Connectwise Urges Screenconnect Admins To Patch Critical Rce Flaw

ConnectWise warned customers to patch their ScreenConnect servers immediately against a maximum severity flaw that can be used in remote code execution (RCE) attacks.
This security bug is due to an authentication bypass weakness that attackers can exploit to gain access to confidential data or execute arbitrary code remotely on vulnerable servers in low-complexity attacks that don’t require user interaction.
The company also patched a path traversal vulnerability in its remote desktop software, which can only be abused by attackers with high privileges.
“Vulnerabilities were reported February 13, 2024, through our vulnerability disclosure channel via the ConnectWise Trust Center,” ConnectWise warned.
“There is no evidence that these vulnerabilities have been exploited in the wild, but immediate action must be taken by on-premise partners to address these identified security risks.”
ConnectWise has yet to assign CVE IDs to the two security flaws that impact all servers running ScreenConnect 23.9.7 and prior.
While ScreenConnect cloud servers hosted on screenconnect.com cloud or hostedrmm.com are already secured against potential attacks, admins using on-premise software are advised to update their servers to ScreenConnect version 23.9.8 immediately.
Huntress security researchers reported earlier today that they’ve already created a proof-of-concept (PoC) exploit that can be used to bypass authentication on unpatched ScreenConnect servers.
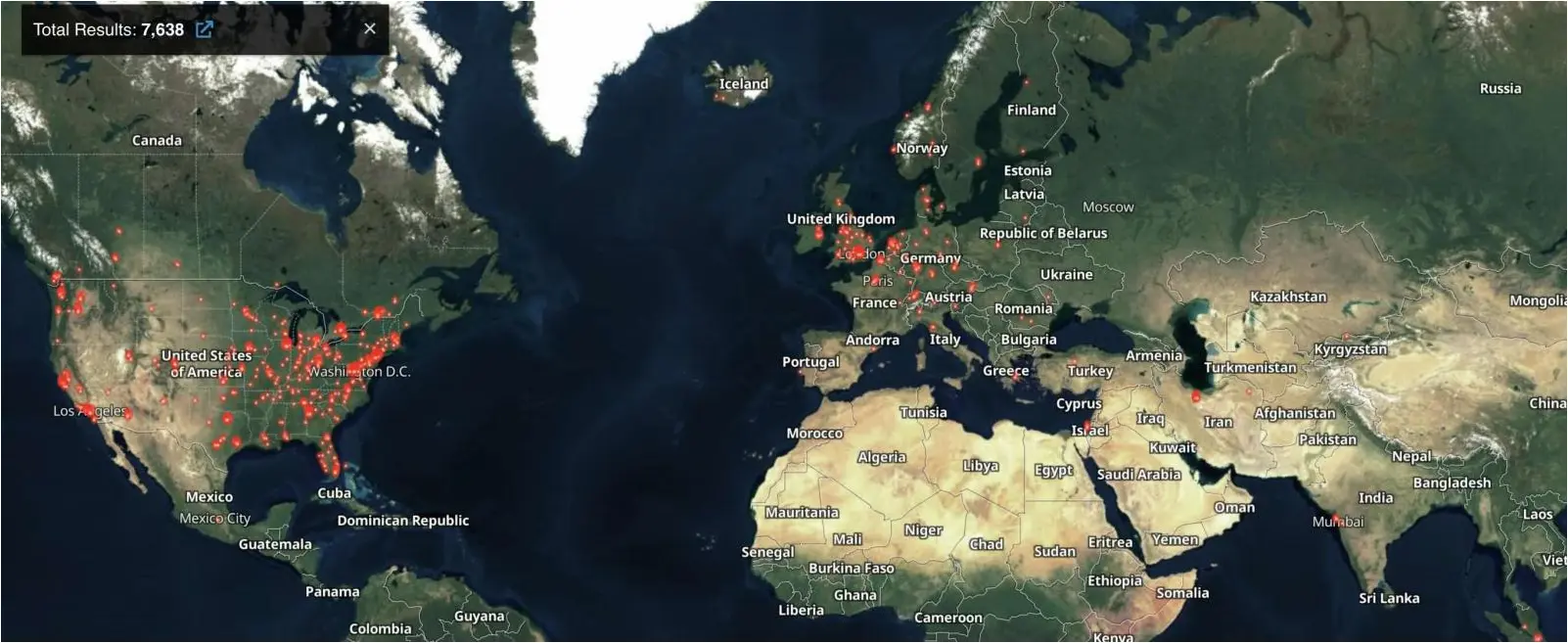
Huntress added that a search on the Censys exposure management platform allowed them to find more than 8,800 servers vulnerable to attacks.
Shodan also tracks over 7,600 ScreenConnect servers, with only 160 currently running the patched ScreenConnect 23.9.8 version.
Last month, CISA, the NSA, and MS-ISAC issued a joint advisory warning that attackers increasingly use legitimate remote monitoring and management (RMM) software such as ConnectWise ScreenConnect for malicious purposes.
By using remote desktop software as an entry point into their targets’ networks, threat actors can access their systems as local users without requiring admin permissions or new complete software installations.
This allows them to bypass security controls and gain access to other devices on the network by taking advantage of the compromised user’s permissions.
Attackers have been using ScreenConnect for malicious purposes for years, including stealing data and deploying ransomware payloads across victims’ breached systems.
More recently, Huntress also spotted threat actors using local ScreenConnect instances for persistent access to hacked networks.
