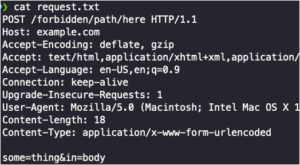
BokuLoader – A Proof-Of-Concept Cobalt Strike Reflective Loader Which Aims To Recreate, Integrate, And Enhance Cobalt Strike’s Evasion Features!
A proof-of-concept User-Defined Reflective Loader (UDRL) which aims to recreate, integrate, and enhance Cobalt Strike's evasion features! Contributors: Contributor Twitter...


















![[QILIN] - Ransomware Victim: Sai Mai Hospital 25 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
