Nitrogen Shelling Malware From Hacked Sites
Nitrogen is the name given to a campaign and associated malware that have been distributed via malicious search ads. Its signature move is using Python and DLL side-loading to connect to the attacker’s command and control server.
In this blog post, we look at a recent Nitrogen campaign and specifically at how the initial payload is being served onto victims. The threat actors seem to have a preference for hosting their payloads on compromised WordPress sites, many of which are already hacked with malicious PHP shell scripts.
We also review the connection between malvertising and ransomware in the context of increased web-based attacks.
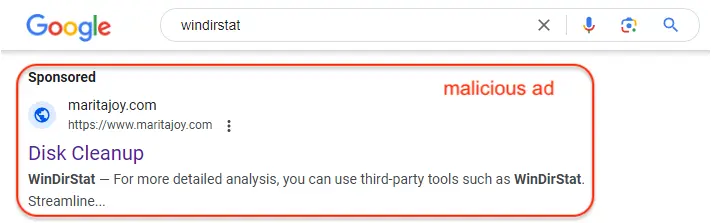
Malicious ads leads to fake WinDirStat site
We are tracking several different malvertising campaigns, which we typically categorize based on the payloads they deliver. However, we also sometimes see overlap in the criminal infrastructure and, more interestingly, in the malicious ads themselves.
The ads are displayed via Google searches for popular search terms related to programs used by IT and system administrators. The malvertiser behind this campaign like to register expired domain names that have a previous history, which helps them to bypass certain security checks that involve looking at the age of a domain name.
The first step upon clicking on the ad consists of filtering visitors. If it doesn’t like your IP address or other client-side setting, it will display a fake page. The content looks like it was generated via Chat-GPT or some other LLM.
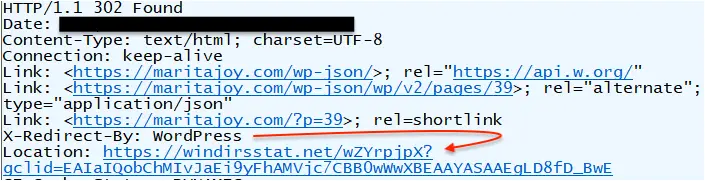
Real victims will instead be served a 302 redirect to a decoy site at windirsstat[.]net:
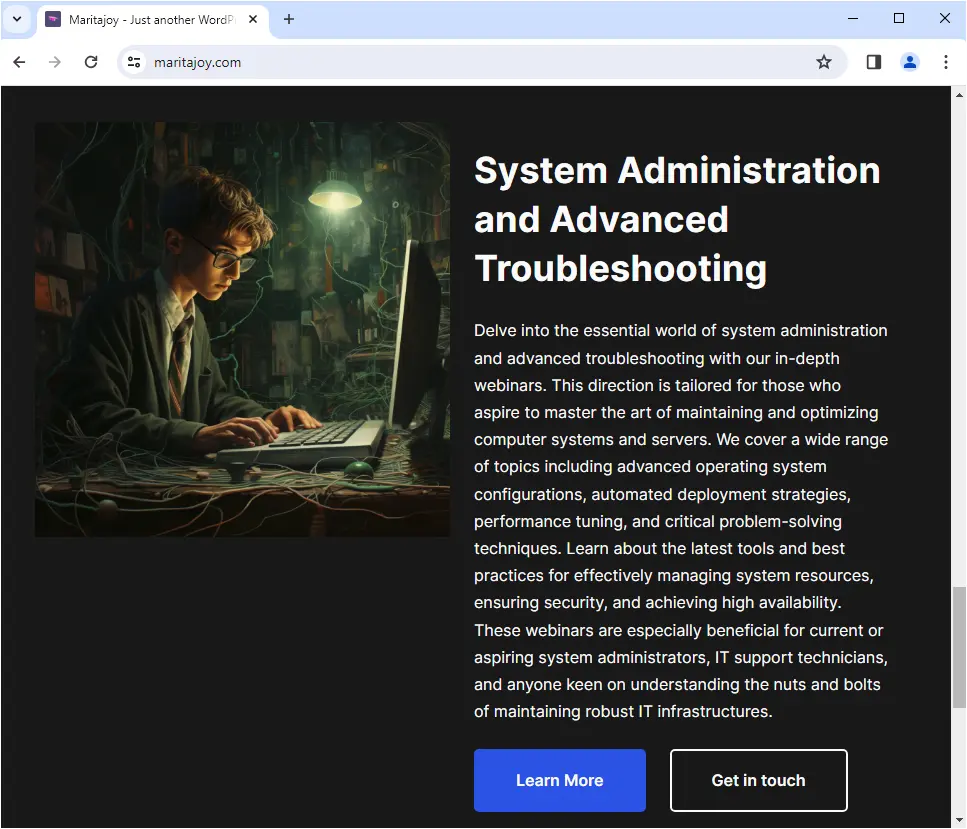
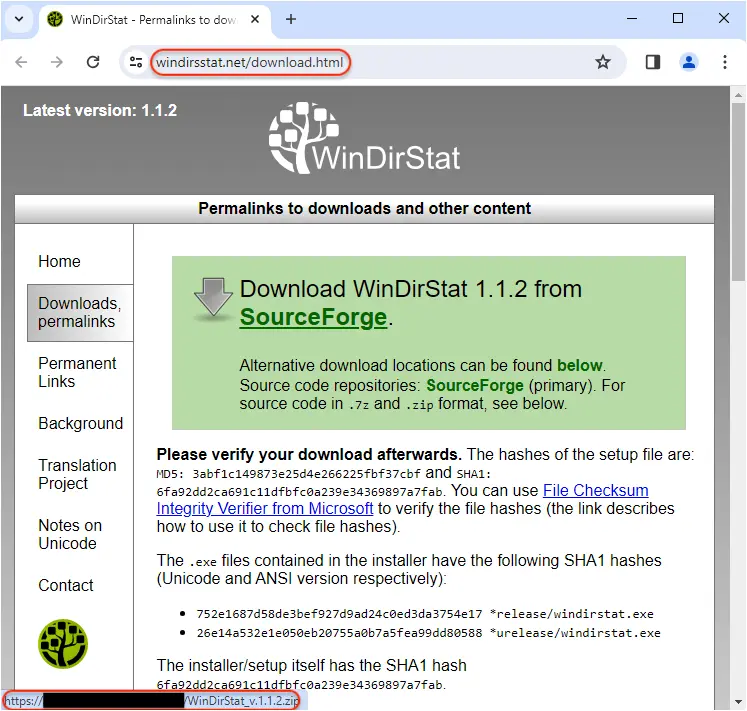
The page is designed to look identical to the real website except for the download link which points somewhere else.
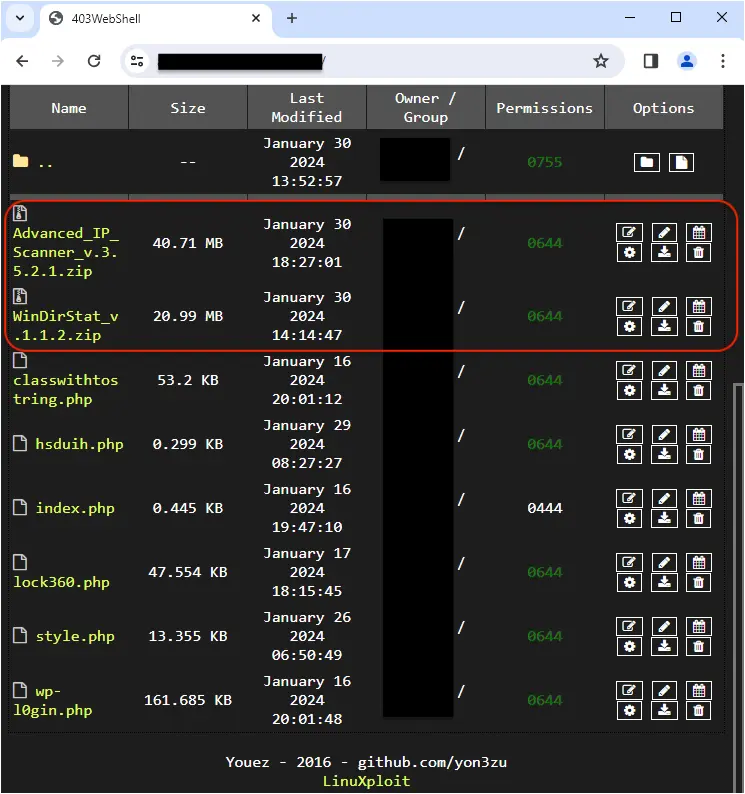
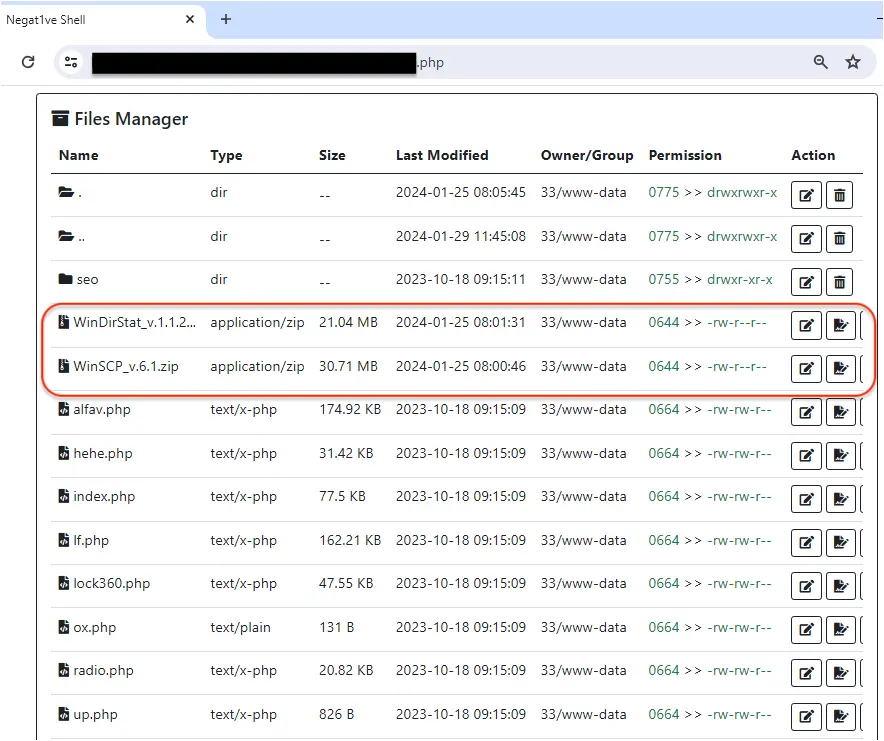
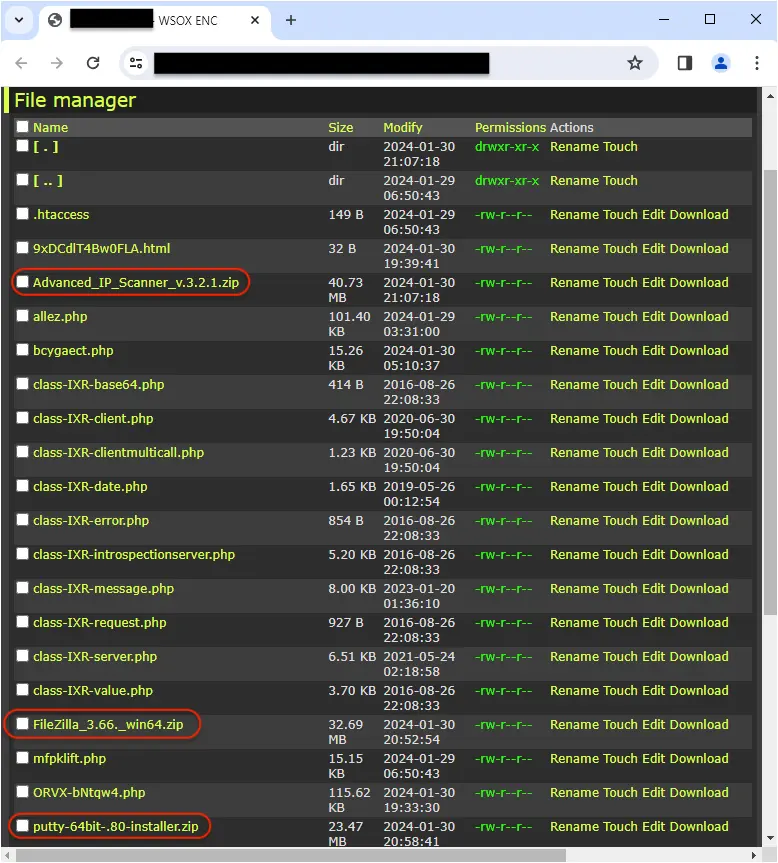
Compromised sites
The threat actor is using a number of hacked sites to host their malicious payloads which they regularly rotate through. This is not a new technique, but it is yet odd to see the fake installers cohabit with various web shells.
In fact, anyone could easily change the files or even delete them. Here, we’re simply observers and looking at the file managers that are open on the internet.
Payload
Nitrogen uses DLL side-loading via a signed executable to launch its payload:
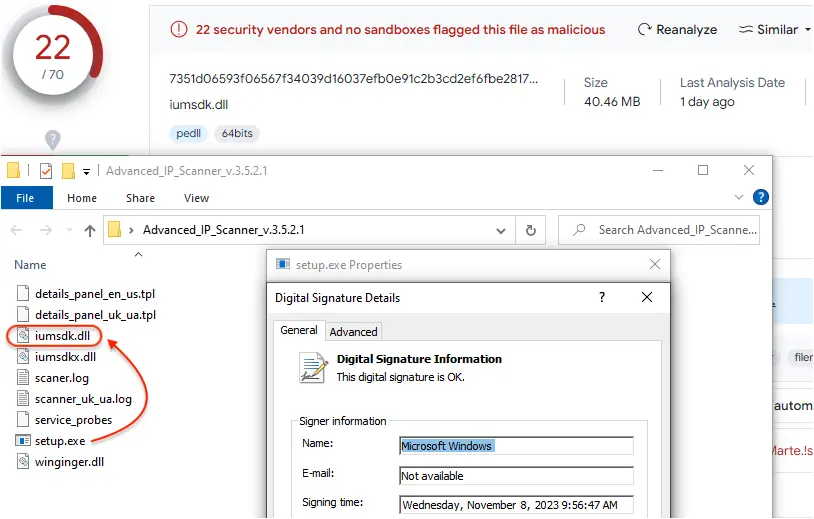
It then proceeds with running Python from a newly created folder under %appdata%:
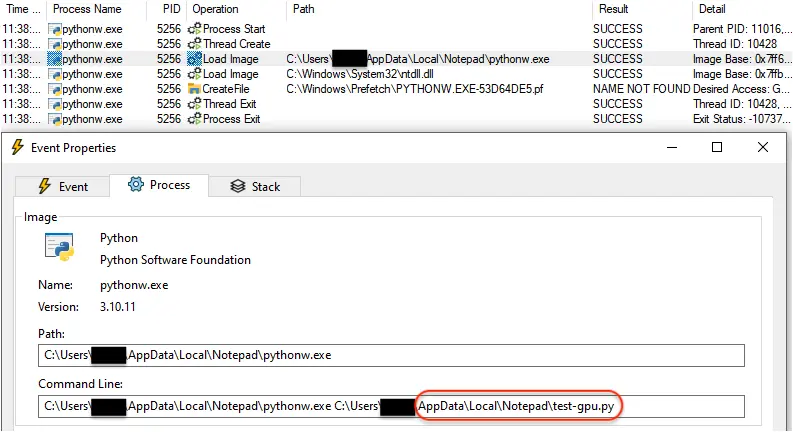
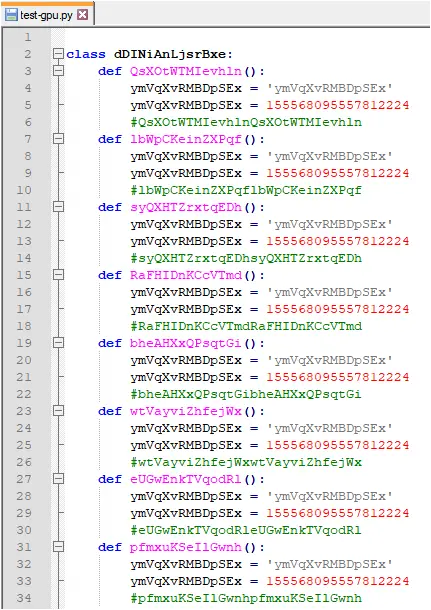
The Python file it executes is heavily obfuscated:
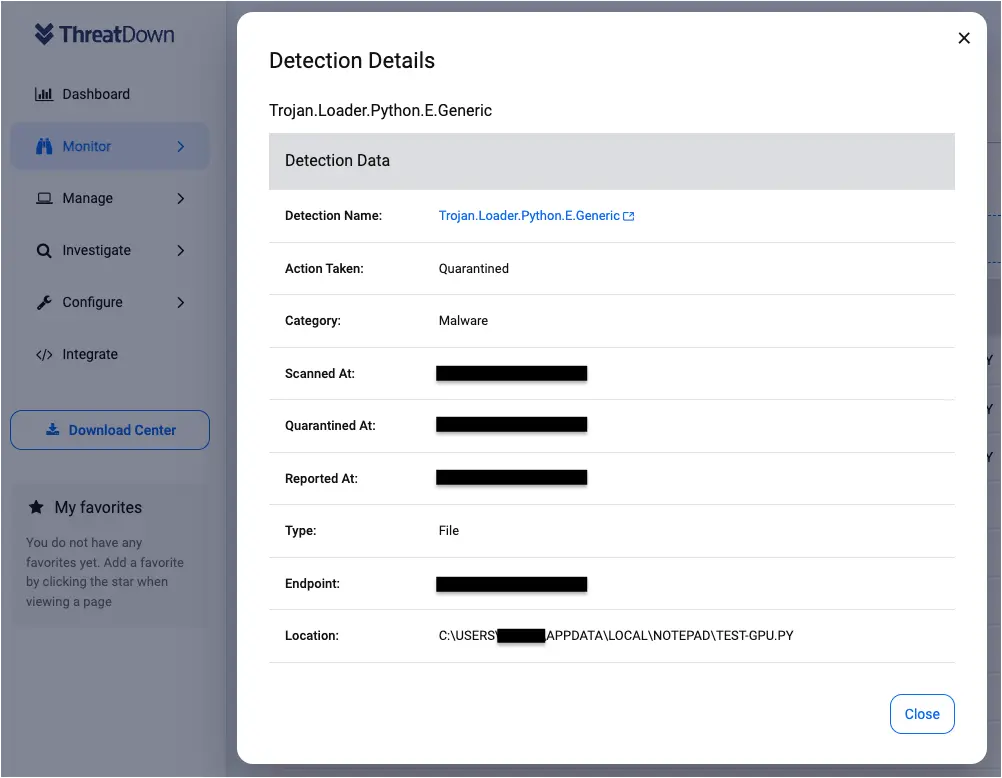
ThreatDown will detect this malicious activity and quarantine the malicious Python file:
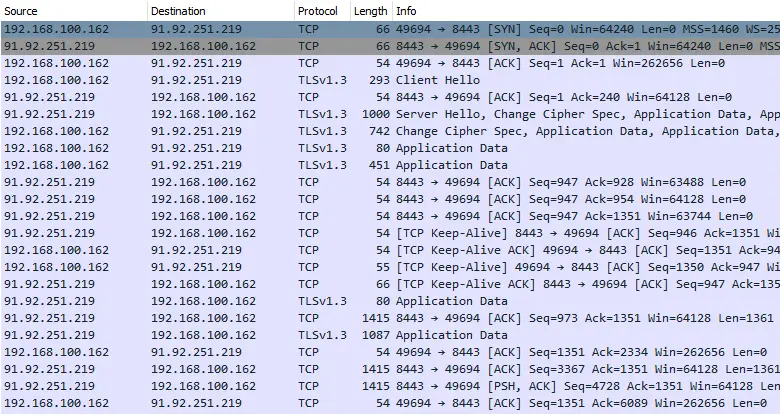
Blocking the payload at this step is crucial as it is the point where it will otherwise contact its command and control server (C2):
In recent Zip installers for Nitrogen, we noticed two files likely related to their control panel. It’s worth noting that one of them is in Ukrainian language:
Victims are added to the attackers’ control panel for further processing. The threat actors will need to cleanup their database to remove uninteresting entries such as those generated by malware sandboxes and researchers. The remaining victim can then be divided into a team of specialists that will use post exploitation tools to further gather information and compromise the network, before launching additional payloads.
Protecting your business from malicious ads
Threat actors have been using online ads as a delivery vector for malware heavily since late 2022. There is a particular segment of the market related to software downloads and in particular those used in an IT or corporate environment.
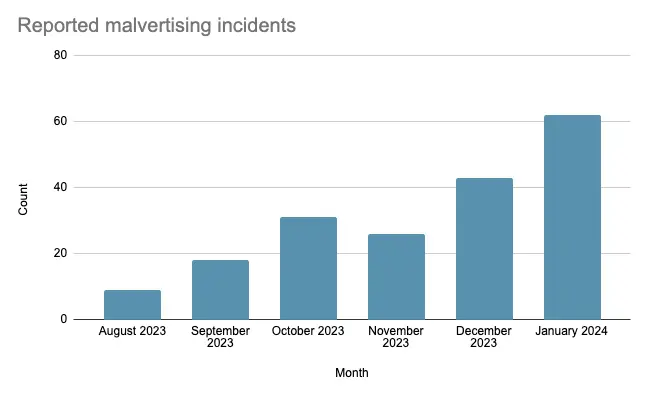
Based on our own stats, we have been seeing a steady rise in reported incidents since summer 2023 with some of the major players distributing FakeBat, PikaBot, Carbanak, Nitrogen, NetSupport RAT, or Atomic Stealer.
What makes campaigns such as Nitrogen a serious threat for businesses is their known connection with ransomware. The threat actors who gain access to a compromised machine deploy adversary emulation framework tools such as Sliver before dropping ransomware, namely ALPHV/BlackCat.
Many businesses are not adequately protected when it comes to malicious ads. This is typically reflected in the tools and security software installed on endpoints, which will often focus on spam and phishing emails.
Threat actors are well aware of this, and they have been using online ads as a delivery vector for malware heavily since late 2022. Based on our own stats from tracked incidents, we have been seeing a rise in reported incidents since summer 2023.
ThreatDown protects your networks thanks to its web-based and malware blocking features. Being able to block the infrastructure used by criminals to funnel traffic from ads is critical to avoid malware even landing on endpoints.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![GoPhish Login Page Detected - 54[.]66[.]160[.]126:443 16 gophish](https://www.redpacketsecurity.com/wp-content/uploads/2024/04/gophish-300x90.png)

