Daily Vulnerability Trends: Sun Jan 29 2023
| CVE NAME | CVE Description |
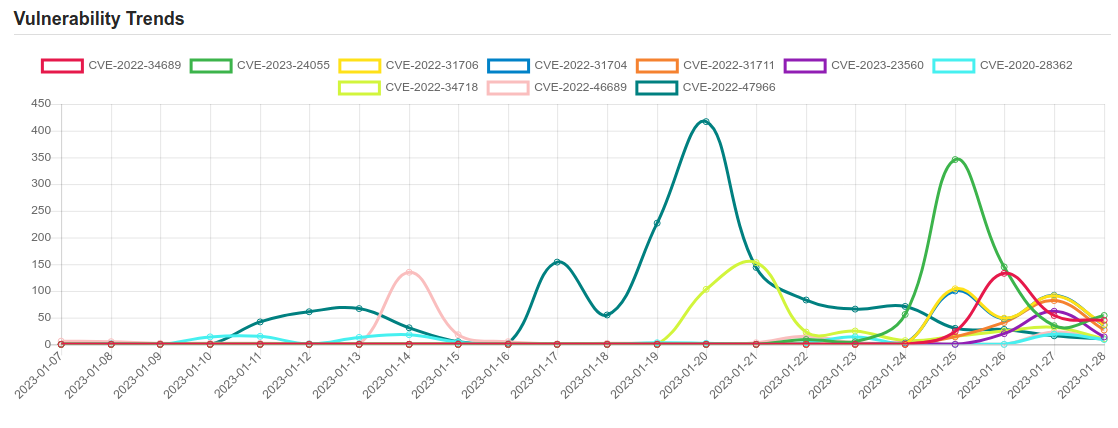
| CVE-2020-28362 | Go before 1.14.12 and 1.15.x before 1.15.4 allows Denial of Service. |
| CVE-2022-34718 | Windows TCP/IP Remote Code Execution Vulnerability. |
| CVE-2022-46689 | A race condition was addressed with additional validation. This issue is fixed in tvOS 16.2, macOS Monterey 12.6.2, macOS Ventura 13.1, macOS Big Sur 11.7.2, iOS 15.7.2 and iPadOS 15.7.2, iOS 16.2 and iPadOS 16.2, watchOS 9.2. An app may be able to execute arbitrary code with kernel privileges. |
| CVE-2022-47966 | Multiple Zoho ManageEngine on-premise products, such as ServiceDesk Plus through 14003, allow remote code execution due to use of Apache xmlsec (aka XML Security for Java) 1.4.1, because the xmlsec XSLT features, by design in that version, make the application responsible for certain security protections, and the ManageEngine applications did not provide those protections. |
| CVE-2022-23529 | ** REJECT ** DO NOT USE THIS CANDIDATE NUMBER. ConsultIDs: none. Reason: The issue is not a vulnerability. Notes: none. |
| CVE-2023-0297 | Code Injection in GitHub repository pyload/pyload prior to 0.5.0b3.dev31. |
| CVE-2022-45770 | Improper input validation in driver adgnetworkwfpdrv.sys in Adguard For Windows x86 up to version 7.11 allows attacker to gain local privileges escalation. |
| CVE-2021-35394 | Realtek Jungle SDK version v2.x up to v3.4.14B provides a diagnostic tool called ‘MP Daemon’ that is usually compiled as ‘UDPServer’ binary. The binary is affected by multiple memory corruption vulnerabilities and an arbitrary command injection vulnerability that can be exploited by remote unauthenticated attackers. |
| CVE-2022-3094 | Sending a flood of dynamic DNS updates may cause `named` to allocate large amounts of memory. This, in turn, may cause `named` to exit due to a lack of free memory. We are not aware of any cases where this has been exploited. Memory is allocated prior to the checking of access permissions (ACLs) and is retained during the processing of a dynamic update from a client whose access credentials are accepted. Memory allocated to clients that are not permitted to send updates is released immediately upon rejection. The scope of this vulnerability is limited therefore to trusted clients who are permitted to make dynamic zone changes. If a dynamic update is REFUSED, memory will be released again very quickly. Therefore it is only likely to be possible to degrade or stop `named` by sending a flood of unaccepted dynamic updates comparable in magnitude to a query flood intended to achieve the same detrimental outcome. BIND 9.11 and earlier branches are also affected, but through exhaustion of internal resources rather than memory constraints. This may reduce performance but should not be a significant problem for most servers. Therefore we don’t intend to address this for BIND versions prior to BIND 9.16. This issue affects BIND 9 versions 9.16.0 through 9.16.36, 9.18.0 through 9.18.10, 9.19.0 through 9.19.8, and 9.16.8-S1 through 9.16.36-S1. |
| CVE-2023-0210 | No description provided |
| CVE-2023-23504 | No description provided |
| CVE-2023-22960 | Lexmark products through 2023-01-10 have Improper Control of Interaction Frequency. |
| CVE-2020-6418 | Type confusion in V8 in Google Chrome prior to 80.0.3987.122 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. |
| CVE-2022-27510 | Unauthorized access to Gateway user capabilities |
| CVE-2022-34689 | Windows CryptoAPI Spoofing Vulnerability. |
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below
To keep up to date follow us on the below channels.






