Colt Changes Tune, Admits Data Theft As Warlock Gang Begins Auction
A week after its services were disrupted by a cyberattack, UK telco Colt Technology Services has gone back on its initial statement to confirm that data has indeed been stolen.
The Warlock ransomware group claimed responsibility for the attack and said it swiped customer data, which is now up for auction on its dark web site.
Colt is now saying, via a freshly minted page dedicated to information about the attack, that data was stolen, but it is not yet sure of the extent of the theft, or whose data was taken.
“Through our extensive investigation, we have determined that some data has been taken,” it said. “Our priority is to determine at pace the precise nature of the data that is impacted and notify any affected parties.
“Our dedicated incident response team, including external investigators and forensic experts, is working to investigate this incident. This has, and will continue, 24/7.
“We continue to work closely with law enforcement agencies as part of our investigation.”
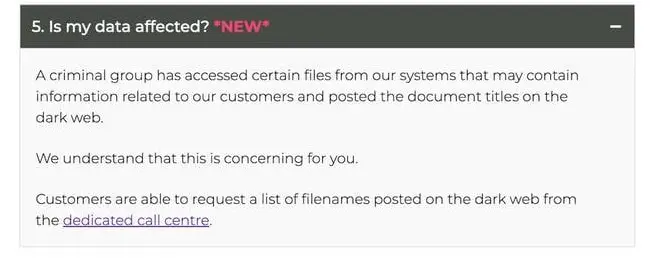
In an FAQ section, it added that certain files “may contain information related to our customers.”
In a very unusual move, the company is also offering customers the opportunity to request the full list of file names that it says were posted to the dark web, via Colt’s dedicated call center.
Since the file list does not appear to be available via Warlock’s page, this suggests the company is potentially in contact with the group. We have asked Colt about this.
Unlike typical double extortion ransomware scenarios, Warlock has not leaked even a snippet of the data it stole online yet. It opted to try and sell the data privately via auction, which ends on August 27.
Auctioning data privately is an uncommon way for cybercrooks to monetize stolen information, but not entirely unheard of either. One high-profile case in recent years was RansomHub’s raid on auctioneering giant Christie’s.
Why the attackers chose to auction off the data is unconfirmed, but experts speaking to The Register at the time said they could have been having some fun, or that they were unable to steal anything of real value, and conducted a so-called private auction to mask the fact they didn’t steal enough to warrant a meaningful extortion demand.
As time went by, RansomHub did not adopt the auctioning model of monetizing stolen data in the long term, lending further support for the face-saving explanation.
Lingering effects
Colt’s status page continues to indicate that its customer portal, Colt Online, and its Voice API platform – an automated voice services management system – remain down as a result of the attack.
“We sincerely apologise for any inconvenience this may be causing. Our teams have been working tirelessly to restore these services and will continue their efforts.”
Some customers may also find that its number-hosting API platform and Colt On Demand – its network as a service portal – are unavailable, and they might struggle to order new services too.
Service disruption at the London-based telco began on August 12, and it confirmed suspicions of foul play three days later.
It has not provided an estimated date by which it will return to normal operations.
Warlock and its SharePoint exploits
Researchers at Trend Micro published research into the Warlock group this week, noting that it was among the ransomware and state-sponsored groups known to be exploiting the now-patched SharePoint bugs with which many organizations had been pwned, starting in July.
Infosec watcher Kevin Beaumont posited in the early days of the Colt attack that the method of entry into its systems was the widely exploited SharePoint vulnerabilities, and while Trend Micro did not name Colt specifically among Warlock’s victims, the fact that multiple experts say the group is a known abuser of the flaws lends support for Beaumont’s claims.
Trend said among Warlock’s recent victims were technology and critical infrastructure organizations, spanning regions such as North America, Europe, Asia, and Africa.
Warlock burst onto the ransomware scene in June after it started advertising its wares on RAMP, the Russian cybercrime forum.
It appealed to cybercriminals by encouraging them to contact the group if they wanted to own a Lamborghini.
Trend said that it quickly racked up a healthy list of victims – half of which were government agencies – and that the group may have ties to the fallen Black Basta. ®
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[Palo Alto Networks Security Advisories] CVE-2025-4614 PAN-OS: Session Token Disclosure Vulnerability 1 Palo_Alto_Networks_Logo](https://www.redpacketsecurity.com/wp-content/uploads/2025/02/Palo_Alto_Networks_Logo-300x55.png)

