Daily Vulnerability Trends: Mon Sep 19 2022
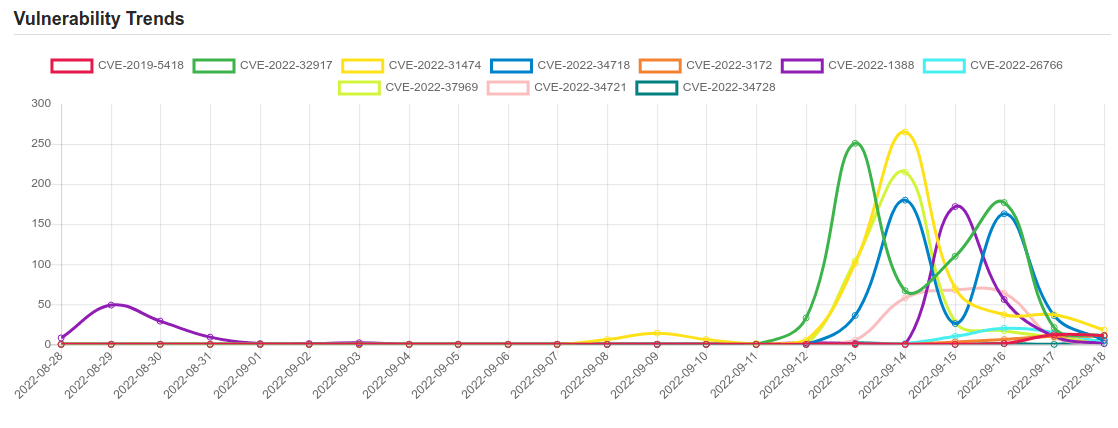
| CVE NAME | CVE Description |
| CVE-2022-34728 | Windows Graphics Component Information Disclosure Vulnerability. This CVE ID is unique from CVE-2022-35837, CVE-2022-38006. |
| CVE-2022-3173 | Improper Authentication in GitHub repository snipe/snipe-it prior to 6.0.10. |
| CVE-2022-26763 | An out-of-bounds access issue was addressed with improved bounds checking. This issue is fixed in tvOS 15.5, iOS 15.5 and iPadOS 15.5, Security Update 2022-004 Catalina, watchOS 8.6, macOS Big Sur 11.6.6, macOS Monterey 12.4. A malicious application may be able to execute arbitrary code with system privileges. |
| CVE-2022-39960 | The Netic Group Export add-on before 1.0.3 for Atlassian Jira does not perform authorization checks. This might allow an unauthenticated user to export all groups from the Jira instance by making a groupexport_download=true request to a plugins/servlet/groupexportforjira/admin/ URI. |
| CVE-2022-37706 | No description provided |
| CVE-2022-3231 | Cross-site Scripting (XSS) – Stored in GitHub repository librenms/librenms prior to 22.9.0. |
| CVE-2022-36203 | Doctor’s Appointment System 1.0 is vulnerable to Cross Site Scripting (XSS) via the admin panel. In addition, it leads to takeover the administrator account by stealing the cookie via XSS. |
| CVE-2022-36201 | Doctor’s Appointment System v1.0 is vulnerable to Blind SQLi via settings.php. |
| CVE-2022-40766 | Modern Campus Omni CMS (formerly OU Campus) 10.2.4 allows login-page SQL injection via a ‘” OR 1 = 1 — – , |
| CVE-2022-36202 | Doctor’s Appointment System1.0 is vulnerable to Incorrect Access Control via edoc/patient/settings.php. The settings.php is affected by Broken Access Control (IDOR) via id= parameter. |
| CVE-2022-37709 | Tesla Model 3 V11.0(2022.4.5.1 6b701552d7a6) Tesla mobile app v4.23 is vulnerable to Authentication Bypass by spoofing. Tesla Model 3’s Phone Key authentication is vulnerable to Man-in-the-middle attacks in the BLE channel. It allows attackers to open a door and drive the car away by leveraging access to a legitimate Phone Key. |
| CVE-2019-5418 | There is a File Content Disclosure vulnerability in Action View <5.2.2.1, <5.1.6.2, <5.0.7.2, <4.2.11.1 and v3 where specially crafted accept headers can cause contents of arbitrary files on the target system's filesystem to be exposed. |
| CVE-2022-32917 | No description provided |
| CVE-2022-31474 | No description provided |
| CVE-2022-34718 | Windows TCP/IP Remote Code Execution Vulnerability. |
| CVE-2022-3172 | No description provided |
| CVE-2022-1388 | On F5 BIG-IP 16.1.x versions prior to 16.1.2.2, 15.1.x versions prior to 15.1.5.1, 14.1.x versions prior to 14.1.4.6, 13.1.x versions prior to 13.1.5, and all 12.1.x and 11.6.x versions, undisclosed requests may bypass iControl REST authentication. Note: Software versions which have reached End of Technical Support (EoTS) are not evaluated |
| CVE-2022-26766 | A certificate parsing issue was addressed with improved checks. This issue is fixed in tvOS 15.5, iOS 15.5 and iPadOS 15.5, Security Update 2022-004 Catalina, watchOS 8.6, macOS Big Sur 11.6.6, macOS Monterey 12.4. A malicious app may be able to bypass signature validation. |
| CVE-2022-37969 | Windows Common Log File System Driver Elevation of Privilege Vulnerability. This CVE ID is unique from CVE-2022-35803. |
| CVE-2022-34721 | Windows Internet Key Exchange (IKE) Protocol Extensions Remote Code Execution Vulnerability. This CVE ID is unique from CVE-2022-34722. |
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below
To keep up to date follow us on the below channels.






![Black Basta Ransomware Victim: thelawrencegroup[.]com_privat 11 Basta](https://www.redpacketsecurity.com/wp-content/uploads/2022/06/Basta-300x97.png)
