Fortinet Warns Of New Fortisiem Rce Bugs In Confusing Disclosure

Fortinet is warning of two new unpatched patch bypasses for a critical remote code execution vulnerability in FortiSIEM, Fortinet’s SIEM solution.
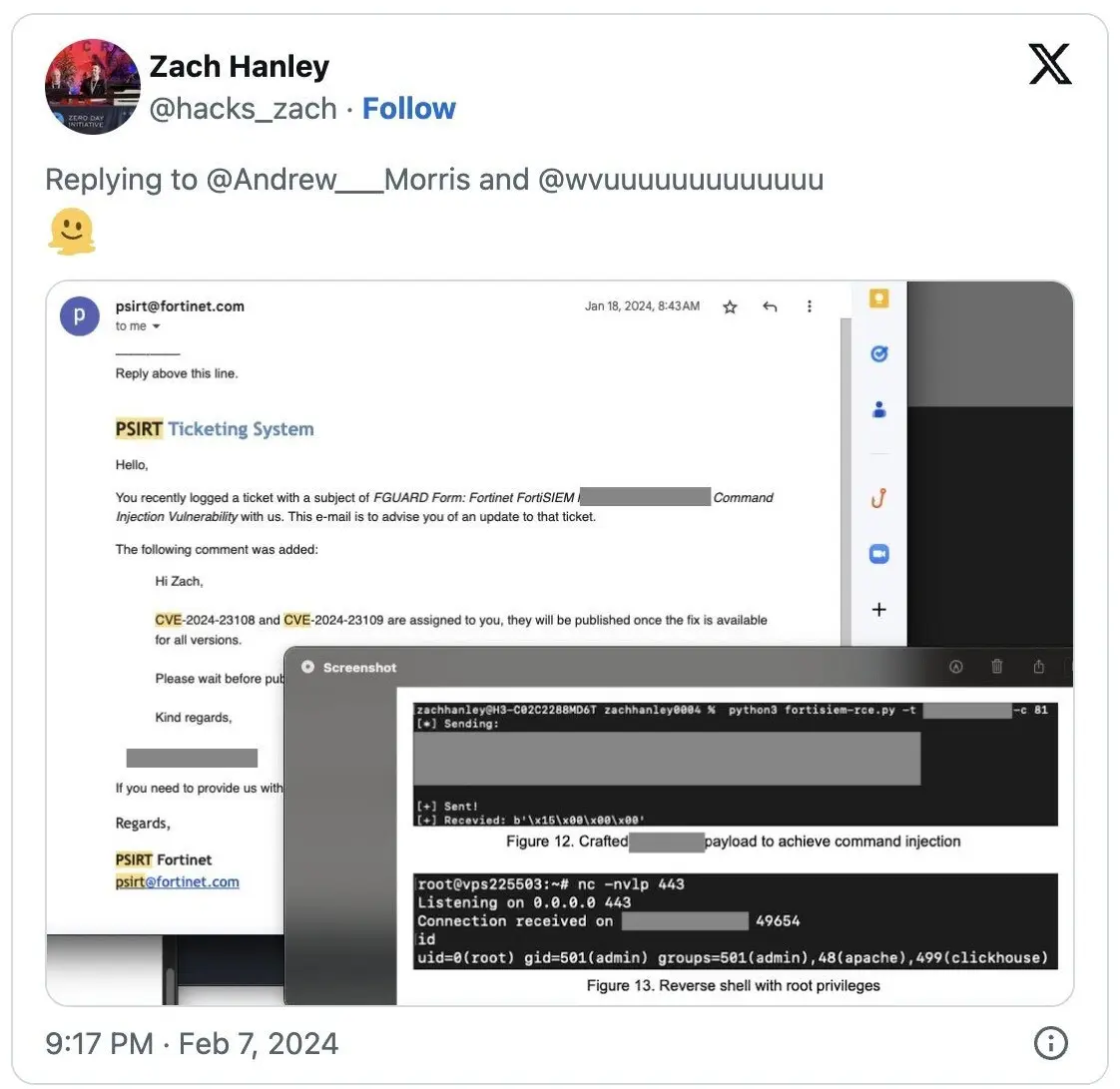
Fortinet added the two new vulnerabilities tracked as CVE-2024-23108 and CVE-2024-23109 to the original advisory for the CVE-2023-34992 flaw in a very confusing update.
Earlier today, BleepingComputer published an article that the CVEs were released by mistake after being told by Fortinet that they were duplicates of the original CVE-2023-34992.
“In this instance, due to an issue with the API which we are currently investigating, rather than an edit, this resulted in two new CVEs being created, duplicates of the original CVE-2023-34992,” Fortinet told BleepingComputer.
“There is no new vulnerability published for FortiSIEM so far in 2024, this is a system level error and we are working to rectify and withdraw the erroneous entries.”
However, it turns out that CVE-2024-23108 and CVE-2024-23109 are actually patch bypasses for the CVE-2023-34992 flaw discovered by Horizon3 vulnerability expert Zach Hanley.
On X, Zach stated that the new CVEs are patch bypasses for CVE-2023-34992, and the new IDs were assigned to him by Fortinet.
After contacting Fortinet once again, we were told their previous statement was “misstated” and that the two new CVEs are variants of the original flaw.
“The PSIRT team followed its process to add two similar variants of the previous CVE (CVE-2023-34992), tracked as CVE-2024-23108 and CVE-2024-23109 to our public advisory FG-IR-23-130, which was published in October 2023. The two new CVEs share the exact same description and score as the initial one; in parallel we updated MITRE. A reminder pointing to the updated Advisory will be included for our customers on Tuesday when Fortinet publishes its monthly advisory.” – Fortinet.
These two new variants have the same description as the original flaw, allowing unauthenticated attackers to execute commands via specially crafted API requests.
“Multiple improper neutralization of special elements used in an OS Command vulnerability [CWE-78] in FortiSIEM supervisor may allow a remote unauthenticated attacker to execute unauthorized commands via crafted API requests,” reads the advisory.
While the original flaw, CVE-2023-34992, was fixed in a previous FortiSIEM release, the new variants will be fixed or have been fixed in the following versions:
- FortiSIEM version 7.1.2 or above
- Upcoming FortiSIEM version 7.2.0 or above
- Upcoming FortiSIEM version 7.0.3 or above
- Upcoming FortiSIEM version 6.7.9 or above
- Upcoming FortiSIEM version 6.6.5 or above
- Upcoming FortiSIEM version 6.5.3 or above
- Upcoming FortiSIEM version 6.4.4 or above
As this is a critical flaw, it is strongly advised that you upgrade to one of the above FortiSIEM versions as soon as they become available.
Fortinet flaws are commonly targeted by threat actors, including ransomware gangs, who use them to gain initial access to corporate networks, so patching quickly is crucial.
BleepingComputer asked Fortinet when the other versions will be released and will update this story when we receive a response.