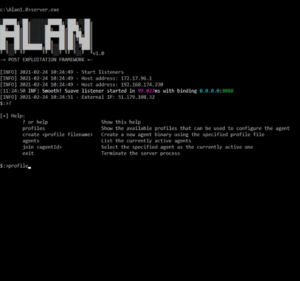
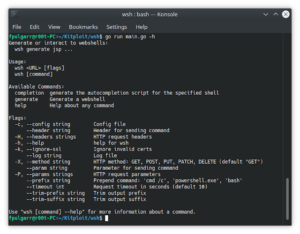
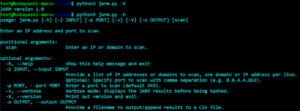
Brutus – An Educational Exploitation Framework Shipped On A Modular And Highly Extensible Multi-Tasking And Multi-Processing Architecture
An educational exploitation framework shipped on a modular and highly extensible multi-tasking and multi-processing architecture. Brutus: an IntroductionLooking for version...









![[DEVMAN] - Ransomware Victim: m*c*e*ic*l[.]com 26 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
![Cobalt Strike Beacon Detected - 165[.]154[.]125[.]212:8080 27 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
