Hackers Target Fcc Crypto Firms In Advanced Okta Phishing Attacks

A new phishing kit named CryptoChameleon is being used to target Federal Communications Commission (FCC) employees, using specially crafted single sign-on (SSO) pages for Okta that appear remarkably similar to the originals.
The same campaign also targets users and employees of cryptocurrency platforms, such as Binance, Coinbase, Kraken, and Gemini, using phishing pages that impersonate Okta, Gmail, iCloud, Outlook, Twitter, Yahoo, and AOL.
Source: Lookout
The attackers orchestrate a complex phishing and social engineering attack consisting of email, SMS, and voice phishing to deceive victims into entering sensitive information on the phishing pages, such as their usernames, passwords, and, in some cases, even photo IDs.
The phishing operation discovered by researchers at Lookout resembles the 2022 Oktapus campaign conducted by the Scattered Spider hacking group, but there is not enough evidence for a confident attribution.
Multi-pronged social engineering attack
The threat actors prepare the attack by first registering domains that closely resemble those of legitimate entities. In the case of the FCC, they created “fcc-okta[.]com,” which is only one different by one character from the FCC’s legitimate Okta single-sign-on page.
The attackers may call, email, or SMS the target, pretending to be customer support, directing them to the phishing site to “recover” their accounts.
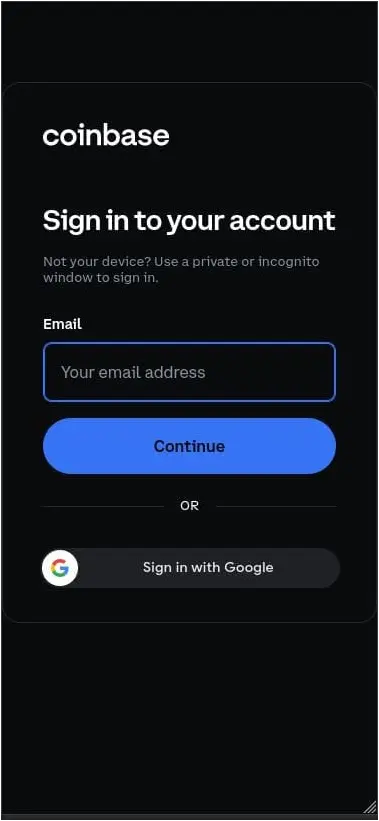
For Coinbase, the texts pretended to be warnings about suspicious login alerts, directing users to phishing pages, as shown below.
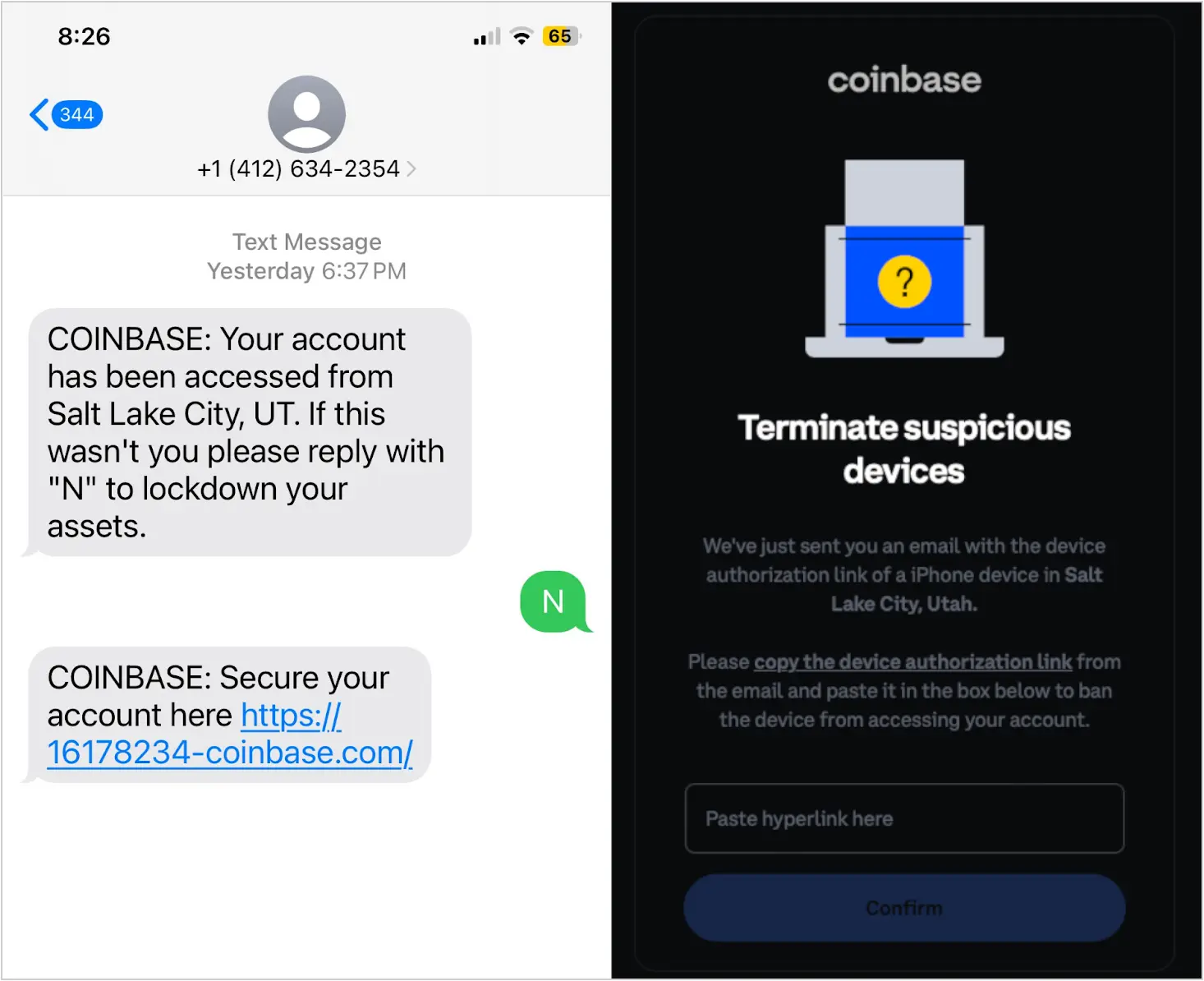
Source: Lookout
Victims reaching the phishing site are prompted to solve a CAPTCHA challenge, which Lookout says serves both for filtering out bots and adding legitimacy to the phishing process.
Those getting through that step are met with a well-designed phishing page that appears as an exact replica of Okta’s genuine login site.
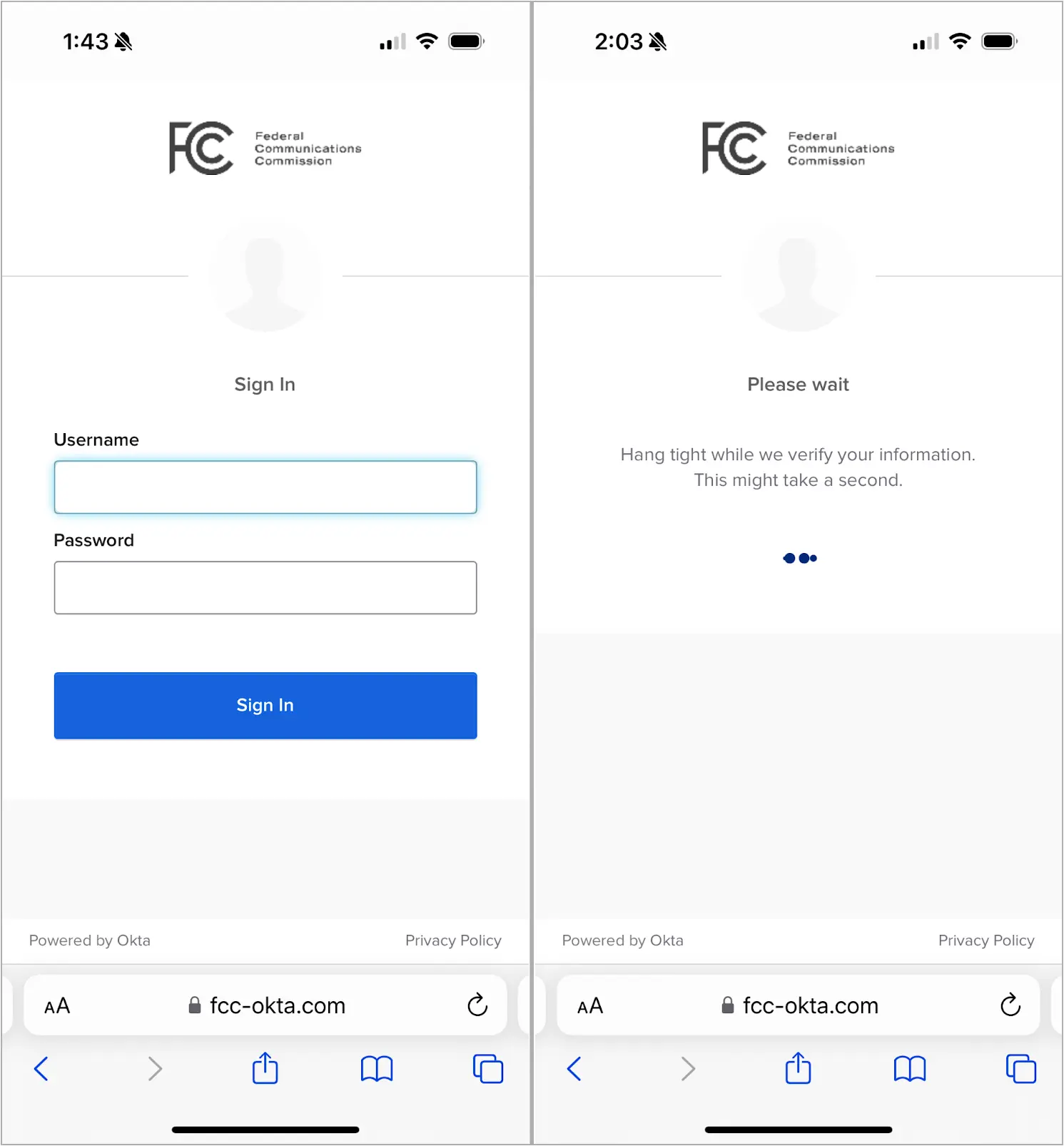
Source: Lookout
The phishing kit deployed by the cybercriminals enables them to interact with the victims in real time to facilitate scenarios like asking for additional authentication in case multi-factor authentication (MFA) codes are required to take over the target’s account.
The central panel controlling the phishing process allows the attackers to customize the phishing page to include the victim’s phone number digits, making the SMS token requests appear legitimate.
After the phishing process is done, the victim may be redirected to the actual platform’s sign-in page or a fake portal that states their account is under review.
Both destinations are used to reduce suspicion on the victim’s side and give the attackers more time to exploit the stolen information.
Digging deeper
Lookout gained insight into the additional targets in the cryptocurrency space by analyzing the phishing kit and finding the relevant lures.
The researchers also gained short-term access to the attacker’s backend logs, confirming that the campaign generated high-value compromises.
“The sites seem to have successfully phished more than 100 victims, based on the logs observed,” explains Lookout.
“Many of the sites are still active and continue to phish for more credentials each hour.”
The threat actors primarily used Hostwinds and Hostinger to host their phishing pages in late 2023 but later switched to the Russia-based RetnNet, which may offer a more extended operational period for shady sites.
Lookout couldn’t determine if the CryptoChameleon phishing kit is used exclusively by a single threat actor or rented to multiple groups.
Regardless of who is behind the kit, its advanced nature, the targeting strategy and communication methods of its operators, and the high quality of the phishing materials underscore the impact this can have on targeted organizations.
A list of indicators of compromise, including command and control servers and phishing sites, can be found at the bottom of Lookout’s article.
