Bumblebee Malware Attacks Are Back After 4 Month Break

The Bumblebee malware has returned after a four-month vacation, targeting thousands of organizations in the United States in phishing campaigns.
Bumblebee is a malware loader discovered in April 2022 and is believed to have been developed by the Conti and Trickbot cybercrime syndicate as a replacement for the BazarLoader backdoor.
The malware is commonly distributed in phishing campaigns to drop additional payloads on infected devices, such as Cobalt Strike beacons, for initial network access and to conduct ransomware attacks.
In a new malware campaign observed by Proofpoint, the return of Bumblebee since October is significant as it could lead to a broader increase in cybercrime activities as we head into 2024.
Spreading through fake voicemails
The new phishing campaign pushing Bumblebee pretends to be voicemail notifications that utilize the subject of “Voicemail February” and were sent to thousands of organizations in the U.S. from the address “info@quarlessa[.]com.”
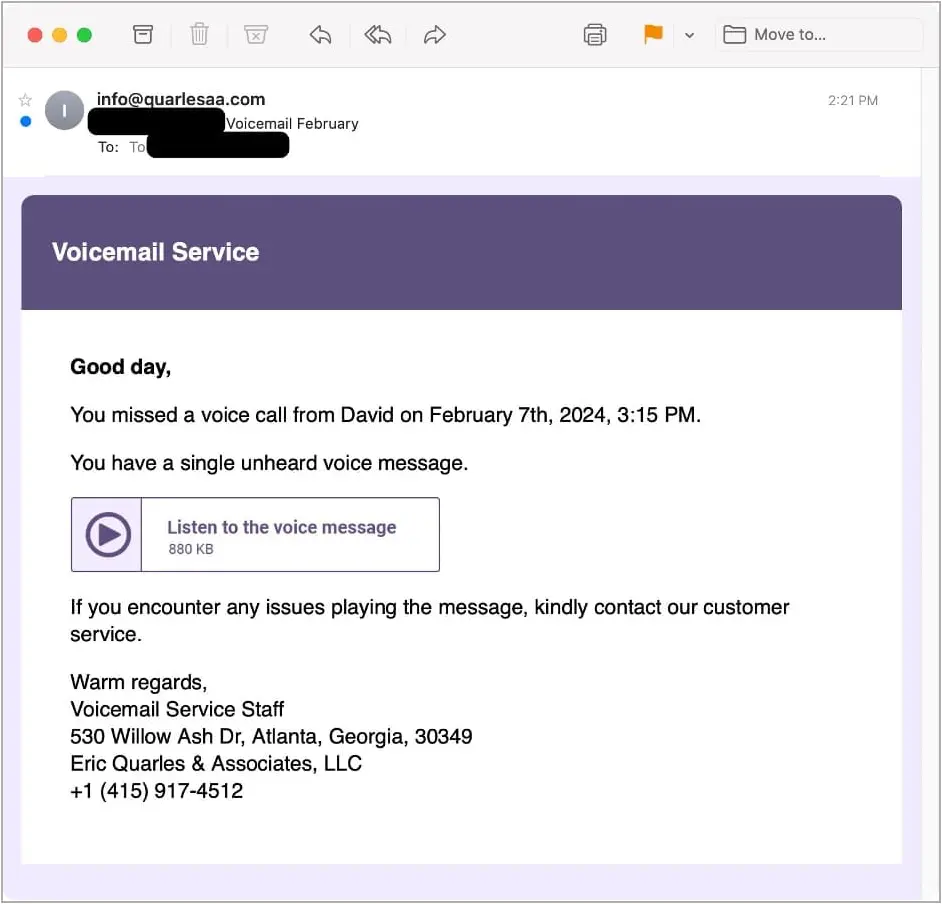
Source: Proofpoint
The emails contain a OneDrive URL that downloads a Word document named “ReleaseEvans#96.docm” or something similar, with a lure pretending to be from consumer electronics company hu.ma.ne, known for its AI-powered pin.
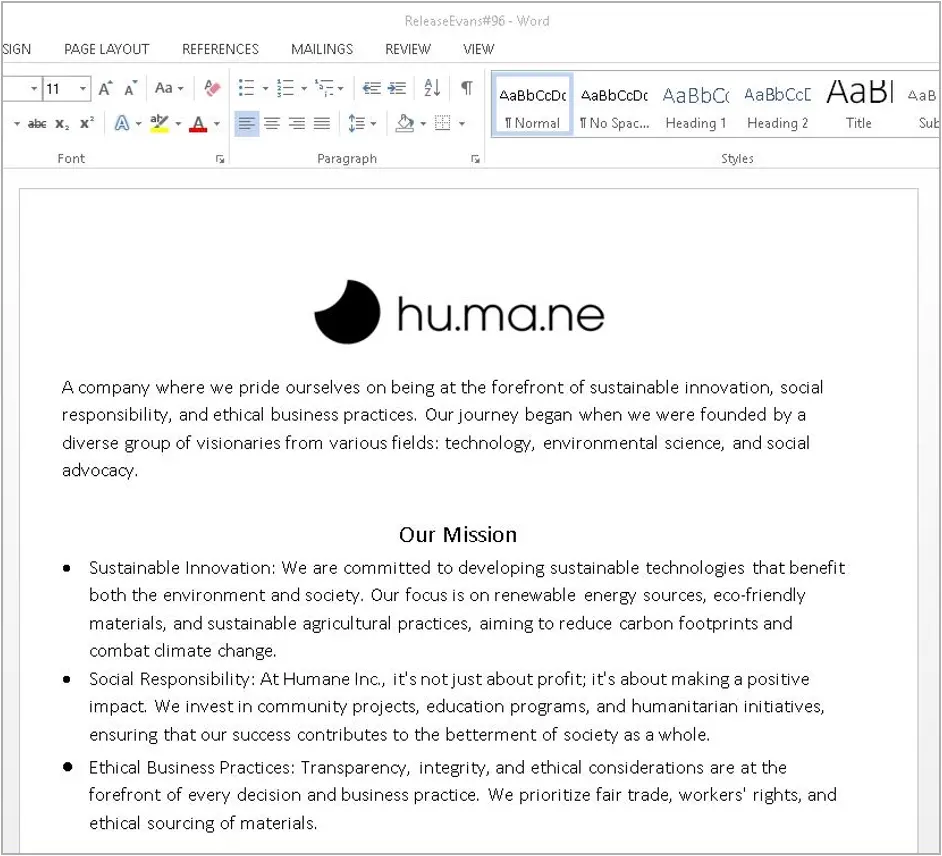
Source: Proofpoint
The malicious document employs macros to create a script file in the Windows temp folder and then executes the dropped file using “wscript.”
This temporary file contains a PowerShell command that fetches and executes the next stage from a remote server, which eventually downloads and launches the Bumblebee DLL (w_ver.dll) on the victim’s system.
Proofpoint comments that using VBA macros in documents is notable and unusual following Microsoft’s decision to block macros by by default in 2022, making it harder for the campaign to achieve much success.
Previous Bumblebee campaigns employed methods like direct DLL downloads, HTML smuggling, and exploitation of vulnerabilities such as CVE-2023-38831 to deliver the final payload, so the current attack chain represents a significant departure from more modern techniques.
Possible explanations for this include evasion since malicious VBAs are now less common or niche/narrow targeting aimed at severely outdated systems. Additionally, Bumblebee may be testing and diversifying its distribution methods.
Proofpoint says Bumblebee has experimented with macro-laden documents in past campaigns, although those cases correspond to just 4.3% of the total recorded (230 campaigns).
Before Bumblebee’s break, the last notable development in the malware was in September 2023, when the malware employed a new distribution technique relying on the abuse of 4shared WebDAV services to evade blocklists.
Cybercrime back to work
Bumblebee is typically rented to cybercriminals who want to bypass the initial access stage and introduce their payloads into already-breached systems.
Proofpoint says there’s not enough evidence to attribute the recent campaign to any particular threat groups. However, the researchers say the campaign bears the hallmarks of the threat actors they track as TA579.
According to Proofpoint, other threat actors who have recently shown a resurgence in their activities include TA576, TA866, TA582, and TA2541.
Law enforcement authorities’ disruption of QBot (Qakbot) has created a void in the payload distribution market, which other malware are attempting to fill.
Notable cases include DarkGate and Pikabot, two highly capable malware loaders that now drive infections via multiple channels, including phishing, malvertising, and messages on Skype and Microsoft Teams.
Zscaler published a report on Pikabot yesterday, noting that the malware has reemerged with a new, simplified version this month, following a short hiatus after Christmas last year.
The new Pikabot version has stripped the advanced code obfuscation techniques used previously and uses a less versatile configuration system, so it looks like an early release of a revamped variant.
