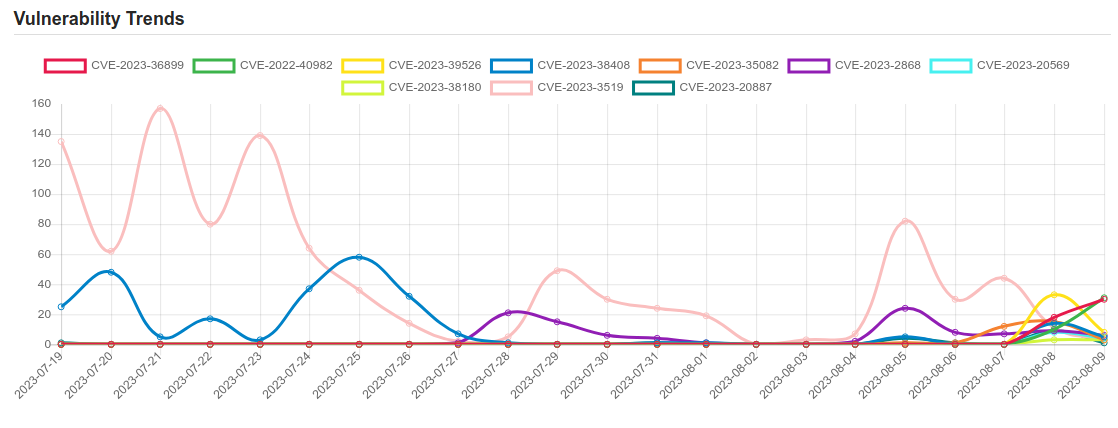
Daily Vulnerability Trends: Thu Aug 10 2023
| CVE NAME | CVE Description |
| CVE-2023-20569 | A side channel vulnerability on some of the AMD CPUs may allow an attacker to influence the return address prediction. This may result in speculative execution at an attacker-controlled?address, potentially leading to information disclosure. |
| CVE-2023-3519 | Unauthenticated remote code execution |
| CVE-2023-20887 | Aria Operations for Networks contains a command injection vulnerability. A malicious actor with network access to VMware Aria Operations for Networks may be able to perform a command injection attack resulting in remote code execution. |
| CVE-2017-11882 | Microsoft Office 2007 Service Pack 3, Microsoft Office 2010 Service Pack 2, Microsoft Office 2013 Service Pack 1, and Microsoft Office 2016 allow an attacker to run arbitrary code in the context of the current user by failing to properly handle objects in memory, aka “Microsoft Office Memory Corruption Vulnerability”. This CVE ID is unique from CVE-2017-11884. |
| CVE-2023-39143 | PaperCut NG and PaperCut MF before 22.1.3 on Windows allow path traversal, enabling attackers to upload, read, or delete arbitrary files. This leads to remote code execution when external device integration is enabled (a very common configuration). |
| CVE-2023-36884 | Windows Search Remote Code Execution Vulnerability |
| CVE-2023-34034 | Using “**” as a pattern in Spring Security configuration for WebFlux creates a mismatch in pattern matching between Spring Security and Spring WebFlux, and the potential for a security bypass. |
| CVE-2023-29320 | No description provided |
| CVE-2023-38182 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-35388 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-28229 | Windows CNG Key Isolation Service Elevation of Privilege Vulnerability |
| CVE-2023-35385 | Microsoft Message Queuing Remote Code Execution Vulnerability |
| CVE-2023-39526 | PrestaShop is an open source e-commerce web application. Versions prior to 1.7.8.10, 8.0.5, and 8.1.1 are vulnerable to remote code execution through SQL injection and arbitrary file write in the back office. Versions 1.7.8.10, 8.0.5, and 8.1.1 contain a patch. There are no known workarounds. |
| CVE-2023-38408 | The PKCS#11 feature in ssh-agent in OpenSSH before 9.3p2 has an insufficiently trustworthy search path, leading to remote code execution if an agent is forwarded to an attacker-controlled system. (Code in /usr/lib is not necessarily safe for loading into ssh-agent.) NOTE: this issue exists because of an incomplete fix for CVE-2016-10009. |
| CVE-2023-35082 | No description provided |
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

