Hackers update Cisco IOS XE backdoor to hide infected devices

10/23/23 update added at the end explaining the cause of decreased detections.
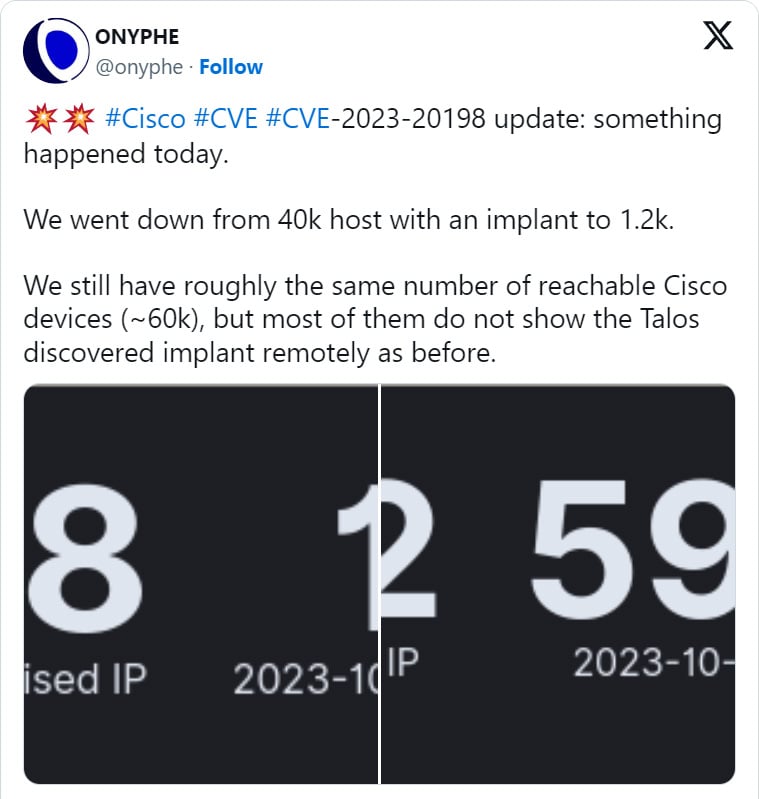
The number of Cisco IOS XE devices detected with a malicious backdoor implant has plummeted from over 50,000 impacted devices to only a few hundred after the attackers updated the backdoor to hide infected systems from scans.
This week, Cisco warned that hackers exploited two zero-day vulnerabilities, CVE-2023-20198 and CVE-2023-20273, to hack over 50,000 Cisco IOS XE devices to create privileged user accounts and install a malicious LUA backdoor implant.
This LUA implant allows the threat actors to remotely execute commands at privilege level 15, the highest privilege level on the device.
However, this implant does not include persistence, meaning a reboot will remove the backdoor. However, any local users created during the attack will remain.
Since the release of this news, cybersecurity firms and researchers have found roughly 60,000 out of the 80,000 publicly exposed Cisco ISO XE devices to be breached with this implant.
Mysterious drop in detected Cisco implants
On Saturday, multiple cybersecurity organizations reported that the number of Cisco IOS XE devices with a malicious implant has mysteriously dropped from approximately 60,000 devices to only 100-1,200, depending on the different scans.
Onyphe Founder & CTO Patrice Auffret told BleepingComputer that he believes the threat actors behind the attacks are deploying an update to hide their presence, thus causing the implants to be no longer seen in scans.
“For the second day in a row, we see the number of implants have drastically dropped in a short time (see screenshots attached). Basically, they appear to have been practically all rebooted (as the known implant doesn’t survive a reboot) or have been updated.”
“We believe it is the action from the original threat actor which is trying to fix an issue that should not have been there from the beginning. The fact that the implant was so easy to detect remotely was a mistake from their side.
“They are probably deploying an update to hide their presence.”
Piotr Kijewski, the CEO of The Shadowserver Foundation, also told BleepingComputer that they have seen a sharp drop in implants since 10/21, with their scans only seeing 107 devices with the malicious implant.
“The implant appears to have been either removed or updated in some way,” Kijewski told BleepingComputer via email.
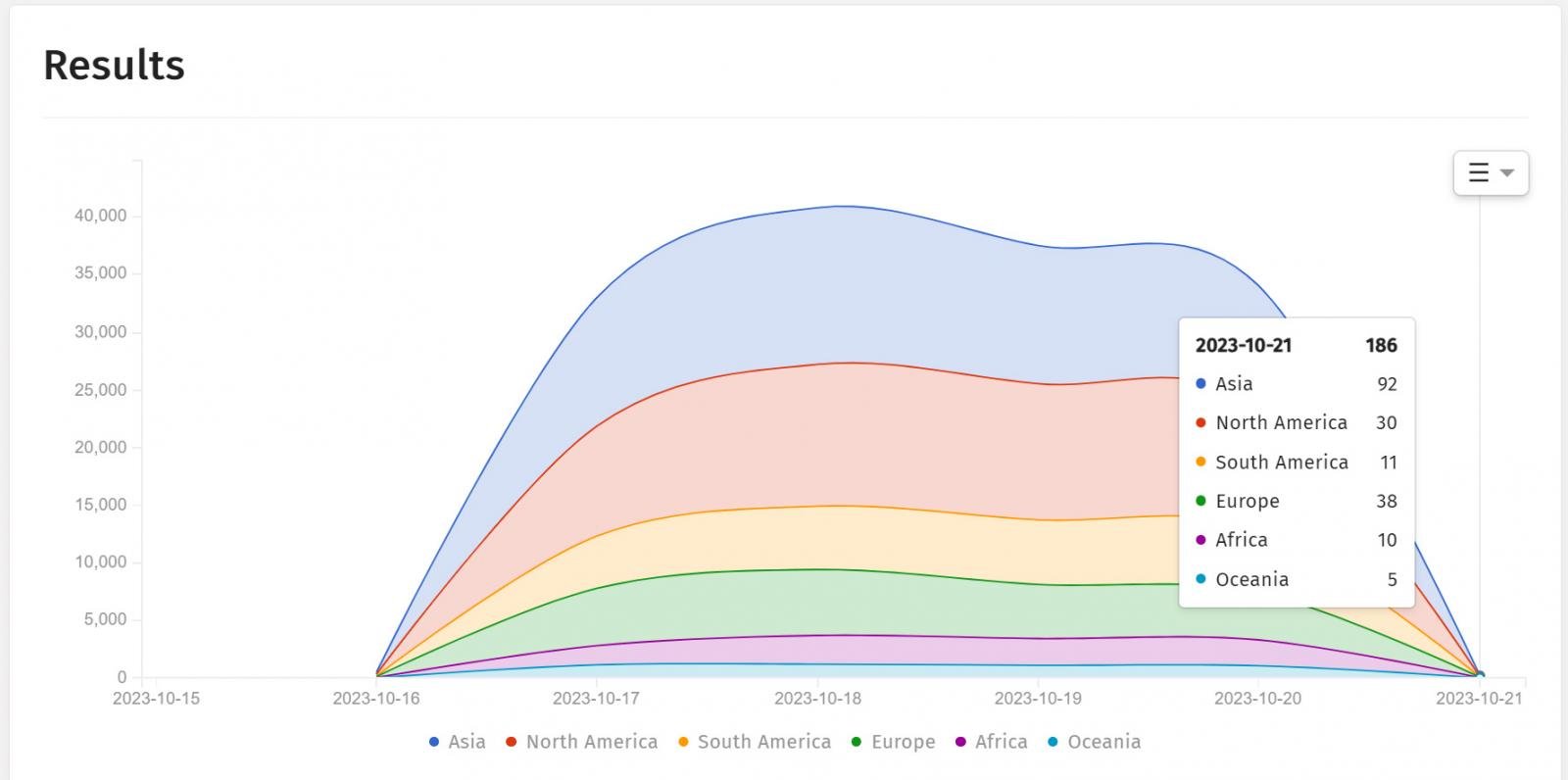

Source: ShadowServer
Another theory shared is that a grey-hat hacker is automating the reboot of impacted Cisco IOS XE devices to clear the implant. A similar campaign was seen in 2018 when a hacker claimed to have patched 100,000 MikroTik routers so they could not be abused for cryptojacking and DDoS campaigns.
However, Orange Cyberdefense CERT for the Orange Group told BleepingComputer that they do not believe that a grey-hat hacker is behind the decrease in implants but rather that this could be a new exploitation phase.
“Please note that a potential trace cleaning step is underway to hide the implant (following exploitation of #CVE-2023-20198),” tweeted Orange Cyberdefense CERT.
“Even if you have disabled your WebUI, we recommend that you carry out an investigation to make sure that no malicious users has been added and that its configuration has not been altered.”
Finally, security researcher Daniel Card theorized that the many devices breached with implants were simply a decoy to hide the real targets in attacks.
Unfortunately, at the time, all we have are theories as to what caused the reduced detections.
Update 10/23/23: Today, cybersecurity firm Fox-IT explained that the cause of the sudden drop of detected implants is due to the threat actors rolling out a new version of the backdoor on Cisco IOS XE devices.
According to Fox-IT the new implant version now checks for an Authorization HTTP header before responding.
“We have observed that the implant placed on tens of thousands of Cisco devices has been altered to check for an Authorization HTTP header value before responding,” reads the LinkedIn post.
As the previous scan methods did not utilize an authorization header, there was no response from the implant, making it appear as if it had been removed.
Cisco Talos confirmed the change in updated advisories [1, 2], sharing a new curl command that can detect the implant on backdoored Cisco ISO XE devices.
This command is the same as the previously shared method but now includes an ‘Authorization’ header to cause the implant to respond to requests:
curl -k -H "Authorization: 0ff4fbf0ecffa77ce8d3852a29263e263838e9bb" -X POST "https[:]//DEVICEIP/webui/logoutconfirm.html?logon_hash=1"The DEVICEIP placeholder should be replaced with the device’s IP address you want to check for the implant.
Once the researchers switched to using the new ‘Authorization’ header, scans showed that there are now 37,890 Cisco ISO XE devices infected with the malicious backdoor implant.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.