Meet LostTrust ransomware — A likely rebrand of the MetaEncryptor gang

The LostTrust ransomware operation is believed to be a rebrand of MetaEncryptor, utilizing almost identical data leak sites and encryptors.
LostTrust began attacking organizations in March 2023 but did not become widely known until September, when they began utilizing a data leak site.
Currently, the data leak site lists 53 victims worldwide, with some having their data leaked already for not paying a ransom.
It is unclear if the ransomware gang only targets Windows devices or if they utilize a Linux encryptor as well.
A rebrand of MetaEncryptor
MetaEncryptor is a ransomware operation that is believed to have launched in August 2022, amassing twelve victims on their data leak site through July 2023, after which no new victims were added to the site.
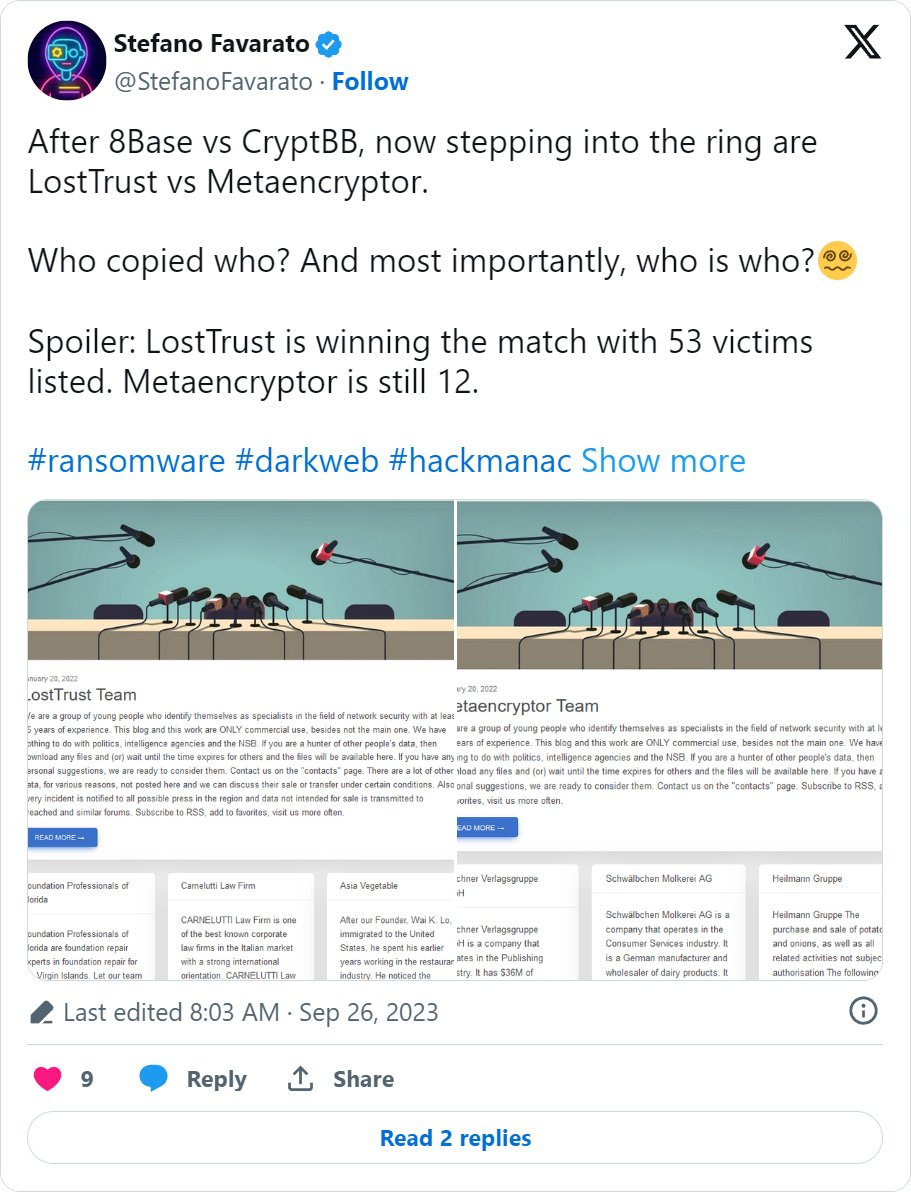
This month, a new data leak site for the ‘LostTrust’ gang was launched, with cybersecurity researcher Stefano Favarato quickly noticing it utilizes the same exact template and bio as MetaEncryptor’s data leak site.
“We are a group of young people who identify themselves as specialists in the field of network security with at least 15 years of experience,” reads a description on both the MetaEncryptor and LostTrust data leak sites.
“This blog and this work are ONLY commercial use, besides not the main one. We have nothing to do with politics, intelligence agencies and the NSB.”
BleepingComputer also found that both the LostTrust [VirusTotal] and MetaEncryptor [VirusTotal] encryptors are virtually identical, with some minor changes to ransom notes, embedded public keys, ransom note names, and encrypted file extensions.
Furthermore, cybersecurity researcher MalwareHunterTeam told BleepingComputer that LostTrust and MetaEncryptor are based on the SFile2 ransomware encryptor. This relation is further backed up by an Intezer scan showing a lot of code overlap between the LostTrust and SFile encryptors.
Due to the significant overlap between the two operations, it is believed that LostTrust is a rebrand of the MetaEncryptor operation.
The LostTrust encryptor
BleepingComputer found a sample of the LostTrust encryptor and performed a brief analysis below.
The encryptor can be launched with two optional command line arguments, –onlypath (encrypt a specific path) and –enable-shares (encrypt network shares).
When launched, the encryptor will open a console displaying the current state of the encryption process, as shown below.
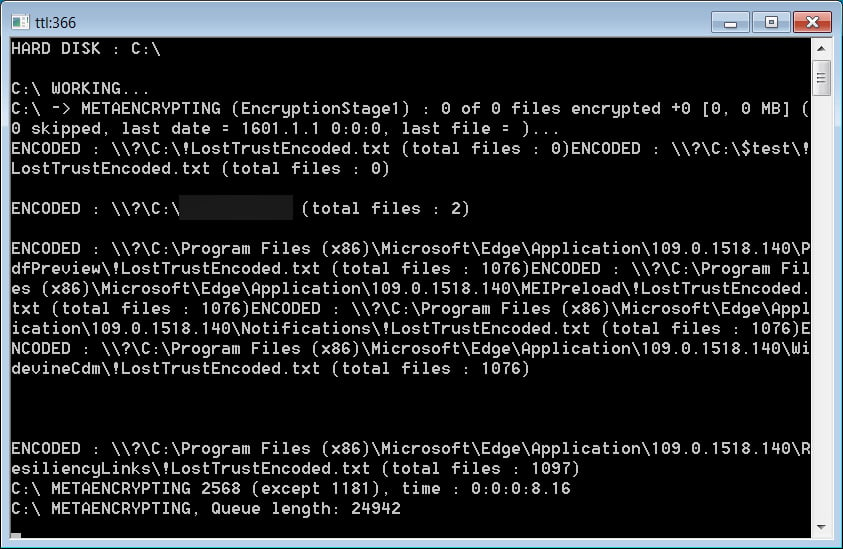

Source:BleepingComputer
Note the ‘METAENCRYPTING‘ string in the encryptor, indicating it is a modified MetaEncryptor encryptor.
When executed, LostTrust will disable and stop numerous Windows services to ensure all files can be encrypted, including any services containing the Firebird, MSSQL, SQL, Exchange, wsbex, postgresql, BACKP, tomcat, SBS, and SharePoint strings.
The encryptor will also disable and stop additional services associated with Microsoft Exchange.
When encrypting files, the encryptor will append the .losttrustencoded extension to encrypted file’s names, as illustrated below.
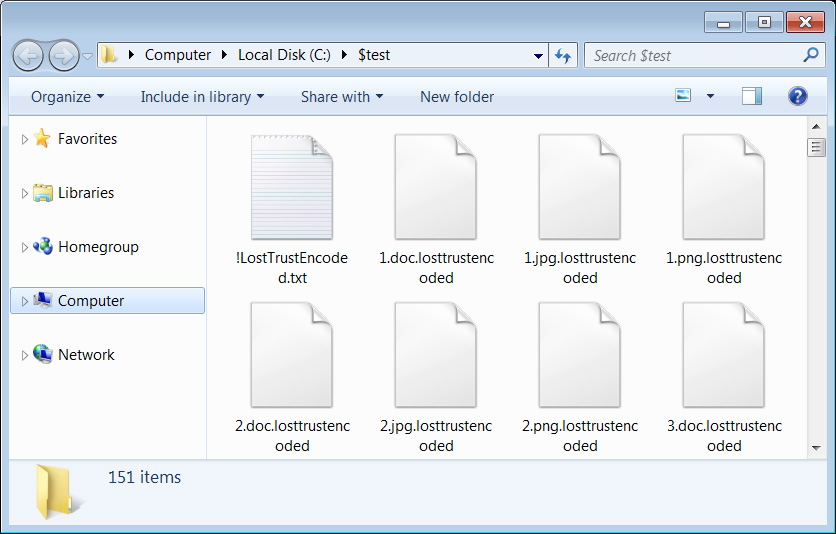
Source: BleepingComputer
Ransom notes named !LostTrustEncoded.txt will be created in every folder on the device, with the threat actors introducing themselves as prior white hat hackers. However, after being poorly paid, they decided to switch to cybercrime.
“Our team has an extensive background in legal and so called white hat hacking. However, clients usually considered the found vulnerabilities to be minor and poorly paid for our services,” reads the LostTrust ransom note.
“So we decided to change our business model. Now you understand how important it is to allocate a good budget for IT security.”
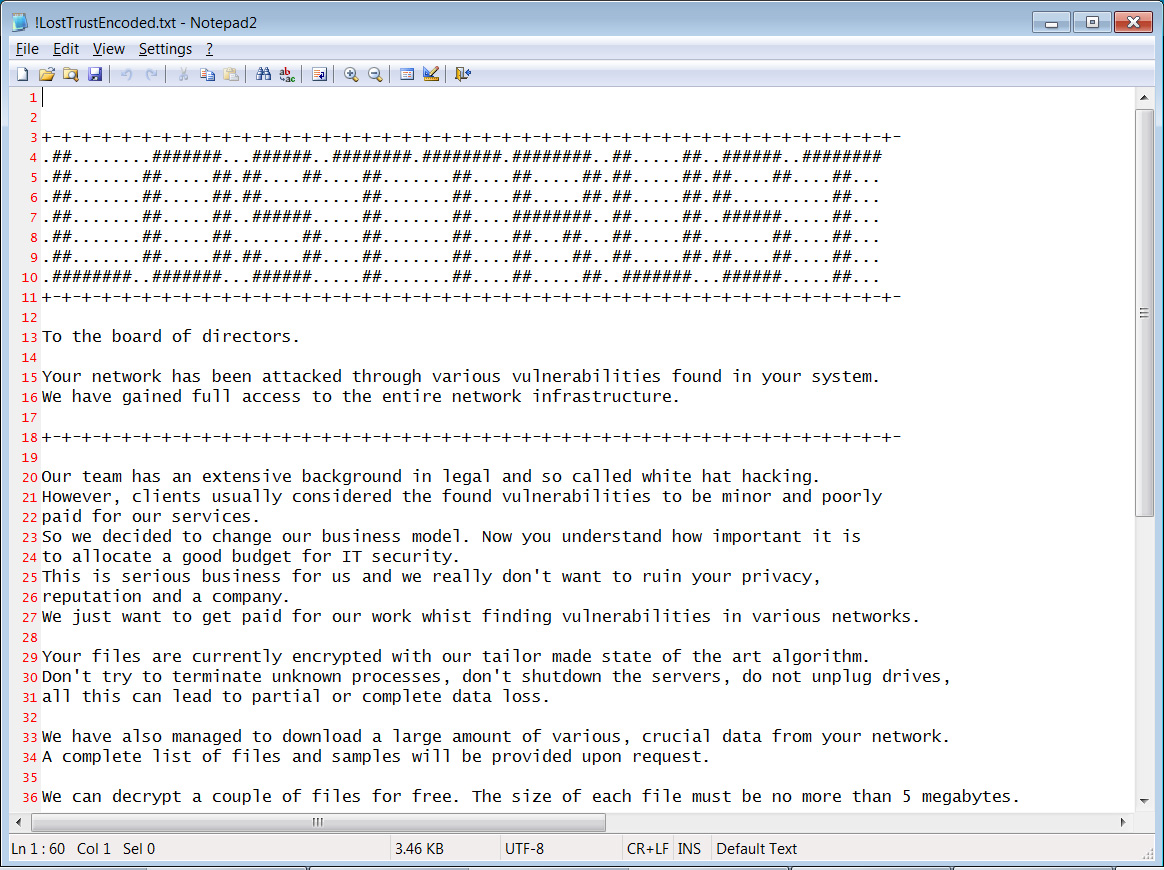
Source: BleepingComputer
These ransom notes contain information on what happened to the company’s files and include a unique link to the ransomware gang’s Tor negotiation site.
The negotiation site is bare bones, with only a chat feature allowing company representatives to negotiate with the threat actors.
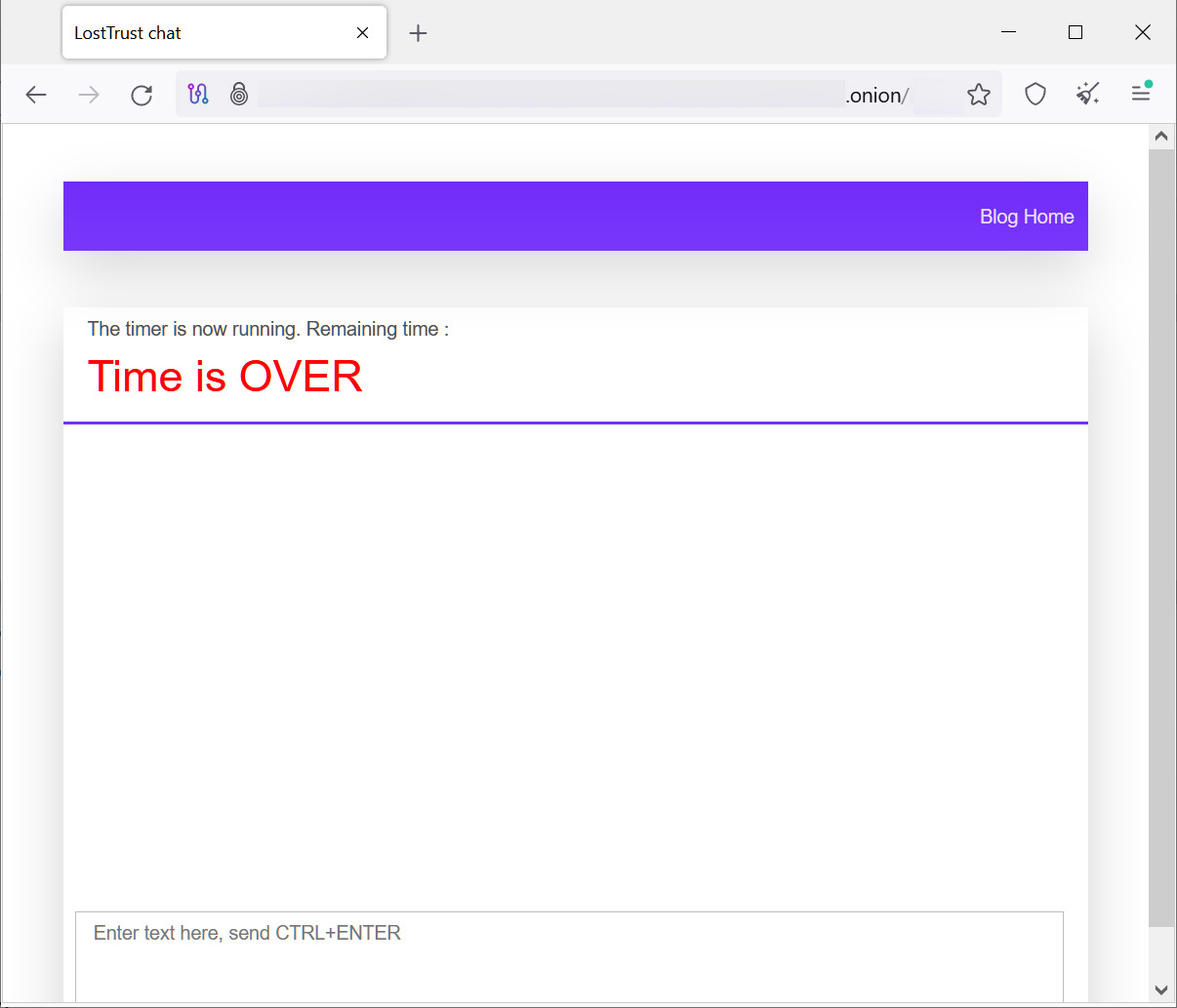
Source: BleepingComputer
BleepingComputer was told that ransom demands for LostTrust attacks range from $100,000 to millions.
Data leak site used to extort victims
Like other ransomware operations, LostTrust utilizes a Tor data breach site that is used to extort companies by threatening to leak their stolen data if a ransom is not paid.
LostTrust has 53 victims on their data leak site, with some companies already having their data leaked.
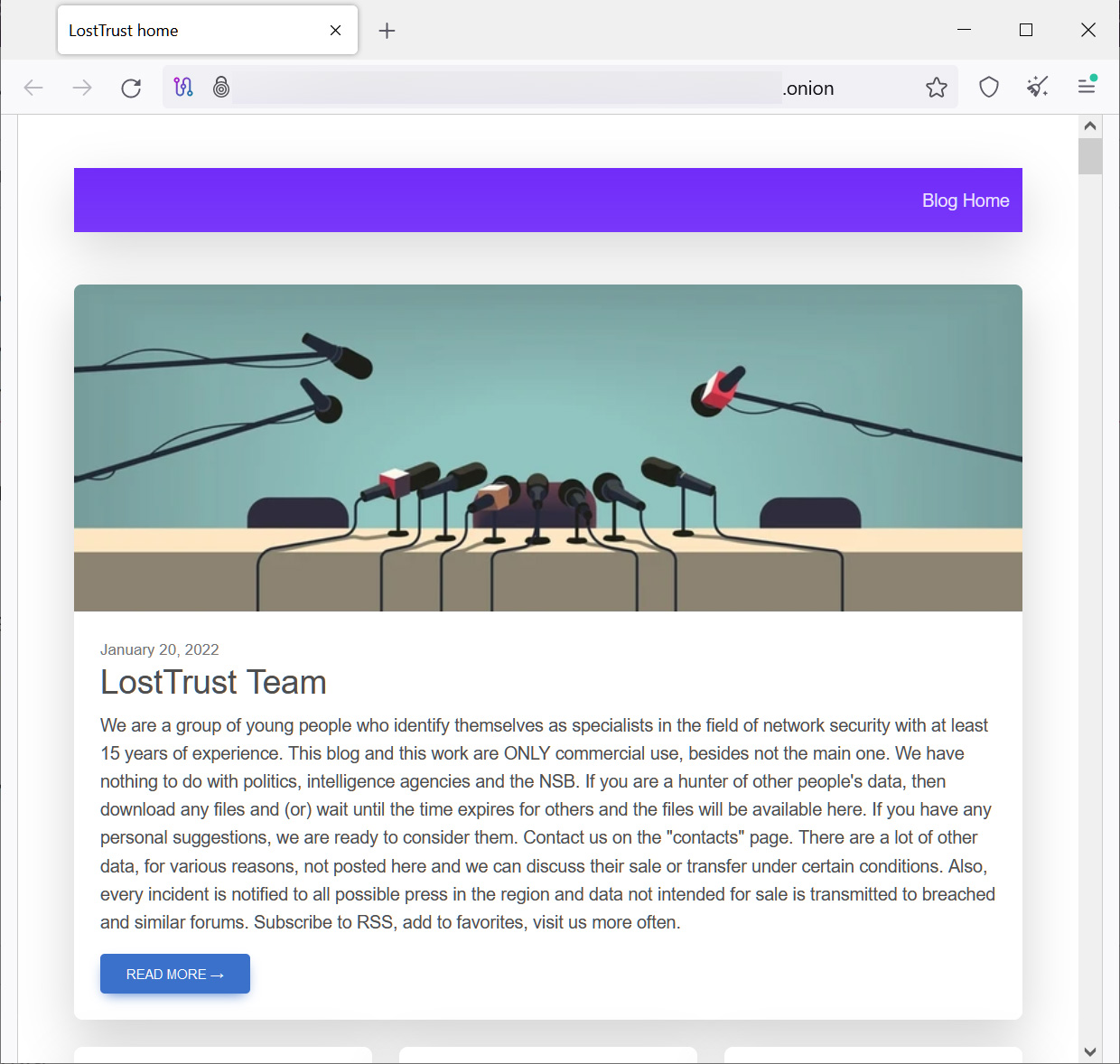
Source: BleepingComputer
At this time, it is not known if paying a ransom demand will lead to the deletion of data and a working decryptor.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![Sliver C2 Detected - 185[.]246[.]118[.]237:31337 9 Sliver C2](https://www.redpacketsecurity.com/wp-content/uploads/2024/02/Sliver-C2-300x142.jpg)
