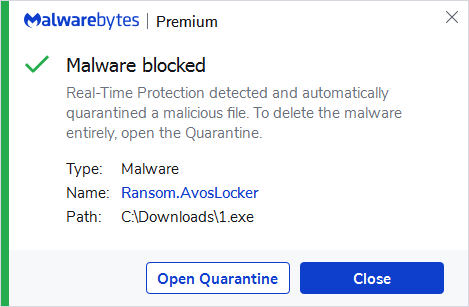
Detection
Malwarebytes detects AvosLocker as Ransom.AvosLocker.

Stay safe, everyone!
The post AvosLocker ransomware uses Microsoft Exchange Server vulnerabilities, says FBI appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


