Exploit released for critical VMware SSH auth bypass vulnerability

Proof-of-concept exploit code has been released for a critical SSH authentication bypass vulnerability in VMware’s Aria Operations for Networks analysis tool (formerly known as vRealize Network Insight).
The flaw (tracked as CVE-2023-34039) was found by security analysts at ProjectDiscovery Research and patched by VMware on Wednesday with the release of version 6.11.
Successful exploitation enables remote attackers to bypass SSH authentication on unpatched appliances and access the tool’s command line interface in low-complexity attacks that don’t require user interaction because of what the company describes as “a lack of unique cryptographic key generation.”
To mitigate the flaw, VMware “highly recommends” applying security patches for Aria Operations for Networks versions 6.2 / 6.3 / 6.4 / 6.5.1 / 6.6 / 6.7 / 6.8 / 6.9 / 6.10 available on this support document.
Today, VMware confirmed that CVE-2023-34039 exploit code has been published online, two days after disclosing the critical security bug.
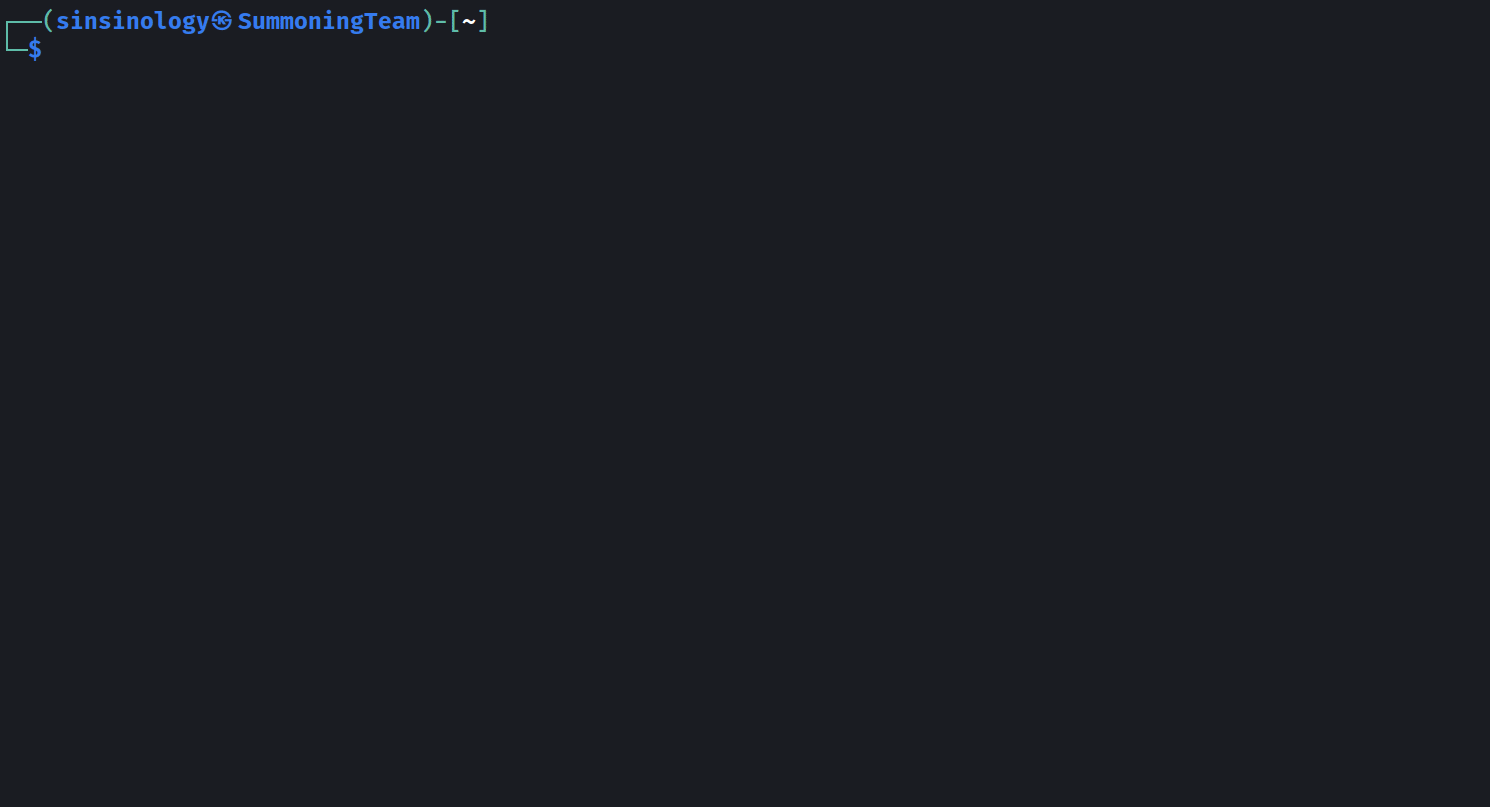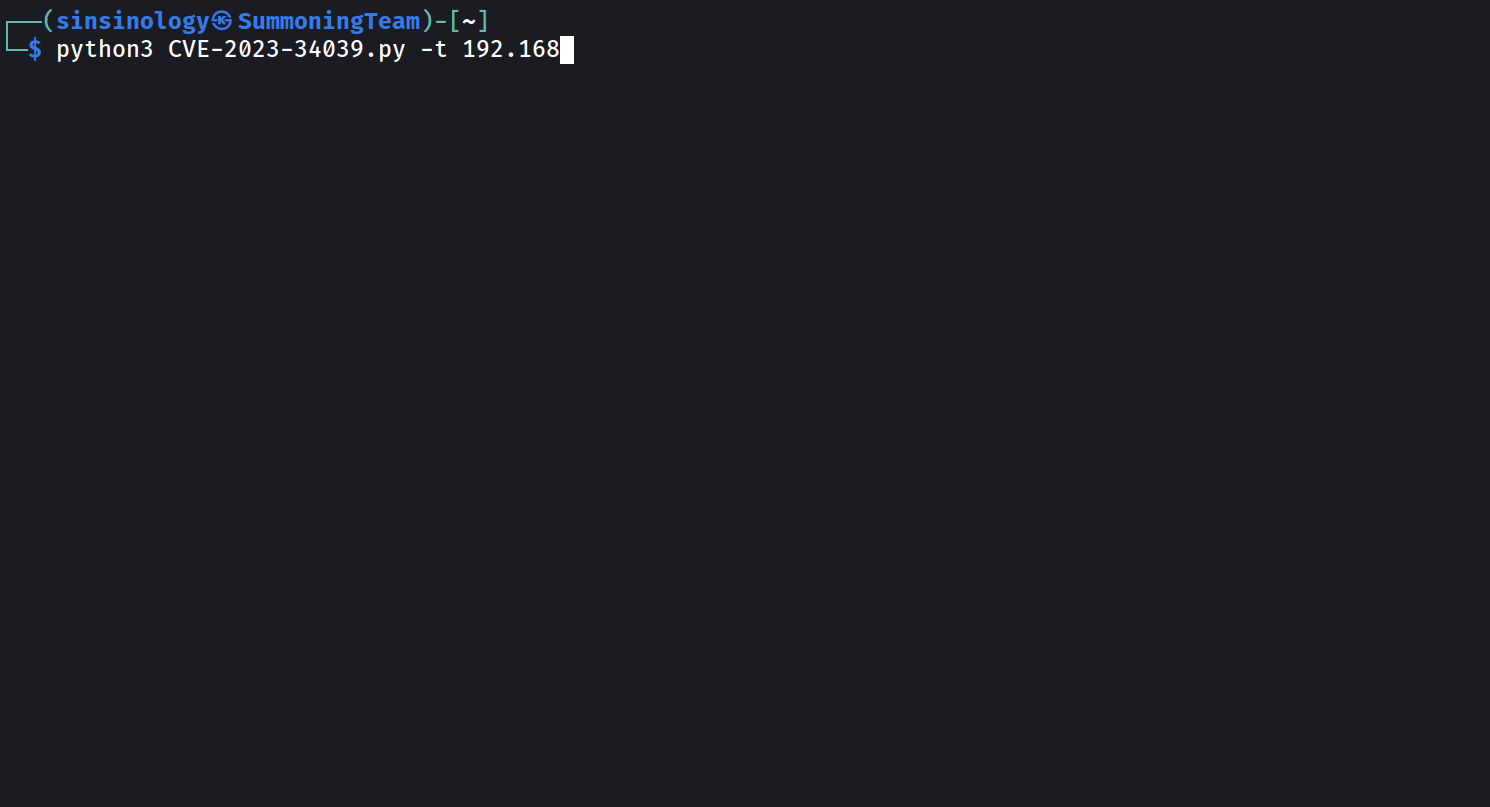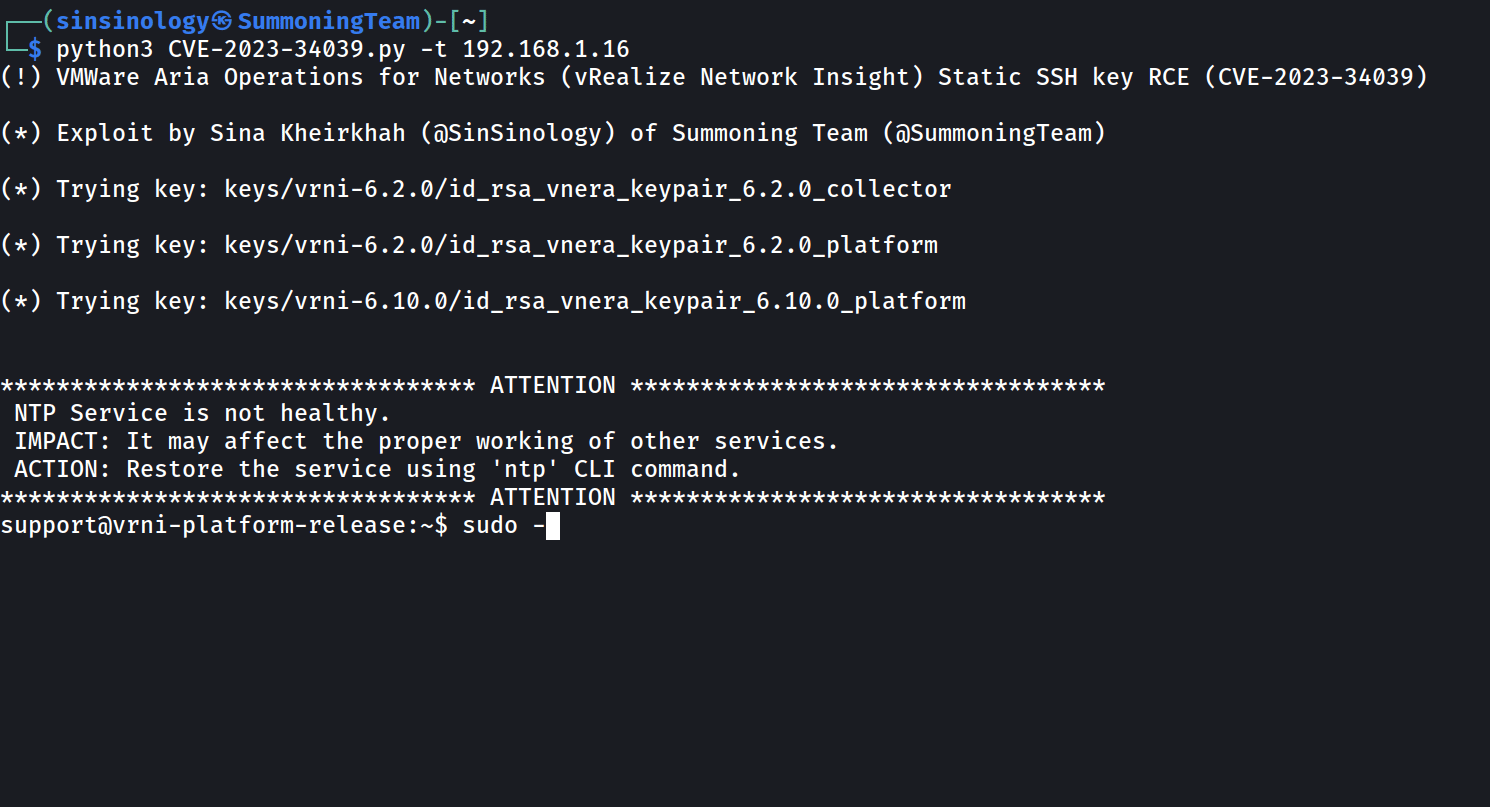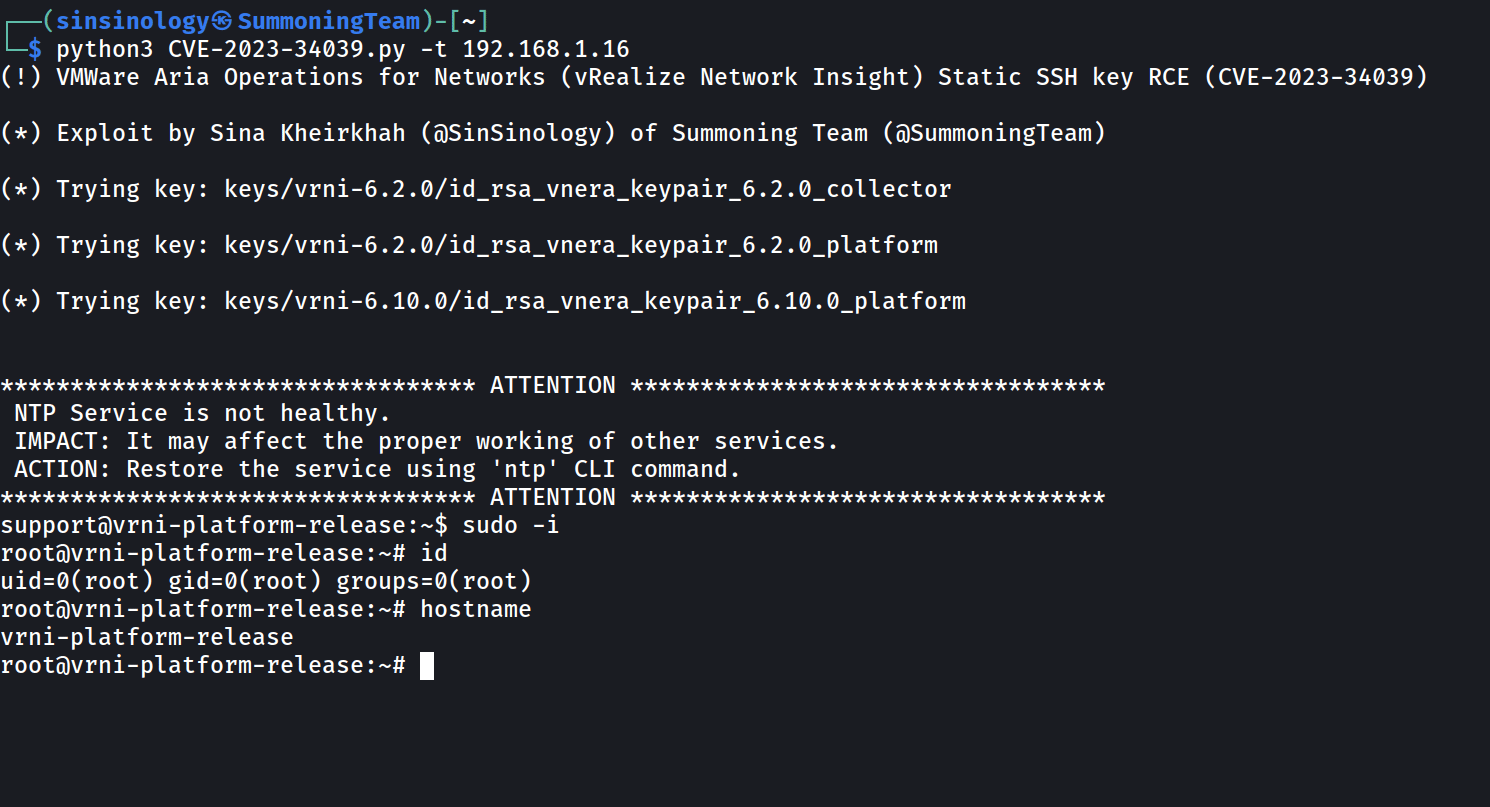
The proof-of-concept (PoC) exploit targets all Aria Operations for Networks versions from 6.0 to 6.10, and it was developed and released by Summoning Team vulnerability researcher Sina Kheirkhah.
Kheirkhah said that the root cause of the issue are hardcoded SSH keys left after VMware forgot to regenerate SSH authorized keys.
“Each version of VMware’s Aria Operations for Networks has a unique SSH key. To create a fully functional exploit, I had to collect all the keys from different versions of this product,” Kheirkhah said.

VMware also patched an arbitrary file write vulnerability this week (CVE-2023-20890), which allows attackers to gain remote code execution after obtaining admin access to the targeted appliance (the CVE-2023-34039 PoC could let them get root permissions following successful attacks).
In July, VMware warned customers that exploit code was released online for a critical RCE flaw (CVE-2023-20864) in the VMware Aria Operations for Logs analysis tool, patched in April.
One month earlier, the company issued another alert regarding the active exploitation of another Network Insight critical bug (CVE-2023-20887) that can lead to remote command execution attacks.
CISA ordered U.S. federal agencies to patch their systems against CVE-2023-20887 by July 13th after adding it to its list of known exploited vulnerabilities.
In light of this, admins are strongly recommended to update their Aria Operations for Networks appliances to the latest version as soon as possible as a preemptive measure against potential incoming attacks.
While the number of VMware vRealize instances exposed online is relatively low, it aligns with the intended use of these appliances on internal networks.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

