Daily Vulnerability Trends: Fri Nov 18 2022
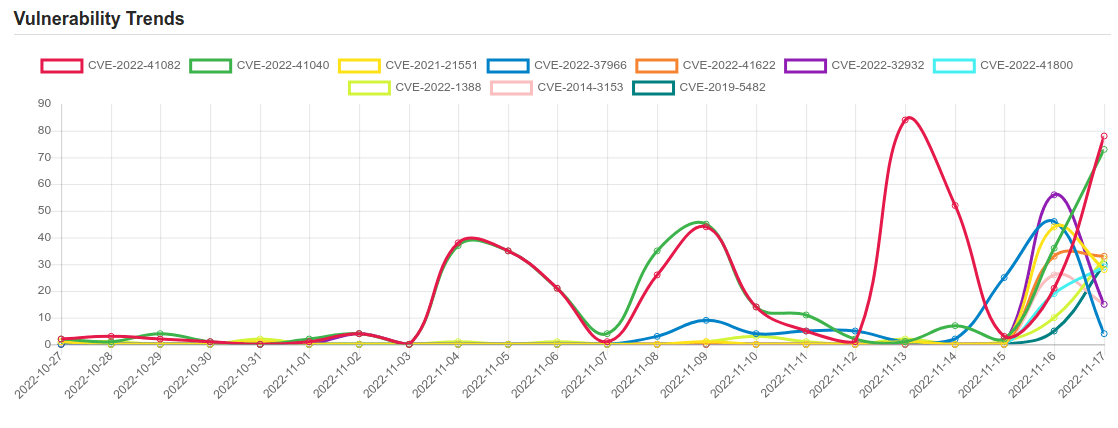
| CVE NAME | CVE Description |
| CVE-2019-5482 | Heap buffer overflow in the TFTP protocol handler in cURL 7.19.4 to 7.65.3. |
| CVE-2022-24086 | Adobe Commerce versions 2.4.3-p1 (and earlier) and 2.3.7-p2 (and earlier) are affected by an improper input validation vulnerability during the checkout process. Exploitation of this issue does not require user interaction and could result in arbitrary code execution. |
| CVE-2022-35803 | Windows Common Log File System Driver Elevation of Privilege Vulnerability. This CVE ID is unique from CVE-2022-37969. |
| CVE-2022-43781 | There is a command injection vulnerability using environment variables in Bitbucket Server and Data Center. An attacker with permission to control their username can exploit this issue to execute arbitrary code on the system. This vulnerability can be unauthenticated if the Bitbucket Server and Data Center instance has enabled “Allow public signup”. |
| CVE-2021-42321 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2022-32929 | A permissions issue was addressed with additional restrictions. This issue is fixed in iOS 15.7.1 and iPadOS 15.7.1, iOS 15.7 and iPadOS 15.7, iOS 16.1 and iPadOS 16. An app may be able to access iOS backups. |
| CVE-2021-38819 | A SQL injection vulnerability exits on the Simple Image Gallery System 1.0 application through “id” parameter on the album page. |
| CVE-2022-45047 | Class org.apache.sshd.server.keyprovider.SimpleGeneratorHostKeyProvider in Apache MINA SSHD <= 2.9.1 uses Java deserialization to load a serialized java.security.PrivateKey. The class is one of several implementations that an implementor using Apache MINA SSHD can choose for loading the host keys of an SSH server. |
| CVE-2021-25369 | An improper access control vulnerability in sec_log file prior to SMR MAR-2021 Release 1 exposes sensitive kernel information to userspace. |
| CVE-2021-25370 | An incorrect implementation handling file descriptor in dpu driver prior to SMR Mar-2021 Release 1 results in memory corruption leading to kernel panic. |
| CVE-2021-25337 | Improper access control in clipboard service in Samsung mobile devices prior to SMR Mar-2021 Release 1 allows untrusted applications to read or write certain local files. |
| CVE-2022-41082 | Microsoft Exchange Server Remote Code Execution Vulnerability. |
| CVE-2022-41040 | Microsoft Exchange Server Elevation of Privilege Vulnerability. |
| CVE-2021-21551 | Dell dbutil_2_3.sys driver contains an insufficient access control vulnerability which may lead to escalation of privileges, denial of service, or information disclosure. Local authenticated user access is required. |
| CVE-2022-37966 | Windows Kerberos RC4-HMAC Elevation of Privilege Vulnerability. |
| CVE-2022-32932 | The issue was addressed with improved memory handling. This issue is fixed in iOS 15.7.1 and iPadOS 15.7.1, iOS 16.1 and iPadOS 16, watchOS 9.1. An app may be able to execute arbitrary code with kernel privileges. |
| CVE-2022-1388 | On F5 BIG-IP 16.1.x versions prior to 16.1.2.2, 15.1.x versions prior to 15.1.5.1, 14.1.x versions prior to 14.1.4.6, 13.1.x versions prior to 13.1.5, and all 12.1.x and 11.6.x versions, undisclosed requests may bypass iControl REST authentication. Note: Software versions which have reached End of Technical Support (EoTS) are not evaluated |
| CVE-2014-3153 | The futex_requeue function in kernel/futex.c in the Linux kernel through 3.14.5 does not ensure that calls have two different futex addresses, which allows local users to gain privileges via a crafted FUTEX_REQUEUE command that facilitates unsafe waiter modification. |
| CVE-2022-41622 | F5 BIG-IP and BIG-IQ cross-site request forgery | CVE-2022-41622 |
| CVE-2022-41800 | F5 BIG-IP security bypass | CVE-2022-41800 |
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.






