Hackers exploit Control Web Panel flaw to open reverse shells

Hackers are actively exploiting a critical vulnerability patched recently in Control Web Panel (CWP), a tool for managing servers formerly known as CentOS Web Panel.
The security issue is identified as CVE-2022-44877 and received a critical severity score of 9.8 out of 10 as it allows an attacker to execute code remotely without authentication.
Exploit code readily available
On January 3, researcher Numan Türle at Gais Cyber Security, who had reported the issue around October last year, published a proof-of-concept (PoC) exploit and a video showing how it works.
Three days later, security researchers noticed hackers exploiting the flaw to get remote access to unpatched systems and to find more vulnerable machines.
CWP version 0.9.8.1147 was released on October 25, 2022, to fix CVE-2022-44877, which affects previous versions of the panel.
A technical analysis of the PoC exploit code is available from CloudSek, which ran a search for CWP servers on the Shodan platform and found more than 400,000 CWP instances accessible over the internet.
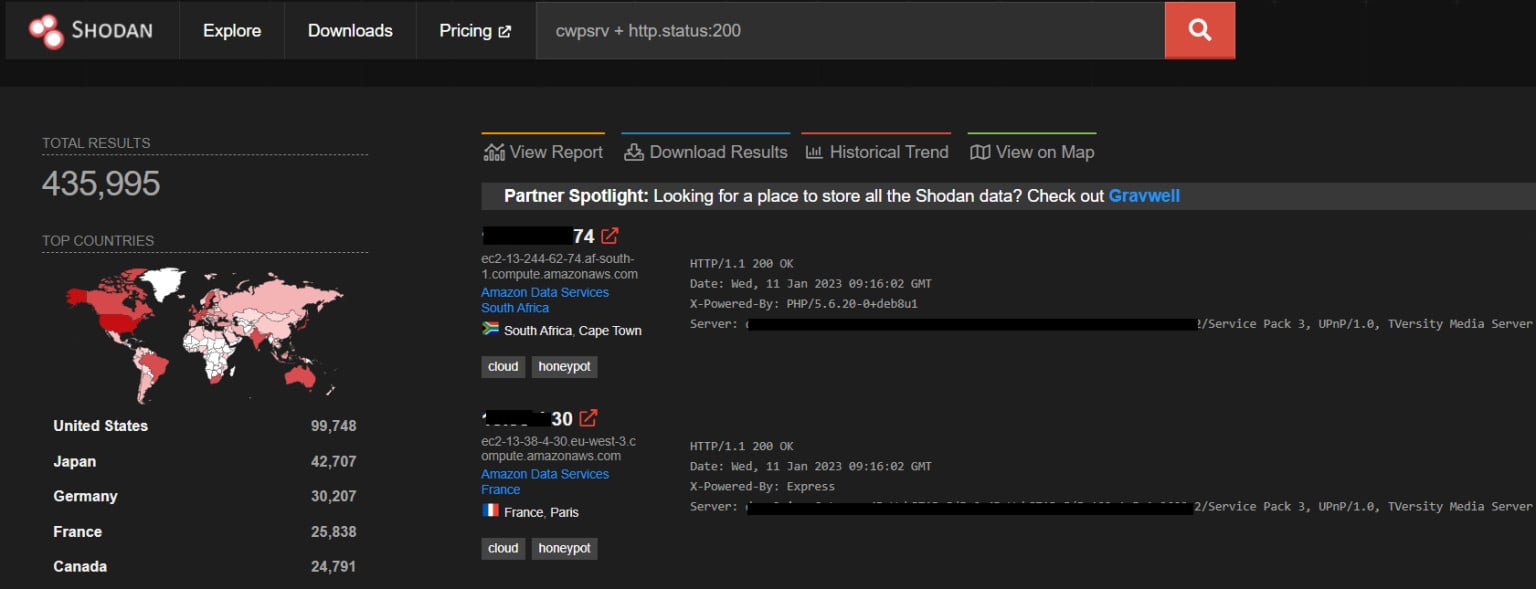

source: CloudSek
Researchers at the Shadowserver Foundation, who observed exploitation of the vulnerability, note that their scans see around 38,000 CWP instances every day.
This figure does not represent vulnerable machines but the population seen by the platform.
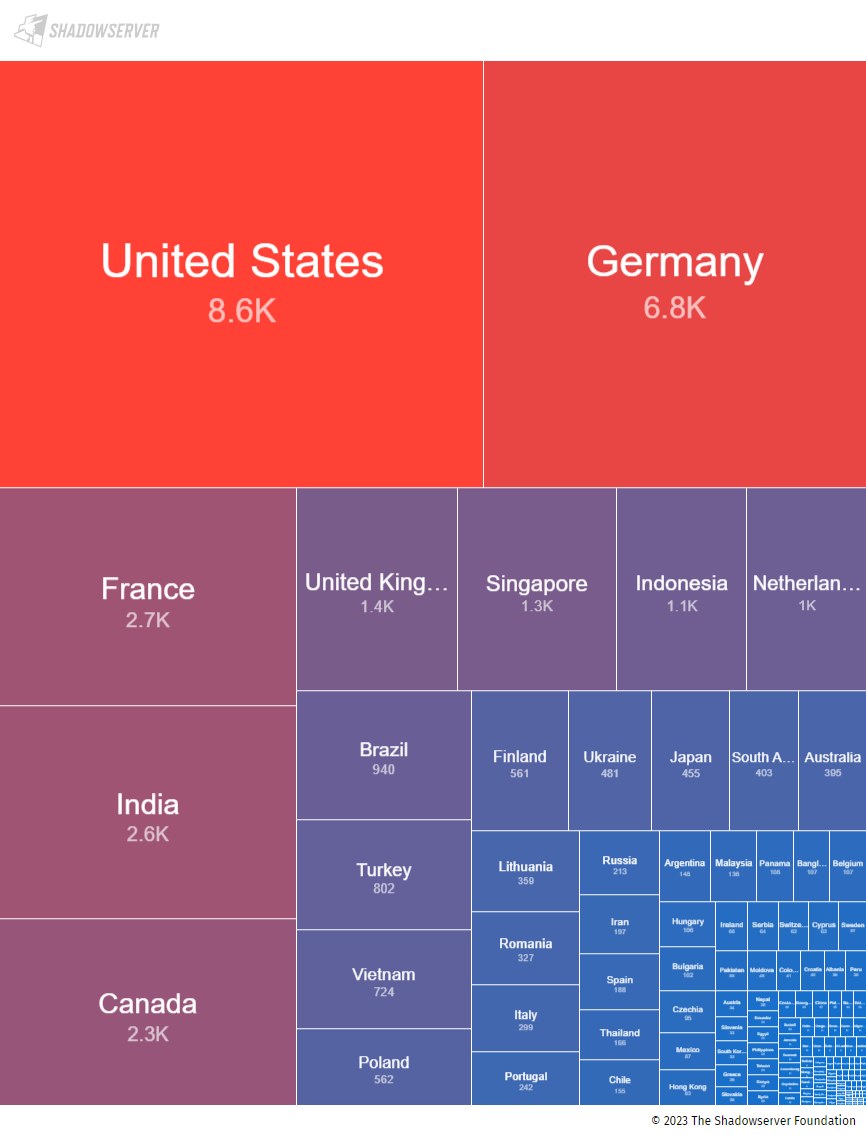

source: The Shadowserver Foundation
Malicious activity recorded by Shadowserver and shared with BleepingComputer revealed that attackers are finding vulnerable hosts and exploiting CVE-2022-44877 to spawn a terminal for interaction with the machine.
In some attacks, the hackers are using the exploit to start a reverse shell. The encoded payloads convert to Python commands that call the attacker’s machine and spawn a terminal on the vulnerable host using the Python pty Module.
Other attacks were just looking to identify vulnerable machines. It is unclear if these scans are conducted by researchers or threat actors looking to find machines to breach at a later date.
It appears that all these exploitation attempts are based on the original public PoC from Numan Türle, slightly modified to suit the attacker’s needs.
Research company GreyNoise also observed several attacks on unpatched CWP hosts from IP addresses in the United States, Thailand, and the Netherlands.
Leveraging CVE-2022-44877 is easy and with exploit code already public, all hackers have to do is find vulnerable targets, a menial task.
Administrators should take immediate action and update CWP to the latest version available, currently 0.9.8.1148 released on December 1, 2022.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below
To keep up to date follow us on the below channels.







