Hackers Exploit 14 Year Old Cms Editor On Govt Edu Sites For Seo Poisoning

Threat actors are exploiting a CMS editor discontinued 14 years ago to compromise education and government entities worldwide to poison search results with malicious sites or scams.
Open redirects are when websites, whether intentionally or through a flaw, allow arbitrary redirection requests that take users from the original site to an external URL without adequate validation or security checks.
For example, if there was a URL at https://www.example.com/?redirect=<url> that redirects visitors to the specified URL, and anyone could modify that URL to a site of their choosing, it would be considered an open redirect.
Attackers abuse these open redirects to perform phishing attacks, distribute malware, or scam users while appearing to originate from legitimate domains. As the URLs are hosted on trusted domains, it may allow them to bypass URL filters used by security products.
Furthermore, search engine crawlers index the redirects and list them on Google Search results, making them an effective strategy for SEO poisoning campaigns, leveraging a trusted domain to rank malicious URLs higher for specific queries.
Because open redirect URLs do not host the malicious content directly but merely point to it, they can remain active and visible in search results for a long time until they are reported for takedown.
However, many companies, including Google and Microsoft, do not consider open redirects a flaw and may not fix them unless they lead to a more severe vulnerability.
Targeting outdated plugin
Cybersecurity researcher @g0njxa discovered the malicious redirect campaign after seeing Google Search results for ‘Free V Bucks’ (Fortnite in-game currency) generators hosted on university sites.
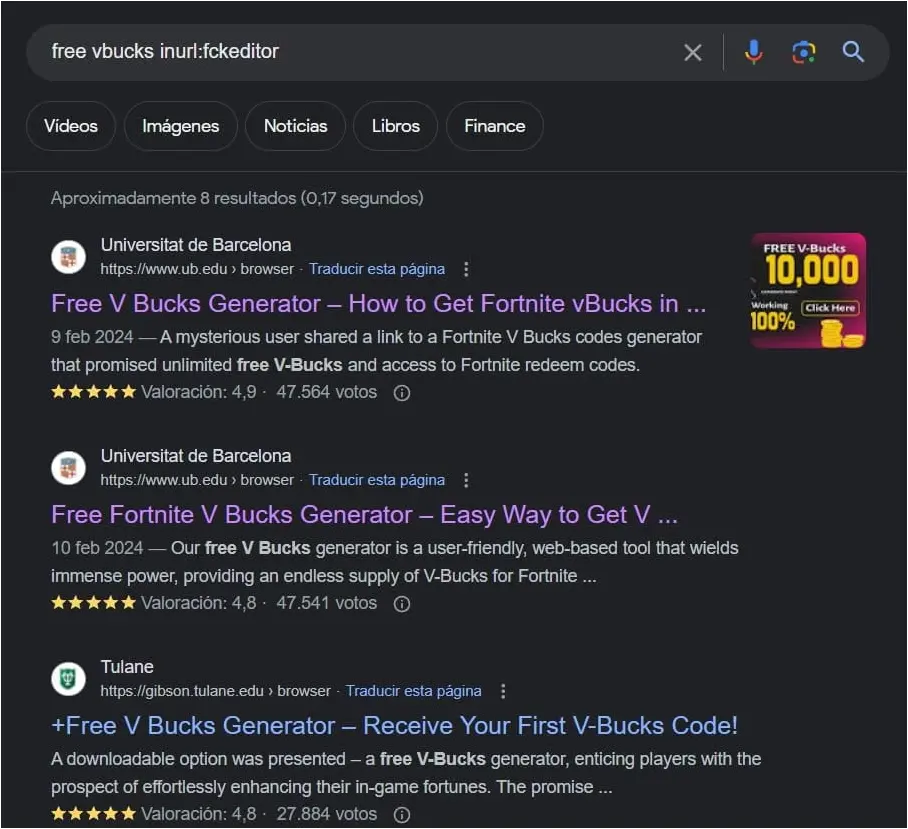
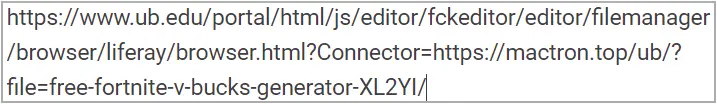
The open redirect requests used by the attackers in this campaign are related to FCKeditor, a once-popular web text editor that allows users to edit HTML content directly within a web page.
In 2009, FCKeditor was rebranded and significantly revamped, resulting in the launch of CKEditor, which uses a more modern codebase, offers enhanced usability and compatibility with contemporary web standards, and is also actively supported by its developer.
In a Twitter thread, g0njxa lists the various organizations targeted by this campaign, primarily targeting educational institutions, such as MIT, Columbia University, Universitat de Barcelona, Auburn University, University of Washington, Purdue, Tulane, Universidad Central del Ecuador, and the University of Hawaiʻi.
However, the campaign also targets government and corporate sites using the outdated FCKeditor plugin, including Virginia’s government site, Austin, Texas’s government site, Spain’s government site, and Yellow Pages Canada.
From BleepingComputer’s tests, we discovered that the compromised FCKeditor instances utilize a combination of static HTML pages and redirects to malicious sites.
The static HTML pages open under the legitimate domain and are used to poison the search engine with malicious results.
For example, one of the links in Google goes to the FCKeditor instance on the aum.edu site, where an HTML page pretends to be a news article about tinnitus remedies.
However, the article is designed to promote other content pages on the compromised FCKeditor instance installed on AUM’s website so that Google will index the pages. Once these pages are ranked in search engines, the threat actors will likely swap them out for redirects to malicious sites.
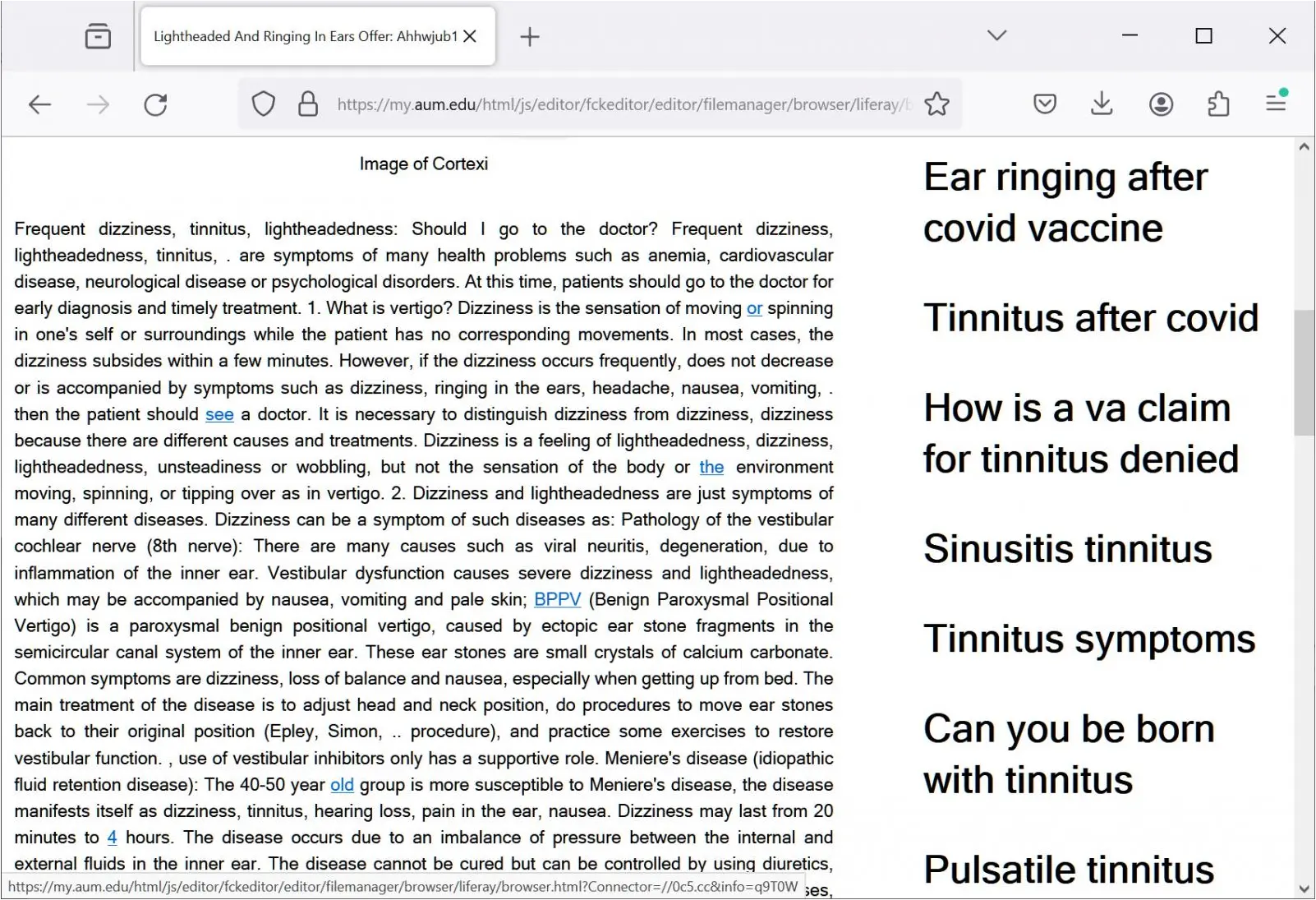
Source: BleepingComputer
Other URLs in this campaign will simply abuse FCKeditor to redirect visitors to scam sites, fake news articles, phishing pages, hacking assistance sites, or malicious browser extensions.
The software maker responded to the open redirects campaign report on X, saying that FCKeditor has been deprecated since 2010 and nobody should be using it anymore.
Unfortunately, it’s not uncommon to see university and government sites using software that has been discontinued for a long time, in this case, over 13 years.
In the past, we saw similar campaigns where threat actors abused open redirects on government sites to redirect users to fake OnlyFans and adult sites.