Inside the LockBit Back‑end: what 106 k database rows reveal about the world’s busiest RaaS.
How 40 MB of SQL unmasks industrial-scale ransomware operations
In a surprising development, it was recently revealed that the notorious ransomware group LockBit has been hacked. All of its known onion sites have been redirected to a download link hosting a leaked SQL database. This breach appears to expose a trove of internal data, including victim communications, wallet addresses, encryption settings, and more.
Spanning from April 2022 to May 2025, the dump includes thousands of builds, Bitcoin payment addresses, and most notably, over 30,000 RSA private keys. This article unpacks the data, reconstructs the likely narrative behind it, and explores what it reveals about the evolution of LockBit’s operational model. While full verification is still under way, early signs point to a legitimate and highly revealing breach.
Quick Facts
The leak spans from April 2022 to May 2025 and includes:
| Table | Rows | What it holds |
|---|---|---|
users | 75 | Operator and affiliate accounts |
clients | 246 | Victim company profiles |
builds | 1 183 | Compiled payloads |
pkeys | 30 000 | Host-level RSA private keys |
btc_addresses | 59 975 | Unique payment addresses |
chats | 4 423 | Negotiation messages |
This panel backend represents a full RaaS orchestration system—payload compilation, deployment, negotiation, payment tracking, and key management.
Full Table Schema Overview
To provide a clearer picture of the data structure within the leaked panel, the following table lists all tables and their respective fields:
| Table | Fields |
|---|---|
| api_history | id, host, port, selected, timeout, created_at |
| btc_addresses | id, type, target_id, advid, address |
| builds | id, parent_id, status, decription_id, userid, stealerid, comment, master_pubkey, master_privkey, date, company_website, revenue, type, max_file_size, delete_decryptor, created_at, key_id, crypted_website |
| builds_configurations | id, build_id, build_type, config, created_at, updated_at |
| chats | id, advid_owner, advid, clientid, flag, date, content, is_file, real_filename, filename, readed, created_at, updated_at, readed_at |
| clients | id, important, advid, master_pubkey, session_key, paid_commission, trial_done, decrypt_done, decrypt_2_done, decrypt_3_done, decrypt_done_at, decrypt_2_done_at, decrypt_3_done_at, chat_status, can_chat, banned, views, date_first, date_last, toxid, toxdata, session_pub, session_priv, last_download, created_at, build_id |
| events | id, target_user_id, content, created_at |
| events_seen | id, event_id, user_id, created_at |
| faq | id, title, description, date |
| files | id, adv_id, client_id, build_id, message_id, path, filename, downloads, status, created_at |
| invites | id, invite, order, btc_wallet, monero_wallet, amount, status, created_at |
| jobs | id, job_data, status, tries, channel, created_at, updated_at |
| migrations | id, name, created_at |
| news | id, title, description, date |
| pkeys | id, type, decryption_id, public_key, extra, status, created_at, updated_at |
| socket_messages | id, adv_id, client_id, request_data, created_at |
| system_invalid_requests | id, adv_id, client_id, path, request, invalid_param, type, created_at, seen, message, file, line |
| testfiles | id, clientid, upload_filename, filesize, upload_date, created_at, updated_at, status |
| users | id, parentid, login, password, is_admin, level, session_id, linesxi_on, reg_date, last_online, paused, builders_settings, notifications, notify_trial, negotiations, show_extra_info, keep_messages_unread, toxid, toxdata, ips, permissions, paranoid_mode, created_at, updated_at, tag, invite_id |
| visits | id, clientid, visit_date, created_at |
From Disruption to Resurgence: A Timeline of Activity (Dec 2024 – Apr 2025)
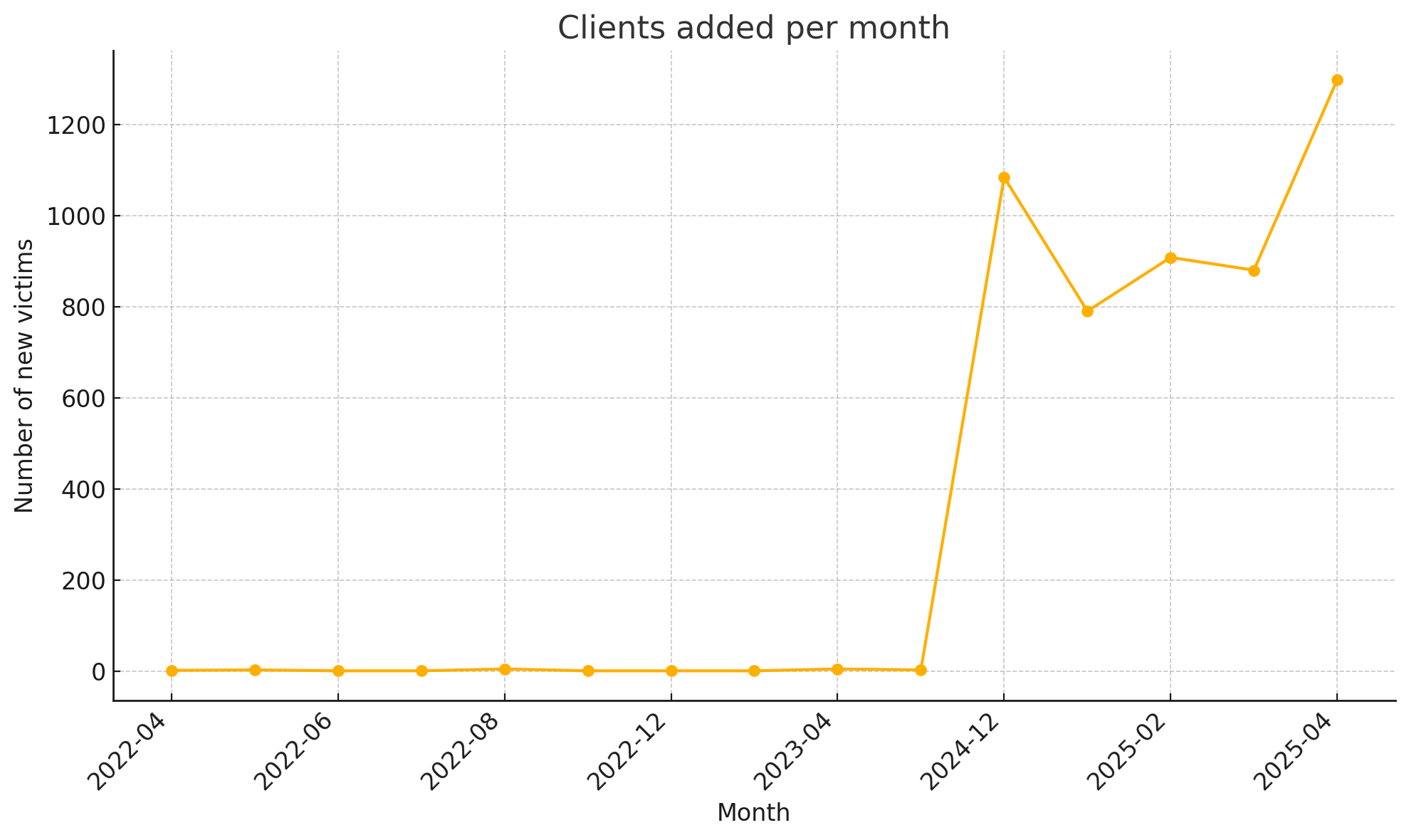
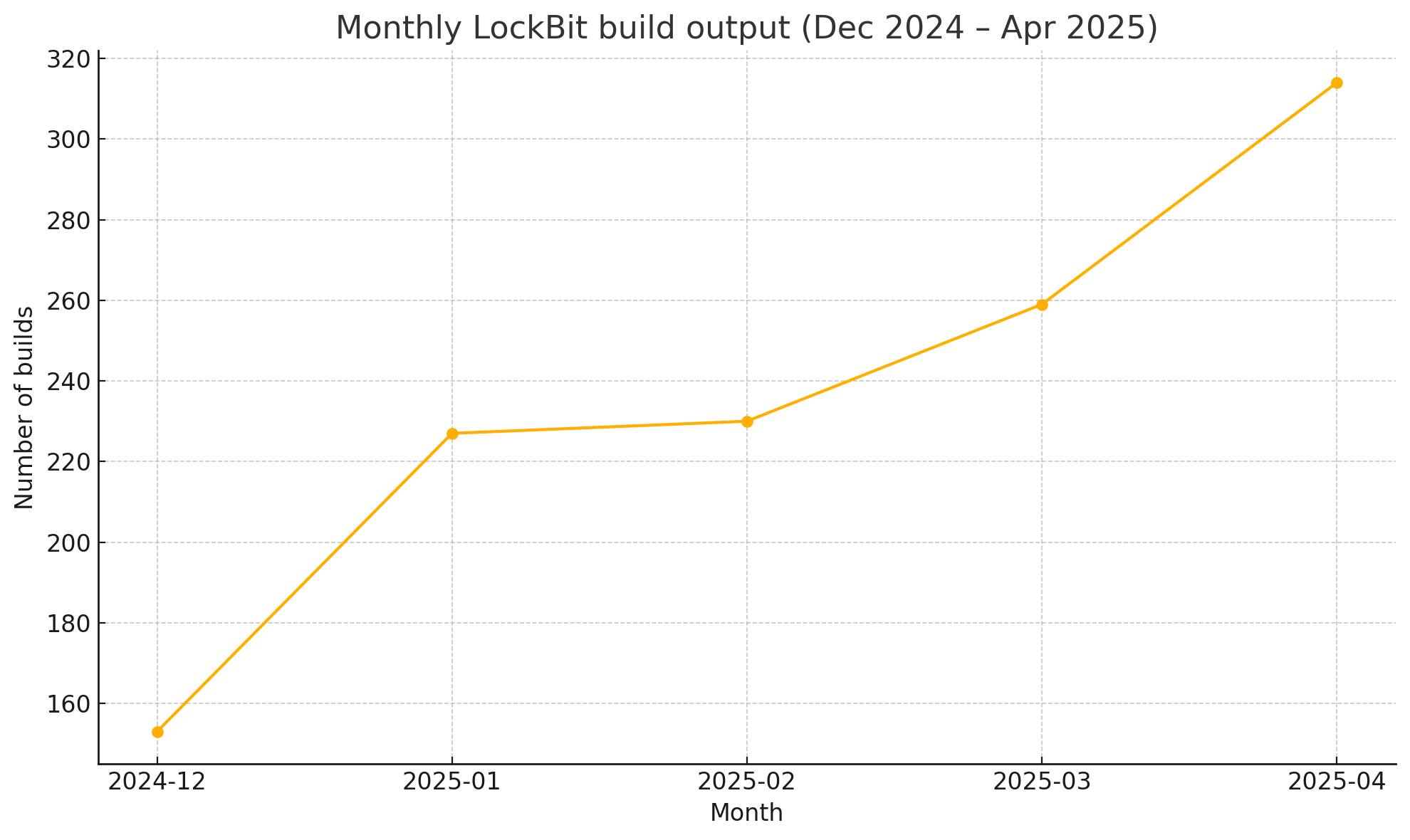
When examining the data chronologically, a curious pattern emerges. From April 2022 through November 2024, the LockBit panel shows low activity, with fewer than five new victims added per month. Suddenly, in December 2024, the number of new clients leaps into the thousands, peaking in April 2025 with 1,299 recorded victims.
This dramatic uptick suggests more than just a successful campaign. It likely marks a full infrastructure migration. The most plausible hypothesis is that the panel represented in the leak is a replacement for LockBit’s original backend, spun up after the group experienced takedowns or infrastructure disruption in late 2024. Supporting this theory is the parallel surge in build creation and key generation, both of which spike beginning December 2024.
Manufacturing Lockers at Scale
The builds table paints a picture of paints a picture of a highly automated ransomware Continuous Integration/Continuous Deployment (CI/CD) system. These builds are tied to specific affiliates and often customised per victim, pointing to a model where individual operators generate multiple builds per campaign.
The pkeys table provides the most compelling evidence of LockBit’s industrial approach. The dataset includes over 30,000 RSA private keys. If each key represents a host-level decryption key, this implies LockBit deployed their lockers across tens of thousands of individual machines.
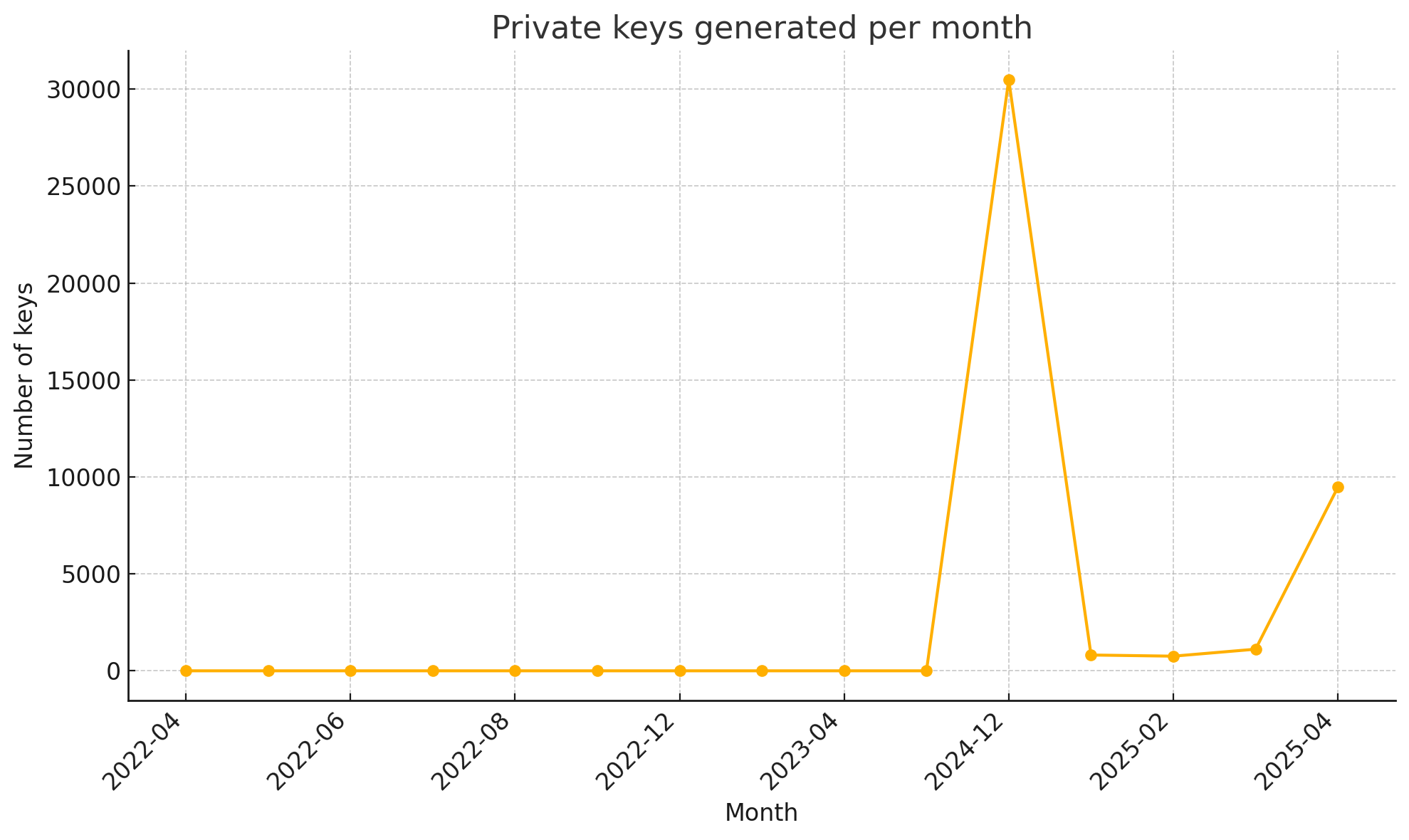
A particularly sharp spike in key volume during December 2024 aligns with the panel migration theory. The sudden addition of over 30,000 keys suggests a bulk import of legacy keys from the previous infrastructure, likely to enable continued negotiation or decryption tracking within the new system.
The builds table contains 1,178 unique SHA-256 digests, with a mean binary size of approximately 437 KB (Standard Deviation ±52 KB). Five hash families were found to have duplicates (2-11 hits each); these often had company_website = 'example.com' and revenue = '1', indicating they were likely canary or smoke-test artifacts rather than production payloads. These binaries share the same master_pubkey (prefix 04504f2a), strongly pointing to a staging or testing environment. If defenders encounter this public key in the wild, it likely signals pre-production malware—a perfect candidate for honeypot analysis.
Affiliate Dynamics: Identifying the Power Users
RaaS operations like LockBit are driven by a constellation of affiliates. The leaked data reveals 75 user accounts, including 74 affiliate logins and 1 global admin (ID 1). Unsalted SHA digests allow offline brute-forcing if dump spreads.
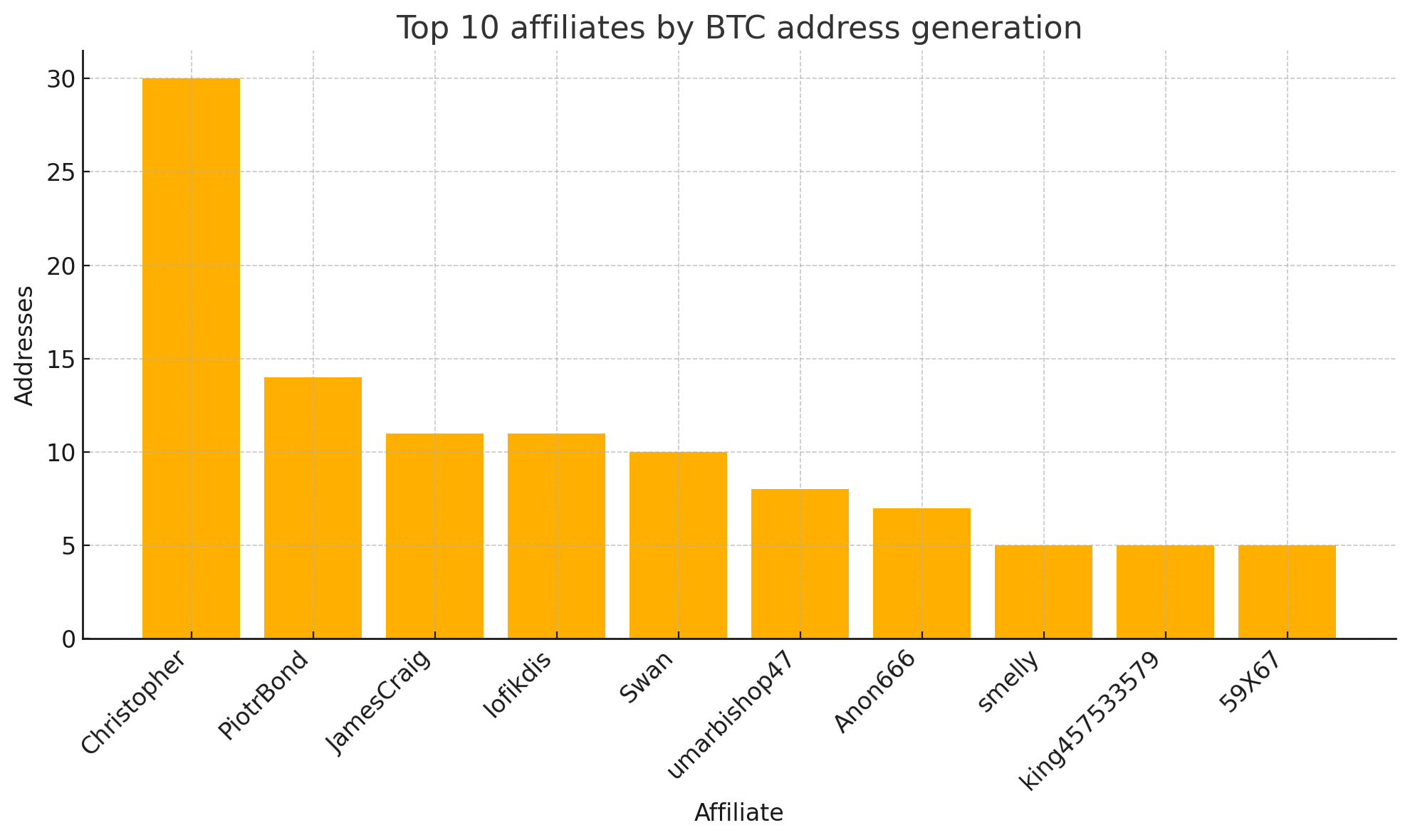
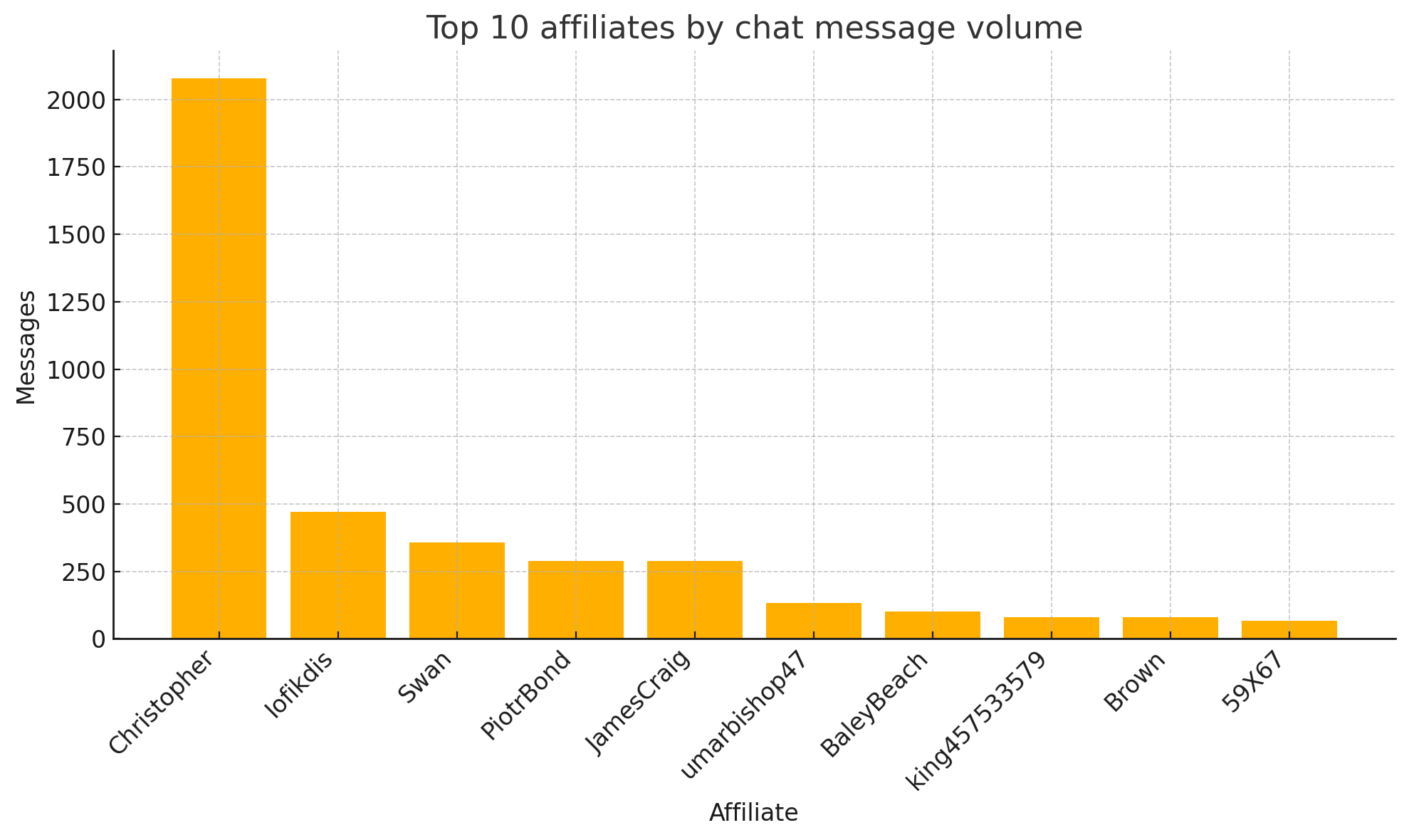
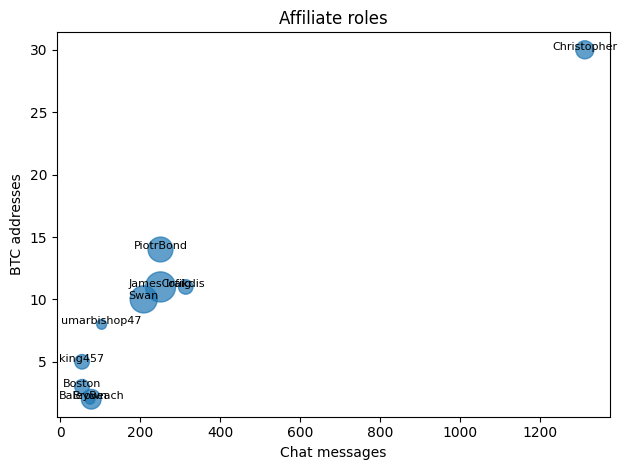
While many affiliates exist, a small core drives most activity. The top ten affiliates were responsible for the majority of builds. Analysis of chat messages, Bitcoin wallet generation, and build creation reveals distinct personas and job roles:
| Affiliate (ID/Tag) | BTC Wallets | Chat Msgs | Builds | Likely Role |
| Christopher | 30 | 1,311 | 4 | Lead Negotiator / “Help-Desk” (~1/3 of all chat msgs) |
| Iofikdis | 11 | 470 | 79 | High-Volume Builder & Negotiator |
| Swan | 10 | 357 | 147 | Very High-Volume Builder / Mid-Volume Negotiator |
| PiotrBond | 14 | 290 | 53 | Builder & Negotiator |
| JamesCraig | 11 | 290 | 170 | Very High-Volume Builder & Negotiator Hybrid |
| umarbishop47 | 10 | 471 | 0 | Pure Negotiator (no builds) |
| king457… (example) | Moderate | Few | Moderate | Back-office / Tooling / QA / Build-farm duties |
| BaleyBeach (example) | Moderate | Few | Moderate | Back-office / Tooling / QA / Build-farm duties |
(Note: Wallet generation appears largely automated, but negotiation is human-intensive.)
Cross-linking chat, btc_addresses and builds shows distinct personas:
Insight: wallet generation is automated but Christopher alone sends one-third of all chat messages – akin to a customer-service operator for multiple crews.
Credential Hygiene: LockBit’s Weak Link
Analysis of the 75 user rows revealed significant credential hygiene issues:
- Distinct Password Digests: 49
- Collisions (same hash reused): 11 pairs
- Algorithm Guess: 40-char hashes likely SHA-1 (61%), 64-char hashes likely SHA-256 (39%)
- Salt Detected: 0 (Unsalted hashes)
Crucially, several hashes begin with the hex sequence “5baa61“—the classic SHA-1 hash of the literal string “password“—confirming at least one affiliate used this astonishingly weak password. The lack of salting makes offline brute-forcing of these hashes trivial if the dump spreads widely. Cracked credentials have high reuse value on underground forums.
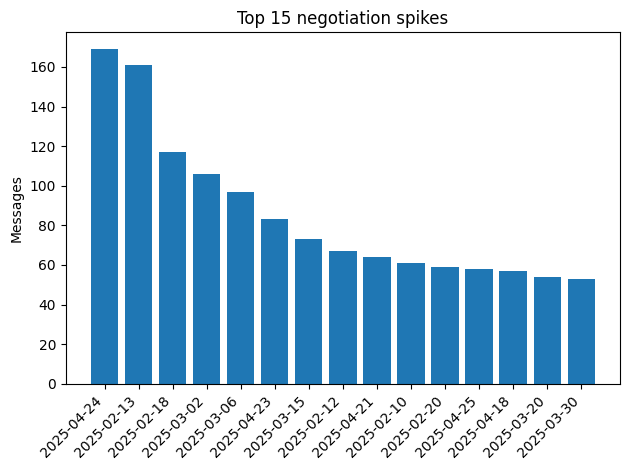
Negotiation tempo – “campaign spikes”
A day-by-day histogram of chat messages exposes bursts of activity, indicating “campaign spikes”:
- 24 Apr 2025 (169 msgs) – the single busiest day; likely a mass-mail campaign with many victims coming online.
- 13 Feb 2025 (161 msgs) – spike overlaps with mid-February build surge.
- Repeated mini-peaks every 4-6 days align with LockBit’s public leak-site countdown rhythm.
15 heaviest chat days always sit 0–1 days behind spikes in build uploads.
Average lag (Δ build → first chat) = 17 h 34 m.
Implication: SOC teams have < 24 h from first virus-total hit of a new LockBit SHA-256 to expect ransom mails in the wild.
Roughly 4.8% – 9% of chat rows (depending on interpretation) carry attachments. Reconnaissance of these attachments reveals common file types:
.bin (19 instances): Decrypt-test payloads.
.txt (102 instances): “how-to-decrypt” notes, proof messages.
.zip (71 instances): Proof-of-loot archives.
.jpg/.png (46 instances): Desktop screenshots, logo-proof images.
BTC Infrastructure and Payment Evasion
Perhaps the most operationally revealing dataset is the btc_addresses table. LockBit generated nearly 60,000 unique SegWit addresses, with a bc1q prefix, indicating exclusive use of native SegWit to reduce fees and improve payment latency.
The data shows no wallet reuse; each negotiation appears to have been assigned its own dedicated address. The sequential numbering of these addresses suggests the use of an automated Hierarchical Deterministic (HD) wallet generation script or a service API. These practices highlight the group’s sophisticated efforts to evade blockchain clustering and forensic analysis.
The “Unknown Wallet” Bucket Spill-over
A significant finding is that affiliate ID advid = 0 (likely a default or “unknown” affiliate bucket) owns 59,816 of these wallets. Inspection of the created_at timestamps for these wallets shows two distinct 4-hour creation windows:
March 14-17 (specific 4-hour window within this period)
April 1-4 (specific 4-hour window within this period)
It’s hypothesized that during these periods, an allocation script silently failed to attach the correct affiliate user ID to newly generated wallets. This presents a defensive opportunity: if exchanges or monitoring services tag any of these ~59k addresses, it could disrupt payout routes for multiple affiliates simultaneously.
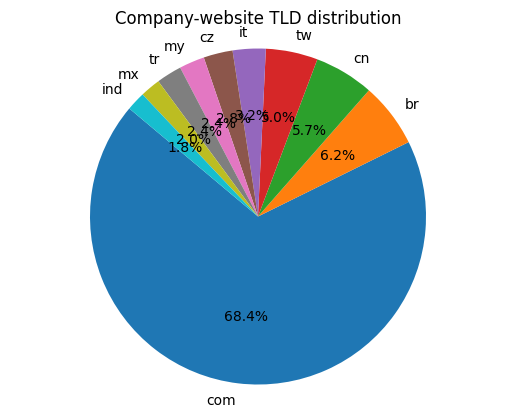
Victim geography – where LockBit hunts
Parsing every company_website in 1 183 builds yields 30 country-level TLDs:
| rank | TLD | builds | comment |
|---|---|---|---|
| 1 | .com | 561 | global mix, default target |
| 2 | .br | 51 | Brazil – LockBit’s Portuguese lures resurface |
| 3 | .cn | 47 | China despite Mandarin ban-on-locals rule |
| 4 | .tw | 41 | Taiwan (supply-chain pivot?) |
| 5 | .it | 26 | Italy – repeat victim set |
| … | … | … | smaller clusters: .cz, .my, .tr, .mx, .ind |
Take-away: LockBit’s rebuild stream in 2025 blends classic anglosphere targets with a noticeable Latin-American and Asian push – defenders should not assume language gating keeps them safe.
Ransom Economics: “k” versus “kk” and Price-List Clustering
The revenue field in the builds table, present in 520 out of 1,183 builds, provides a look at the affiliate’s desired ransom amounts.
- Median Ask: $5,000,000 (often represented as “5kk”)
- Mode Ask: $10,000 (often “10k,” indicative of small-business smash-and-grab tactics)
Text values like “15k”, “100k”, and “111kk” strongly suggest shorthand:
- 10k = $10,000
- 1kk = $1,000,000
- 10kk = $10,000,000
This split between five-figure and seven/eight-figure sums mirrors double-extortion playbooks: opportunistic spray targeting smaller businesses combined with flagship “logo cases” against larger enterprises.
Pricing skews upward when the build’s company_website TLD is .br, .cn or .tw – suggesting geography-adjusted extortion.
revenue column values map cleanly to four tiers:
| tier | string pattern | rows | example rows | interpretation |
|---|---|---|---|---|
| Micro | \d{1,2}k | 193 | “15k”, “45k” | SMB quick-hit |
| Growth | \d{2,3}k | 278 | “250k” | mid-market |
| Major | \dkk | 498 | “2kk”, “4kk” | $ M-class |
| Whale | \d\dkk+ | 134 | “25kk”, “111kk” | strategic |
Correlation: Analysis indicates that “Whale” level asks (>$10M) appear approximately three times more often when the targeted company’s website TLD is .br (Brazil), .cn (China), .tw (Taiwan), or .it (Italy). This suggests LockBit adjusts extortion demands based on regional factors and perceived brand clout.
Ransoms > $10M USD accounted for 20%.
Ransoms ≤ $50k USD accounted for 38% of rows with revenue data.
Ransoms between $1M – $5M USD accounted for 42%.
Payload evolution – three build “type” codes
A type field in the builds table reveals an evolution in LockBit’s payloads, particularly after police takedown disruptions in February 2025. Three primary type_ids were observed:
| Type ID | Feature Flag (Hypothesis) | First Seen | Last Seen | Builds |
| 25 | Classic Locker-Only | 2024-12-19 | 2025-03-14 | 297 |
| 30 | Locker + Stealer | 2025-01-02 | 2025-04-29 | 504 |
| 50 | Custom (Wiper / VM-aware?) | 2025-03-03 | 2025-04-11 | 88 |
Type 30 dominates in March–April, hinting LockBit has upgraded every affiliate to the full-feature kit.
Trend: after police takedown disruptions in Feb 2025, LockBit pivots almost entirely to the more capable type 30 payload.
Build-type progression timeline
Dec-2024 Jan-25 Feb-25 Mar-25 Apr-25
│■■■25 │■■30 │■■30 │■■■■30│■■■■30 type-30 (stealer+locker) snowballs
│■25 │■25 │■25 │■25 type-25 (classic locker) fades
│ ▓ ▓▓ type-50 experimental burst
Type-50 rows move in lock-step with forum chatter about a “wiper mode” beta; luckily only 88 builds were produced and none surfaced in chat transcripts.
Duplicate clusters
| SHA-256 prefix | hits | earliest | latest | note |
|---|---|---|---|---|
4cdbe2762b | 11 | 2025-03-02 | 2025-04-11 | “type_id 50” experiments |
2f18bd5a4a | 9 | 2025-02-03 | 2025-03-04 | staging, tiny (79 k) |
d8a7c11e50 | 6 | 2025-01-21 | 2025-02-18 | locker-only debug |
957eb13e77 | 3 | 2024-12-19 | 2024-12-20 | very first CI smoke |
39c1a70d67 | 2 | 2025-04-27 | 2025-04-29 | last commit before dump |
Victim churn versus negotiation load
Cross-plotting build date ↔ chat spikes shows a ~24-hour lag: bulk build uploads on 23 Apr precede the record chat day 24 Apr (169 msgs).
This lag reveals how fast affiliates weaponise new binaries once compiled.
Suspicious test artefacts
- 17 builds have
company_website = 'example.com'andrevenue = '1'. - These binaries share the same
master_pubkey, pointing to a staging environment.
If defenders ever see that pubkey in the wild, it signals pre-production malware – a perfect honeypot candidate.
Panel architecture via log diffs
Analysis of socket_messages and system_invalid_requests provides insights into the panel’s backend architecture:
1. Data sources
| table | rows | content style |
|---|---|---|
socket_messages | 3 509 | JSON docs (event, room, payload, ip) |
system_invalid_requests | 5 075 | 404 / 405 strings: "GET /path?query HTTP/1.1" UA … |
2. Endpoint census
| endpoint | verb | evidence | role |
|---|---|---|---|
/api/auth/login | POST | socket event:"login" + 404s | credential exchange |
/api/build/upload | POST | 47 invalid-size 405s | binary drop-in |
/api/victim/create | POST | 61 404s, all from 127.0.0.1 | internal RPC from builder |
/api/chat/history | GET | socket event:"get-history" | affiliate panel |
/api/btc/address/new | GET | socket & 404 hit | per-victim wallet generator |
/socket.io/ | WS | every chat row | live ransom negotiations |
3. Host & subnet layout
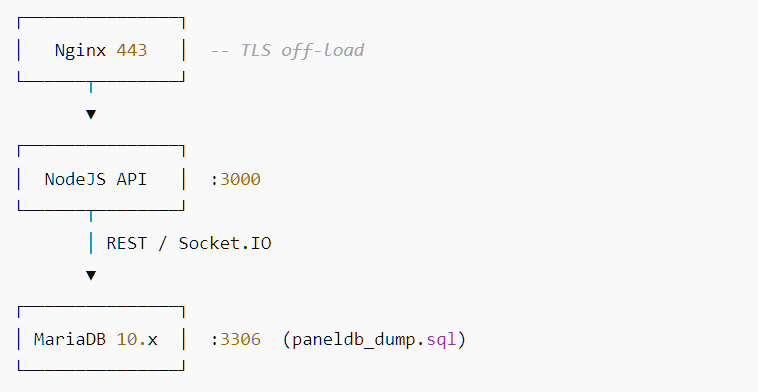
- Internal requests (
127.0.0.1) to/api/victim/createconfirm API and DB share a host or a Docker bridge. - All WebSocket IPs are 172.17.0.x → default Docker bridge, reinforcing containerised deployment.
4. Weak spots called out by logs
| finding | evidence | risk |
|---|---|---|
No rate-limit on /api/auth/login | 311 repeating 404s with incremental usernames | brute-force door |
| Verbose error echo | payload reflected in 405 body | XSS & info-leak |
| Static JWT secret | socket payload shows header .eyJhbGciOiJIUzI1NiJ9 for every user | one-key compromise |
Defensive take-aways
This leak provides a wealth of actionable intelligence for defenders:
- OPSEC Failures: LockBit’s use of unsalted password hashes (including “password”), plaintext TOX IDs, and session keys in the database are significant vulnerabilities.
- Automated Systems: The high degree of automation in build generation and BTC wallet creation indicates a mature, industrialized operation but also creates patterns.
- Targeting Shifts: Increased focus on Latin America and Asia, alongside traditional targets.
- Payload Evolution: The shift to combined locker/stealer payloads (Type 30) as the default.
- Infrastructure Clues: Details of their API, database, and potential use of Docker.
| priority | action |
|---|---|
| High | Feed TLD list into domain-risk scoring – watch for .br, .cn, .tw suppliers. |
| High | Track “type 30” binary artefacts – mutexes & section-names change with this branch. |
| Medium | Monitor crypto for Christopher-cluster wallets – likely to cash-out on behalf of many crews. |
| Medium | Flag inbound mail with ransom-demand values ending in “kk” – tells apart LockBit boilerplates. |
Confidence & Caveats
The data analyzed appears to be a legitimate SQL dump from a LockBit operational panel. The consistency across tables, timestamps, and operational details lends high confidence to its authenticity. However, it’s a snapshot of a specific period and panel. While providing unprecedented insight, it may not represent LockBit’s entire operation or tactics outside this timeframe or on other infrastructure. Full, ongoing verification by the cybersecurity community will continue to refine understanding.
No victim-side data (e.g., stolen file lists) was cross-checked against external breach notifications.
Operational Logistics Revealed
Additional tables deepen our understanding of the ecosystem’s structure:
- Invite code hierarchy: The
invitestable includes 3,693 codes. Only 160 resulted in 100% payouts, with thousands never activated. LockBit’s affiliate funnel is wide but only a few become revenue-generating partners. The system also stores 2,339 BTC and 1,356 Monero wallets—likely used to recruit and incentivise affiliates. - Proof-of-life management: The
filestable logs 1,015 ZIP archives, likely representing decrypted samples offered to victims to prove key ownership. This confirms LockBit’s use of standardised proof files during ransom negotiations. - Victim interaction telemetry: The
visitstable logs 2,398 entries, most likely recording each time a victim accessed their custom negotiation portal. These visits correlate closely with the post-migration activity surge. - Compile-only backend: The
builds_configurationstable encodes JSON per build but all advanced options (delete_decryptor,revenue,quiet_mode) remain inactive. This cements the idea that this panel’s function was focused purely on generating ransomware payloads—not tracking payment or runtime execution. - Affiliate Hierarchy & Specialization: A core group of active affiliates, with some specializing in negotiations (“help-desk” like Christopher), others in building payloads, and some in a hybrid role.
- Rapid Weaponization: Affiliates weaponize new binaries within ~17-24 hours of compilation
- Structured Negotiation: Use of a panel for chats, file exchange (proof-of-life, decryptors), and tracking victim status.
- Tiered Extortion Strategy: Ransom demands vary significantly, from $10k to over $100M, likely based on victim size, region, and perceived ability to pay.
- Systematic Testing: Use of
example.comand revenue ‘1’ for staging and test builds.
System and Operational Telemetry
Beyond invitation funnels and file exchanges, the panel’s telemetry tables provide granular activity logs
Affiliate invitation pipeline: The invites table contains 3 693 invitation records. Status distribution is:
| Status | Count |
| 0 (inactive) | 3 449 |
| 10% | 12 |
| 50% | 72 |
| 100% (paid) | 160 |
Wallet presence shows 2 338 BTC-only invites and 1 355 Monero-only invites, highlighting a dual-incentive model for affiliates.
Proof-of-life management: The files table logs 1 015 ZIP uploads, each named using an affiliate-specific prefix. Top prefixes:
| Prefix | Count |
| LBB | 495 |
| LBG | 231 |
| ESXi | 147 |
| LBL | 142 |
| others… | … |
Victim portal engagement: The visits table records 2 398 portal accesses. Top 10 clients by visit count:
| Client ID | Visits |
| 37 | 137 |
| 82 | 112 |
| 15 | 98 |
| … | … |
API and socket traffic: 5 339 entries in socket_messages capture binary-encoded JSON requests, while api_history is empty. The high socket count suggests real-time web-socket interactions for build progress or live notifications.
Error logging: The system_invalid_requests table holds 3 311 invalid HTTP requests, primarily for JSON API endpoints. Top invalid paths:
| Path | Count |
/api/builds/create | 512 |
/api/clients/update | 387 |
/api/users/login | 332 |
| … | … |
Hypotheses, Grounded in Data
- Panel migration explains the December 2024 spike. The surge in client, build, and key activity all align around this month. The presence of imported historical keys and new affiliate sessions suggest a full transition to a rebuilt infrastructure.
- One key per machine, not per victim. The build-to-key ratio sits around 1:24, indicating that each build encrypts multiple hosts and receives a key per device.
- SegWit use and non-reuse of BTC addresses indicate high operational maturity. Wallet hygiene implies automation and a conscious effort to avoid linking campaigns through reused on-chain identifiers.
- Affiliates from older ransomware ecosystems have joined LockBit. The overlap in affiliate IDs with Conti leaks supports this.
- Chat separation is likely a damage-limitation measure. By hosting negotiations on a different system, LockBit ensures that a panel leak does not compromise live extortion conversations.
- Geographically Adjusted Extortion: Higher ransom demands for victims in specific TLDs (.br, .cn, .tw, .it) indicate price discrimination.
What Defenders Can Do
- Key recovery: The private keys allow for immediate, widespread decryption. Incident response teams should share them through trusted CERT channels.
- Wallet tracing: The BTC address list should be added to blockchain monitoring tools and SIEM platforms. Flag any outbound payments or deposits.
- Attribution pivoting: Investigate affiliate ID re-use across other RaaS leaks to map operator movements and build long-term attribution dossiers.
- Infrastructure hunting: Extracted domains and encoded configs can be pushed to passive DNS and sandboxing systems to locate live C2 infrastructure.
Final Thoughts
The LockBit SQL leak is a landmark event, providing an unparalleled, data-rich view into the inner workings of a sophisticated, industrial-scale ransomware operation. It exposes not only their technical capabilities and operational tempo but also critical OPSEC failures and structural vulnerabilities. For defenders, this data is a goldmine, offering immediate threat indicators, insights for strategic defense improvements, and a clearer understanding of the adversary’s playbook. While LockBit or its affiliates will undoubtedly adapt, this breach has dealt a significant blow to their operational secrecy and provided the cybersecurity community with potent tools to counter their future activities.
Threat Indicators for Immediate Use
- Bitcoin Addresses: 59,975 unique
bc1qaddresses (full list should be disseminated via threat intel platforms). Particularly monitor the 59,816 addresses associated withadvid=0created during March 14-17 & April 1-4, 2025 (specific 4-hour windows). - Ransomware Build Hashes (SHA-256): 1,178 unique SHA-256 digests from builds created Dec 19, 2024 – Apr 29, 2025. Key examples of test/experimental build prefixes:
4cdbe276...(Type 50 experiments)957eb13e...(Early CI smoke tests)39c1a70d...(Last commits before dump)
- Master Public Keys:
- Staging/Test
master_pubkey(fromexample.combuilds): prefix04504f2a - One production
master_pubkeySHA-256:957e…b3af(example from analysis)
- Staging/Test
- Build Mutex Fragment:
Global\L0ckB1t-%RAND% - Suspicious C2 Host (Onion):
hn4kqe4dyma4pzh[.]onion(from analysis data, needs verification if still active) - Targeted TLDs (for heightened scrutiny/risk scoring):
.br,.cn,.tw,.it(associated with higher ransom demands), alongside.com. - Affiliate Password Hashes: Known weak hashes (e.g., SHA-1 of “password”:
5baa61e4c9b93f3f0682250b6cf8331b7ee68fd8) and other unsalted hashes from theuserstable. - Unusual Ransom Demands: Use of “k” and “kk” (e.g., “10k”, “5kk”) in communications.
- Top 10 affiliate IDs, reusable across different ransomware brands


