New tool scans iPhones for ‘Triangulation’ malware infection

Cybersecurity firm Kaspersky has released a tool to detect if Apple iPhones and other iOS devices are infected with a new ‘Triangulation’ malware.
This malware was discovered by Kaspersky on its own network, reporting that it has infected multiple iOS devices across its premises worldwide since at least 2019.
Although the malware analysis is still underway, the cybersecurity firm noted that the ‘Operation Triangulation’ malware campaign uses an unknown zero-day exploit on iMessage to perform code execution without user interaction and elevated privileges.
This allows the attack to download further payloads to the device for further command execution and information collection.
It should also be noted that the FSB, Russia’s intelligence and security service, linked the malware to infections of high-ranking government officials and foreign diplomats.
In the original report, Kaspersky provided quite a few details on manually checking iOS device backups for possible indicators of compromise by this unknown malware using the Mobile Verification Toolkit (MVT).
However, the security firm has now released an easier-to-use, automated Triangulation scanner for both Windows and Linux.
The Triangle iOS scanner
iOS can only be analyzed as a backup, as Apple’s various security mechanisms (sandboxing, data encryption, code signing) prevent live system analysis.
Thus, users need to first back up their iOS devices following these steps depending on their operating system:
Windows:
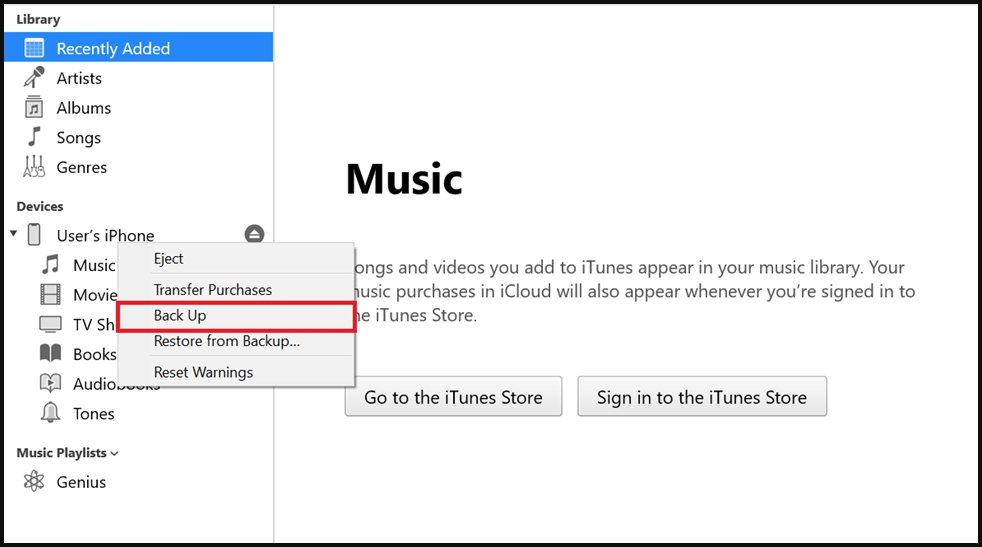
- Connect your device to a computer that has iTunes installed. Unlock your device and, if needed, confirm that you trust your computer.
- Your device should now be displayed in iTunes. Right-click on it and press “Back Up.”
- The created backup will be saved to the %appdata%\Apple Computer\MobileSync\Backup directory.

macOS:
- Connect your device to the computer and, if needed, confirm that you trust the computer.
- Your device should now be displayed in Finder. Select it and then click “Create a backup. “
- The created backup will be saved to the ~/Library/Application Support/MobileSync/Backup/ directory.
Linux:
- Install the “libimobiledevice” library.
- Connect your device to the computer and can create a backup using the “idevicebackup2 backup –full” command.
- During the backup process, enter your device passcode as requested.
The next step is to use Kaspersky’s ‘triangle_check’ scanner to analyze the iOS backups.
Kaspersky has released the scanner as binary builds for Windows and Linux and a cross-platform Python package made available through the PyPI.
Python package:
- Get ‘triangle_check’ from PyPI using the following command: python -m pip install triangle_check
- Alternatively, the tool can be built from GitHub by running:
- git clone https://github.com/KasperskyLab/triangle_check
- cd triangle_check
- python -m build
- python -m pip install dist/triangle_check-1.0-py3-none-any.whl
After that, use this command to launch the tool: python -m triangle_check path to the created backup.
Windows binary:
The Windows binary is available through Kaspersky’s public GitHub repository. To use it, follow these instructions:
- Download the triangle_check_win.zip archive from the GitHub releases page and unpack it.
- Launch the command prompt (cmd.exe) or PowerShell.
- Change your directory to the one with the unpacked archive (e.g., cd %userprofile%\Downloads\triangle_check_win).
- Launch triangle_check.exe, specifying the path to the backup as an argument (e.g., triangle_check.exe “%appdata%\Apple Computer\MobileSync\Backup\00008101-000824411441001E-20230530-143718”).
Linux binary:
The Linux binary is available through Kaspersky’s public GitHub repository. To use it, follow these instructions:
- Download the triangle_check_win.zip archive from the GitHub releases page and unpack it.
- Launch the terminal.
- Change your directory to the one with the unpacked archive (e.g., cd ~/Downloads/triangle_check_linux).
- Allow the utility to be executed with the “chmod +x triangle_check” command.
- Launch the utility, specifying the path to the backup as an argument (e.g., ./triangle_check ~/Desktop/my_backup/00008101-000824411441001E-20230530-143718).
When launched and pointed to the iOS backup path, the triangle_check tool will output one of the following scan results:
- DETECTED: It means that the “Operation Triangulation” malware has infected the device beyond doubt.
- SUSPICION: The scanner has found some indicators of compromise pointing to a likely infection, but there’s not enough evidence to support a conclusive result.
- No traces of compromise were identified: The scanner has not detected any signs of compromise for the particular malware family.
Note that the above results, especially the negative ones, may not be fully trusted or treated as definitive assurances that the device is clean.
As the malware’s analysis is ongoing, additional indicators of compromise or even a newer variant that infects more recent iOS releases may be discovered later.
A targeted malware campaign
Typically, espionage-driven malware distribution campaigns like “Operation Triangulation” target specific individuals or companies rather than the wider population, so most people using the checker should get a clean result.
However, Kaspersky’s tool could be handy for people holding critical roles in important organizations, individuals at heightened risk of state-sponsored espionage, and those working in companies or services that act as information hubs.
Currently, the exact origin of the malware and the orchestrators of Operation Triangulation remain unknown; hence, the targeting scope and victimology have not been determined.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.








![Sliver C2 Detected - 89[.]23[.]117[.]246:31337 12 Sliver C2](https://www.redpacketsecurity.com/wp-content/uploads/2024/02/Sliver-C2-300x142.jpg)
