Daily Vulnerability Trends: Sat Aug 26 2023
| CVE NAME | CVE Description |
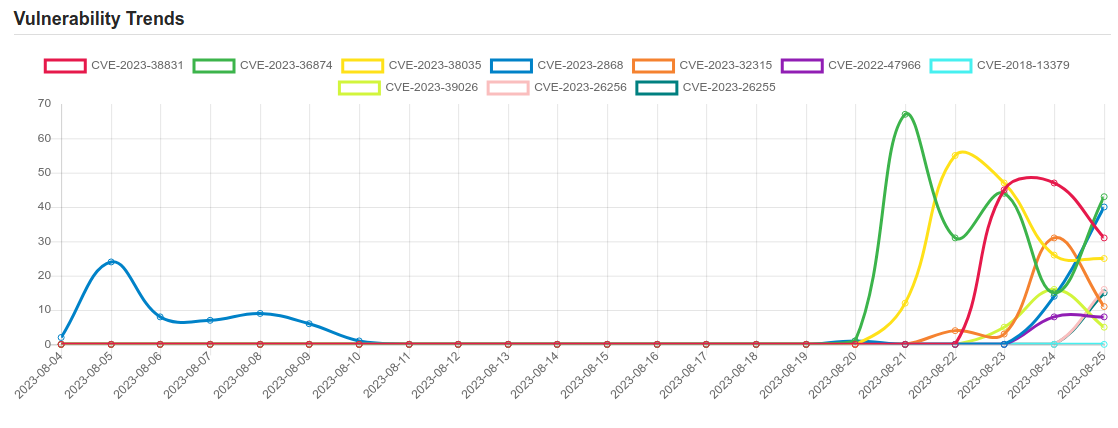
| CVE-2023-38035 | A security vulnerability in MICS Admin Portal in Ivanti MobileIron Sentry versions 9.18.0 and below, which may allow an attacker to bypass authentication controls on the administrative interface due to an insufficiently restrictive Apache HTTPD configuration. |
| CVE-2023-26255 | An unauthenticated path traversal vulnerability affects the “STAGIL Navigation for Jira – Menu & Themes” plugin before 2.0.52 for Jira. By modifying the fileName parameter to the snjCustomDesignConfig endpoint, it is possible to traverse and read the file system. |
| CVE-2023-30943 | The vulnerability was found Moodle which exists because the application allows a user to control path of the older to create in TinyMCE loaders. A remote user can send a specially crafted HTTP request and create arbitrary folders on the system. |
| CVE-2023-41106 | No description provided |
| CVE-2023-24489 | A vulnerability has been discovered in the customer-managed ShareFile storage zones controller which, if exploited, could allow an unauthenticated attacker to remotely compromise the customer-managed ShareFile storage zones controller. |
| CVE-2023-32563 | An unauthenticated attacker could achieve the code execution through a RemoteControl server. |
| CVE-2023-39141 | webui-aria2 commit 4fe2e was discovered to contain a path traversal vulnerability. |
| CVE-2020-19909 | Integer overflow vulnerability in tool_operate.c in curl 7.65.2 via crafted value as the retry delay. |
| CVE-2022-40982 | Information exposure through microarchitectural state after transient execution in certain vector execution units for some Intel(R) Processors may allow an authenticated user to potentially enable information disclosure via local access. |
| CVE-2022-41099 | BitLocker Security Feature Bypass Vulnerability |
| CVE-2023-36874 | Windows Error Reporting Service Elevation of Privilege Vulnerability |
| CVE-2023-2868 | A remote command injection vulnerability exists in the Barracuda Email Security Gateway (appliance form factor only) product effecting versions 5.1.3.001-9.2.0.006. The vulnerability arises out of a failure to comprehensively sanitize the processing of .tar file (tape archives). The vulnerability stems from incomplete input validation of a user-supplied .tar file as it pertains to the names of the files contained within the archive. As a consequence, a remote attacker can specifically format these file names in a particular manner that will result in remotely executing a system command through Perl’s qx operator with the privileges of the Email Security Gateway product. This issue was fixed as part of BNSF-36456 patch. This patch was automatically applied to all customer appliances. |
| CVE-2023-32315 | Openfire is an XMPP server licensed under the Open Source Apache License. Openfire’s administrative console, a web-based application, was found to be vulnerable to a path traversal attack via the setup environment. This permitted an unauthenticated user to use the unauthenticated Openfire Setup Environment in an already configured Openfire environment to access restricted pages in the Openfire Admin Console reserved for administrative users. This vulnerability affects all versions of Openfire that have been released since April 2015, starting with version 3.10.0. The problem has been patched in Openfire release 4.7.5 and 4.6.8, and further improvements will be included in the yet-to-be released first version on the 4.8 branch (which is expected to be version 4.8.0). Users are advised to upgrade. If an Openfire upgrade isn’t available for a specific release, or isn’t quickly actionable, users may see the linked github advisory (GHSA-gw42-f939-fhvm) for mitigation advice. |
| CVE-2022-47966 | Multiple Zoho ManageEngine on-premise products, such as ServiceDesk Plus through 14003, allow remote code execution due to use of Apache xmlsec (aka XML Security for Java) 1.4.1, because the xmlsec XSLT features, by design in that version, make the application responsible for certain security protections, and the ManageEngine applications did not provide those protections. |
| CVE-2018-13379 | An Improper Limitation of a Pathname to a Restricted Directory (“Path Traversal”) in Fortinet FortiOS 6.0.0 to 6.0.4, 5.6.3 to 5.6.7 and 5.4.6 to 5.4.12 and FortiProxy 2.0.0, 1.2.0 to 1.2.8, 1.1.0 to 1.1.6, 1.0.0 to 1.0.7 under SSL VPN web portal allows an unauthenticated attacker to download system files via special crafted HTTP resource requests. |
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![Abyss Ransomware Victim: woldae[.]com 3 image 1](https://www.redpacketsecurity.com/wp-content/uploads/2023/05/image-1-300x132.png)
![Sliver C2 Detected - 135[.]181[.]205[.]15:31337 5 Sliver C2](https://www.redpacketsecurity.com/wp-content/uploads/2024/02/Sliver-C2-300x142.jpg)
![CovenantC2 Detected - 45[.]41[.]187[.]220:7443 7 covenant](https://www.redpacketsecurity.com/wp-content/uploads/2024/02/covenant-300x87.png)
