Cyclops Ransomware Gang Offers Go-Based Info Stealer to Cybercriminals
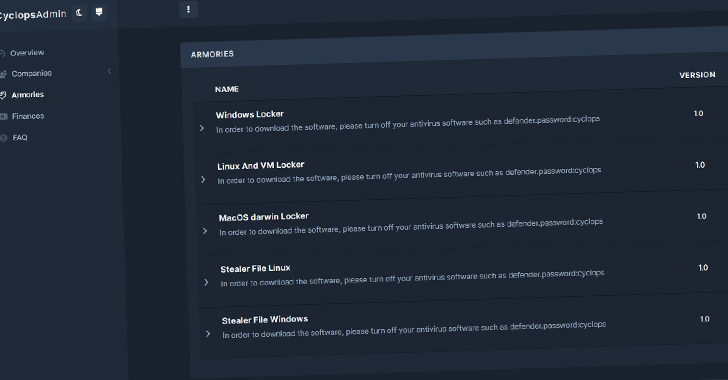
Threat actors associated with the Cyclops ransomware have been observed offering an information stealer malware that’s designed to capture sensitive data from infected hosts.
“The threat actor behind this [ransomware-as-a-service] promotes its offering on forums,” Uptycs said in a new report. “There it requests a share of profits from those engaging in malicious activities using its malware.”
Cyclops ransomware is notable for targeting all major desktop operating systems, including Windows, macOS, and Linux. It’s also designed to terminate any potential processes that could interfere with encryption.
The macOS and Linux versions of Cyclops ransomware are written in Golang. The ransomware further employs a complex encryption scheme that’s a mix of asymmetric and symmetric encryption.
The Go-based stealer, for its part, is designed to target Windows and Linux systems, capturing details such as operating system information, computer name, number of processes, and files of interest matching specific extensions.
The harvested data, which comprises .TXT, .DOC, .XLS, .PDF, .JPEG, .JPG, and .PNG files, is then uploaded to a remote server. The stealer component can be accessed by a customer from an admin panel.
The development comes as SonicWall detailed a new strain of information stealer called Dot Net Stealer to siphon information from web browsers, VPNs, installed apps, and cryptocurrency wallets, in what’s a further evolution of the cybercrime ecosystem into a more lethal threat.
“These capabilities provide attackers to obtain valuable information from the victim’s systems that can lead to big financial frauds which can make huge financial losses to victims,” SonicWall said.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.







![Sliver C2 Detected - 34[.]23[.]66[.]82:31337 8 Sliver C2](https://www.redpacketsecurity.com/wp-content/uploads/2024/02/Sliver-C2-300x142.jpg)

![LockBit 3.0 Ransomware Victim: contest[.]omg 14 image 11](https://www.redpacketsecurity.com/wp-content/uploads/2022/06/image-11-300x142.png)