Misconfigured Firebase Instances Leaked 19 Million Plaintext Passwords

Three cybersecurity researchers discovered close to 19 million plaintext passwords exposed on the public internet by misconfigured instances of Firebase, a Google platform for hosting databases, cloud computing, and app development.
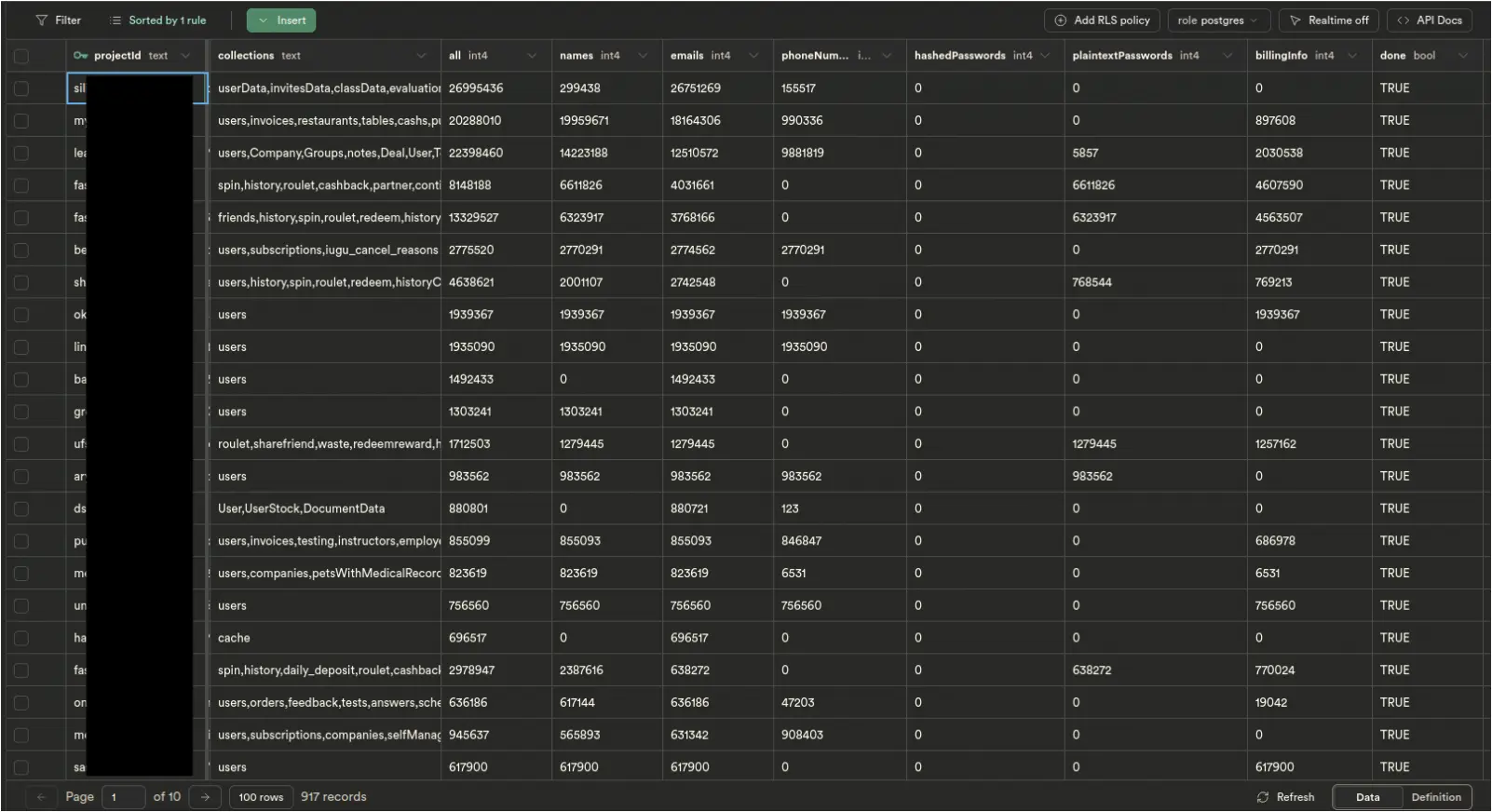
The trio scanned more than five million domains and found 916 websites from organizations that either had no security rules enabled or had set them up incorrectly.
More than 125 million sensitive user records were found, including emails, names, passwords, phone numbers, and billing information with bank details.
Millions of plaintext passwords exposed
The researchers (Logykk, xyzeva/Eva, and MrBruh) started looking on the public web for personally identifiable information (PII) exposed via vulnerable Firebase instances.
Eva told BleepingComputer that they found Firebase instances that had no security rules at all or were incorrectly configured and permitted read access to databases.
“Most of the sites also had write enabled which is bad,” Eva told us, adding that among these they also found a bank.
For each exposed database, Eva’s script, Catalyst, checked for the type of data available and extracted a sample of 100 records.
source: xyzeva
All the details were organized in a private database that offers an overview in numbers of the sensitive user information companies expose due to improper security settings:
- Names: 84,221,169
- Emails: 106,266,766
- Phone Numbers: 33,559,863
- Passwords: 20,185,831
- Billing Info (Bank details, invoices, etc): 27,487,924
For passwords, the problem gets worse because 98% of them, or 19,867,627 to be exact, are in plain text.
Eva told us that companies must have gone “out of their way to store [the password]” in plain text because Firebase has an end-to-end identity solution called Firebase Authentication specifically for secure sign-in processes that do not expose user passwords in the records.
One way to expose user passwords in a Firestore database is for the admin to create a ‘password’ field that stores the data in plaintext.
Alerting site owners
After analyzing the data from the samples, the researchers tried to warn all impacted companies of improperly secured Firebase instances and sent 842 emails over 13 days.
Although just 1% of the site owners replied, a quarter of the notified site administrators fixed the misconfiguration in their Firebase platform.
The researchers were also offered bug bounties from two site owners. However, they declined to comment on the value of the rewards, saying only that they accepted them and that they were not large.
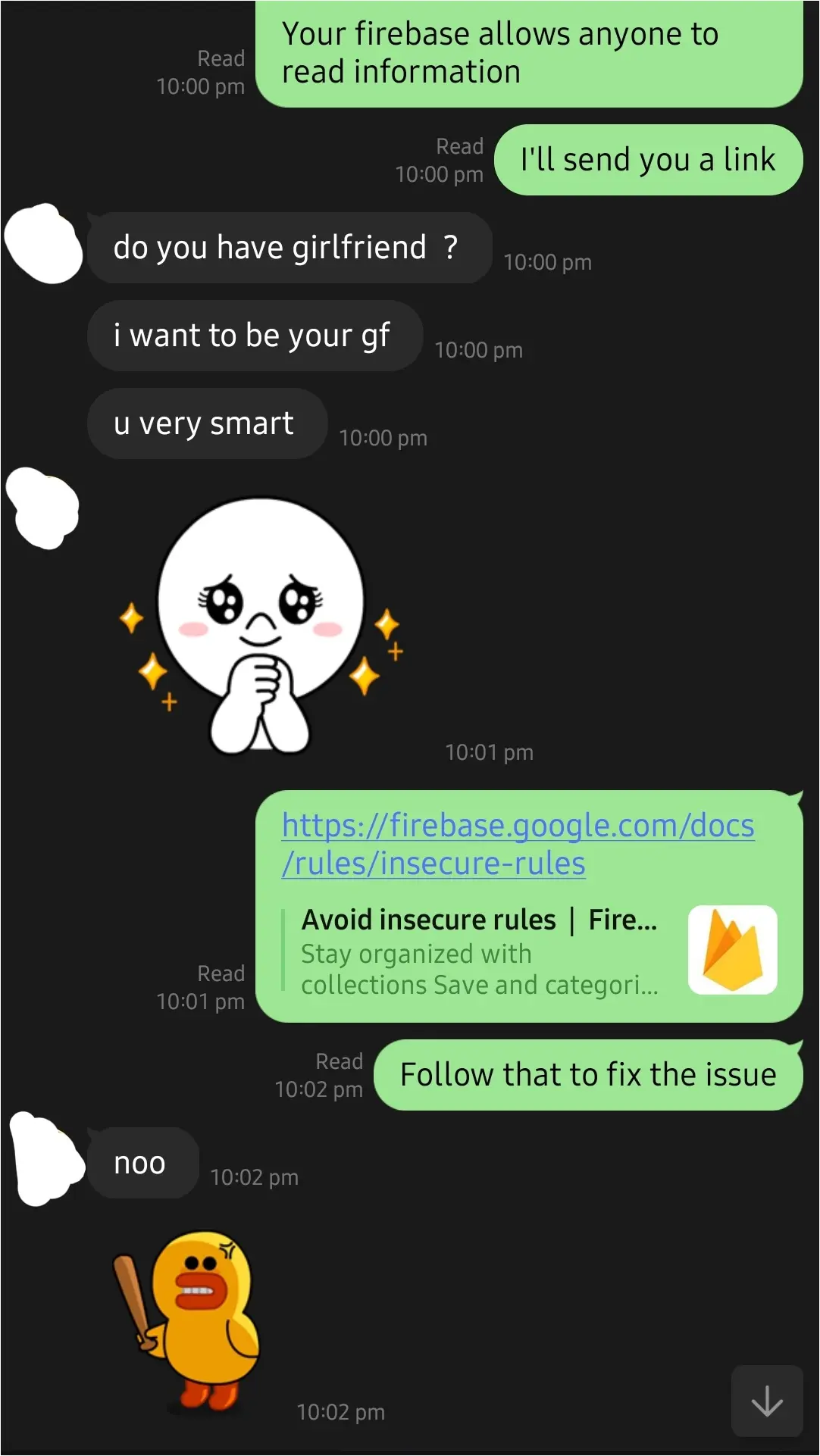
Some organizations were contacted over their customer support channel but the response was far from professional.
In the case of an Indonesian gambling network, that manages nine websites, the researchers faced mockery when reporting the problem and pointing to guidance to fix it.
source: xyzeva
Coincidentally, the same company accounted for the largest number of exposed bank account records (8 million) and plain text passwords (10 million).
According to one of the researchers, the company is bsed in Indonesia and has an annual profit of $4 million.
223 million total exposed records
Scanning the internet, parsing the raw data, and organizing took about a month and the process did not go smoothly from start to finish.
Initially, they ran the scan using a Python script built by MrBruh to check websites or their JavaScript bundles for variables in Firebase configurations.
Large memory consumption made the script unsuitable for the tasks and was replaced by a variant in Golang written by Logykk, which took more than two weeks to finish scanning the internet.
The new script scanned more than five million domains connected to Google’s Firebase platform for backend cloud computing services and application development.
To automate the check of read permissions in Firebase, the team used another script from Eva that would crawl the site or its JavaScript for access to Firebase collections (Cloud Firestore NoSQL databases).
The total number of records the researchers discovered in misconfigured databases is 223,172,248. Of these, 124,605,664 records relate to users; the rest represent data associated with organizations and their tests.
Despite the high number of exposed records, the researchers warn that the figure is conservative and the amount is likely larger.
How it all started
Scanning the internet for exposed PII from misconfigured Firebase instances is a follow-up of another project the researchers conducted two months ago, when, due to misconfiguration issues, they obtained admin and then “superadmin” permissions [1, 2] on an instance of Firebase used by Chattr, an AI-powered hiring software solution.
Chattr is used by many large fast food chains in the United States, such as KFC, Wendy’s, Taco Bell, Chick-fil-A, Subway, Arby’s, Applebee’s, and Jimmy John’s, for hiring their workforce.
While the admin role in Chattr’s Firebase dashboard allowed viewing sensitive information related to individuals trying to obtain a job in a fast food chain, the “superadmin” position gave access to a company’s account and acted on its behalf for certain tasks, including hiring decisions.
The researchers also responsibly disclosed the vulnerability to Chattr, who fixed the flaw, but no longer responded to further emails.
