Daily Vulnerability Trends: Sat Oct 21 2023
| CVE NAME | CVE Description |
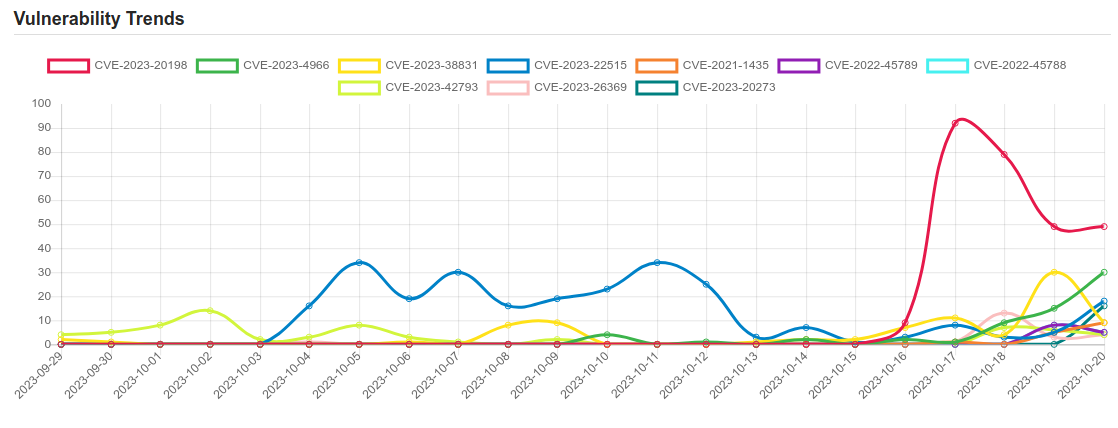
| CVE-2023-20198 | Cisco is aware of active exploitation of a previously unknown vulnerability in the web UI feature of Cisco IOS XE Software when exposed to the internet or to untrusted networks. This vulnerability allows a remote, unauthenticated attacker to create an account on an affected system with privilege level 15 access. The attacker can then use that account to gain control of the affected system. For steps to close the attack vector for this vulnerability, see the Recommendations section of this advisory Cisco will provide updates on the status of this investigation and when a software patch is available. |
| CVE-2023-4966 | Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. |
| CVE-2022-45789 | A CWE-294: Authentication Bypass by Capture-replay vulnerability exists that could cause execution of unauthorized Modbus functions on the controller when hijacking an authenticated Modbus session. Affected Products: EcoStruxure Control Expert (All Versions), EcoStruxure Process Expert (All Versions), Modicon M340 CPU – part numbers BMXP34* (All Versions), Modicon M580 CPU – part numbers BMEP* and BMEH* (All Versions), Modicon M580 CPU Safety – part numbers BMEP58*S and BMEH58*S (All Versions) |
| CVE-2022-45788 | A CWE-754: Improper Check for Unusual or Exceptional Conditions vulnerability exists that could cause arbitrary code execution, denial of service and loss of confidentiality & integrity when a malicious project file is loaded onto the controller. Affected Products: EcoStruxure Control Expert (All Versions), EcoStruxure Process Expert (All Versions), Modicon M340 CPU – part numbers BMXP34* (All Versions), Modicon M580 CPU – part numbers BMEP* and BMEH* (All Versions), Modicon M580 CPU Safety – part numbers BMEP58*S and BMEH58*S (All Versions), Modicon Momentum Unity M1E Processor – 171CBU* (All Versions), Modicon MC80 – BMKC80 (All Versions), Legacy Modicon Quantum – 140CPU65* and Premium CPUs – TSXP57* (All Versions) |
| CVE-2023-42793 | In JetBrains TeamCity before 2023.05.4 authentication bypass leading to RCE on TeamCity Server was possible |
| CVE-2023-26369 | Acrobat Reader versions 23.003.20284 (and earlier), 20.005.30516 (and earlier) and 20.005.30514 (and earlier) are affected by an out-of-bounds write vulnerability that could result in arbitrary code execution in the context of the current user. Exploitation of this issue requires user interaction in that a victim must open a malicious file. |
| CVE-2023-20273 | No description provided |
| CVE-2023-38545 | This flaw makes curl overflow a heap based buffer in the SOCKS5 proxy handshake. When curl is asked to pass along the host name to the SOCKS5 proxy to allow that to resolve the address instead of it getting done by curl itself, the maximum length that host name can be is 255 bytes. If the host name is detected to be longer, curl switches to local name resolving and instead passes on the resolved address only. Due to this bug, the local variable that means “let the host resolve the name” could get the wrong value during a slow SOCKS5 handshake, and contrary to the intention, copy the too long host name to the target buffer instead of copying just the resolved address there. The target buffer being a heap based buffer, and the host name coming from the URL that curl has been told to operate with. |
| CVE-2023-34051 | VMware Aria Operations for Logs contains an authentication bypass vulnerability. An unauthenticated, malicious actor can inject files into the operating system of an impacted appliance which can result in remote code execution. |
| CVE-2023-45802 | No description provided |
| CVE-2023-35182 | The SolarWinds Access Rights Manager was susceptible to Remote Code Execution Vulnerability. This vulnerability can be abused by unauthenticated users on SolarWinds ARM Server. |
| CVE-2023-4069 | Type Confusion in V8 in Google Chrome prior to 115.0.5790.170 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: High) |
| CVE-2023-44487 | The HTTP/2 protocol allows a denial of service (server resource consumption) because request cancellation can reset many streams quickly, as exploited in the wild in August through October 2023. |
| CVE-2023-33297 | Bitcoin Core before 24.1, when debug mode is not used, allows attackers to cause a denial of service (e.g., CPU consumption) because draining the inventory-to-send queue is inefficient, as exploited in the wild in May 2023. |
| CVE-2023-35187 | The SolarWinds Access Rights Manager was susceptible to a Directory Traversal Remote Code Vulnerability. This vulnerability allows an unauthenticated user to achieve the Remote Code Execution. |
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![GoPhish Login Page Detected - 54[.]66[.]160[.]126:443 3 gophish](https://www.redpacketsecurity.com/wp-content/uploads/2024/04/gophish-300x90.png)

