Mac users, update now! “Powerdir” flaw could allow attackers to spy on you
If you have been forgoing updating your Mac, this article might make you think twice.
The Microsoft 365 Defender Research Team has discovered a vulnerability in macOS, which allows malicious apps to successfully bypass a user’s privacy preferences. This means attackers could access personal data that was once private, as well as install a malicious app—or hijack one that’s already installed—to access the microphone to record conversations or capture screenshots of the user’s screen without them knowing.
Dubbed “Powerdir,” it is the latest in a lengthening line of Transparency, Consent, and Control (TCC) security framework bypasses that have been hitting Apple these past few months. The Microsoft team is said to have reported Powerdir to Apple in mid-July 2021, and Apple patched it 6 months after. It is tracked as CVE-2021-30970.

The TCC is essentially the technology that keeps user data within a device private, so apps without full disk access rights cannot just access data without the user’s consent. It also houses a database of consent history for app requests.
While Apple has set up restrictions and blocking mechanisms against unauthorized code execution, the Microsoft team was able to successfully change a user’s home directory and plant a second TCC database (a specially crafted one, of course). In doing so, they were able to access protected user information.
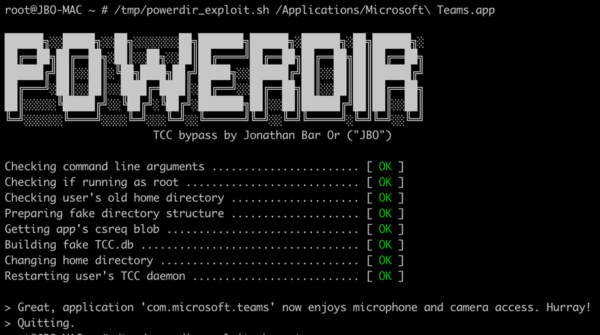

A bypass similar to Powerdir was presented by Wojciech Reguła and Csaba Fitzl in Black Hat USA on August 2021, along with over 20 more TCC bypasses. This flaw was tracked as CVE-2020-27937. However, despite Apple patching this, the Microsoft team’s PoC still worked until Apple released macOS Monterey in October 2021.
The Microsoft team then modified their first Powerdir PoC to make it work in the new macOS. Here’s a link to the demo video of how it now works in Monterey. This, too, has been patched by Apple and included as part of CVE-2021-30970.
How to protect yourself from Powerdir
All Mac users have to do is download and apply the fixes. Easy!
Stay safe!
The post Mac users, update now! “Powerdir” flaw could allow attackers to spy on you appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


